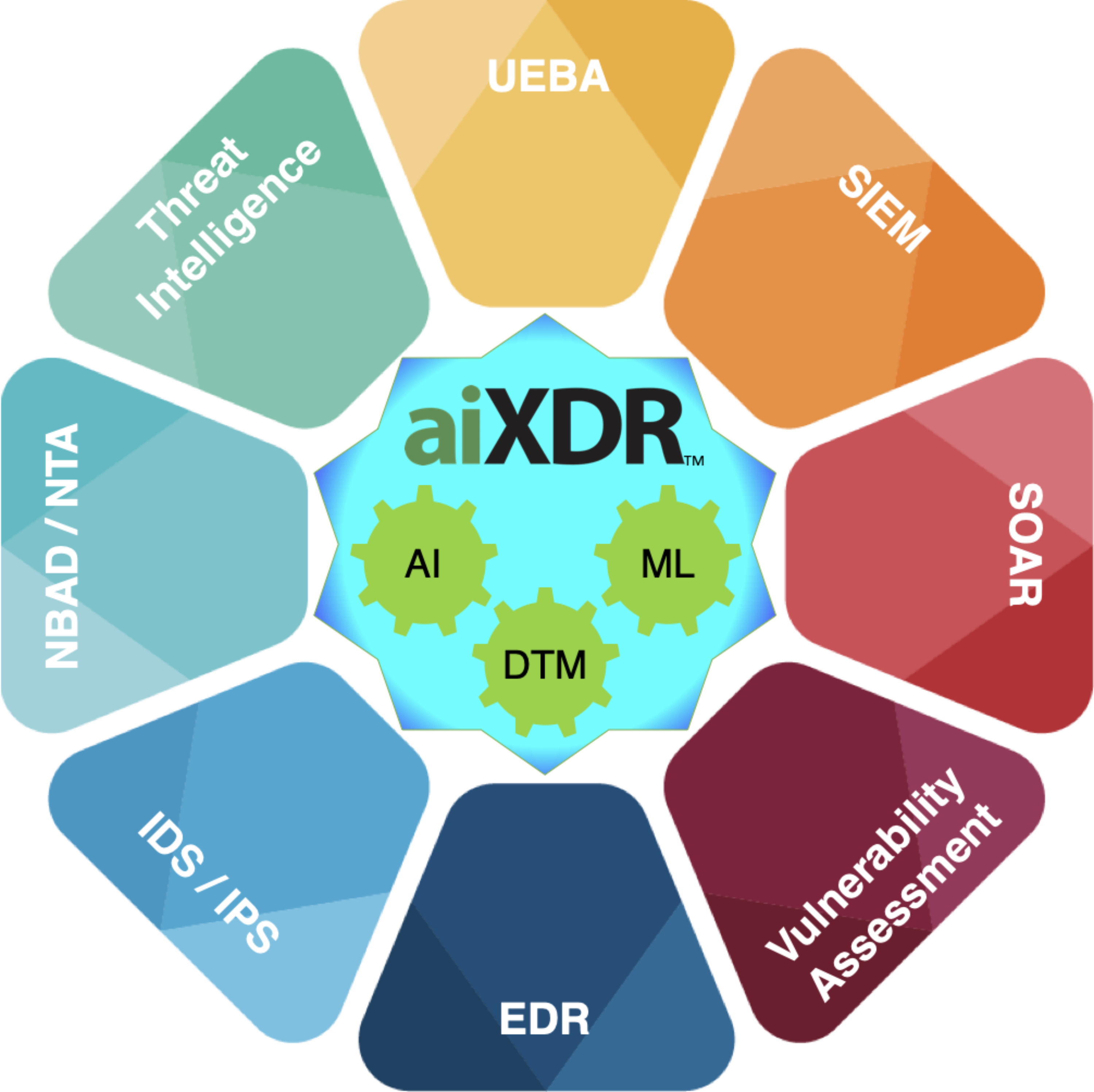
End-to-end Cybersecurity with aiXDR™
Stay Vigilant, Stay Ahead of Your Adversaries.
When it comes to safeguarding digital information, IT assets and business data, IT organizations often contend with quasi-normal state, forced by the lack of deep composite insights from endpoints, servers, firewalls, users, entity behaviors, network traffic, vulnerabilities and threat intelligence.
Secure your final frontiers – whether in the remote workplace, in the cloud, in the office or in transit – with Seceon aiXDR.
Draw upon insights rendered by razor-sharp analytics, guided by AI and ML.
In the evolving context of remote workplaces and sophisticated attacks, any weakness could play into the hands of adversaries.
- Malware downloaded from malicious website or spammed email
- Compromised Credentials of endpoint users through brute-force attacks
- Use of VPN browsing to access torrent files goes unmonitored
- Business and Privacy Protected Data Leakage by employee
- Use of Public Wi-fi for business applications using sensitive data
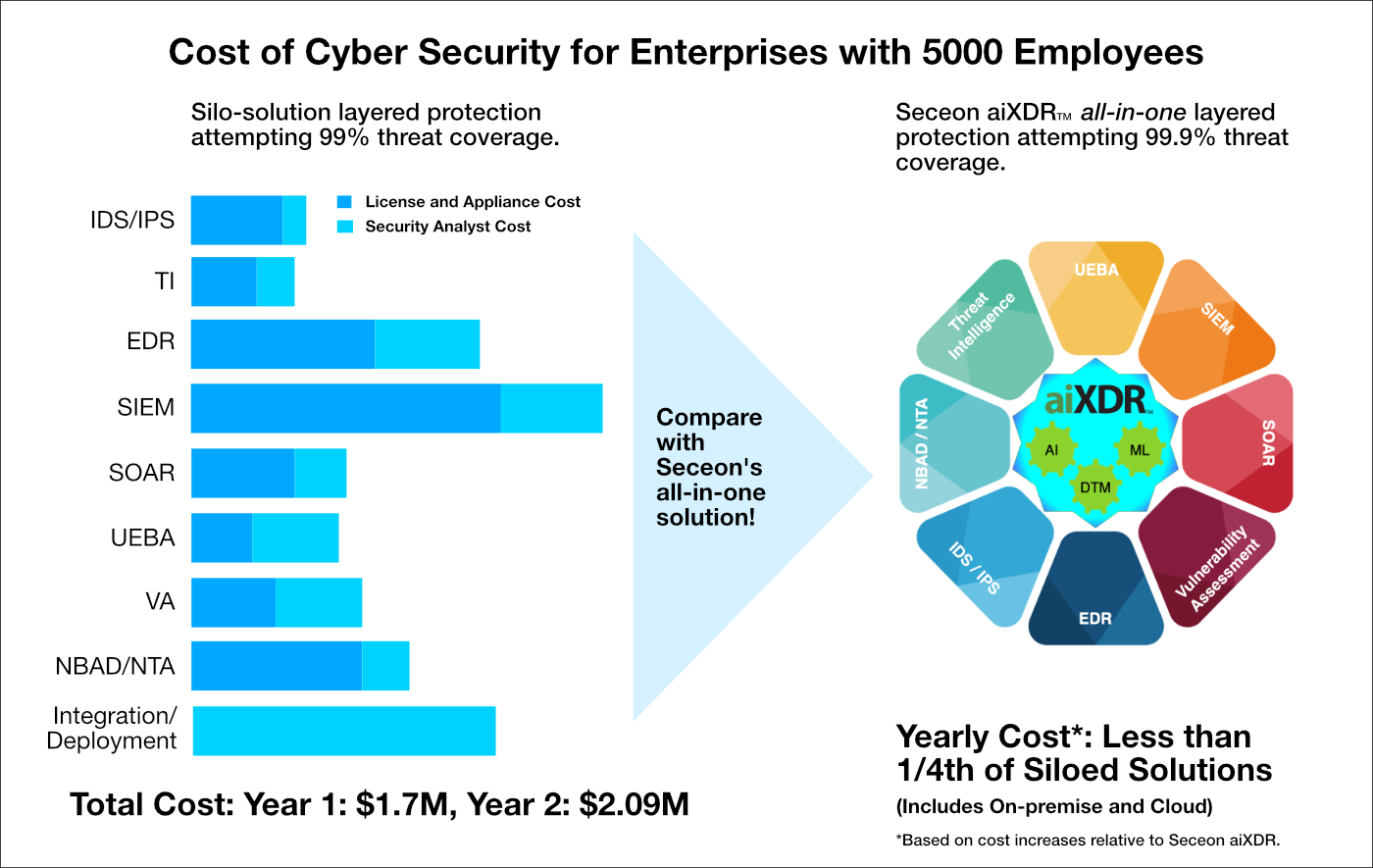
Merely relying on any particular layered protection like EDR, IDS/IPS, SIEM, SOAR or Network Security will not provide adequate coverage for the critical assets that your business relies on. Seceon’s aiXDR is a fusion of all these protective layers built organically with the speed of real-time analytics, defence in-depth oversight and dynamically adaptive threat models guided by Artificial Intelligence.
Seceon’s aiXDR takes grey and white spaces out of the cyber security canvas, leaving nothing to guesswork, abandonment or fate - making it a truly “One Stop Shop” for multi-layered protection against threats, attacks, compromises and exploits.
Comprehensive Security For Your Digital Assets
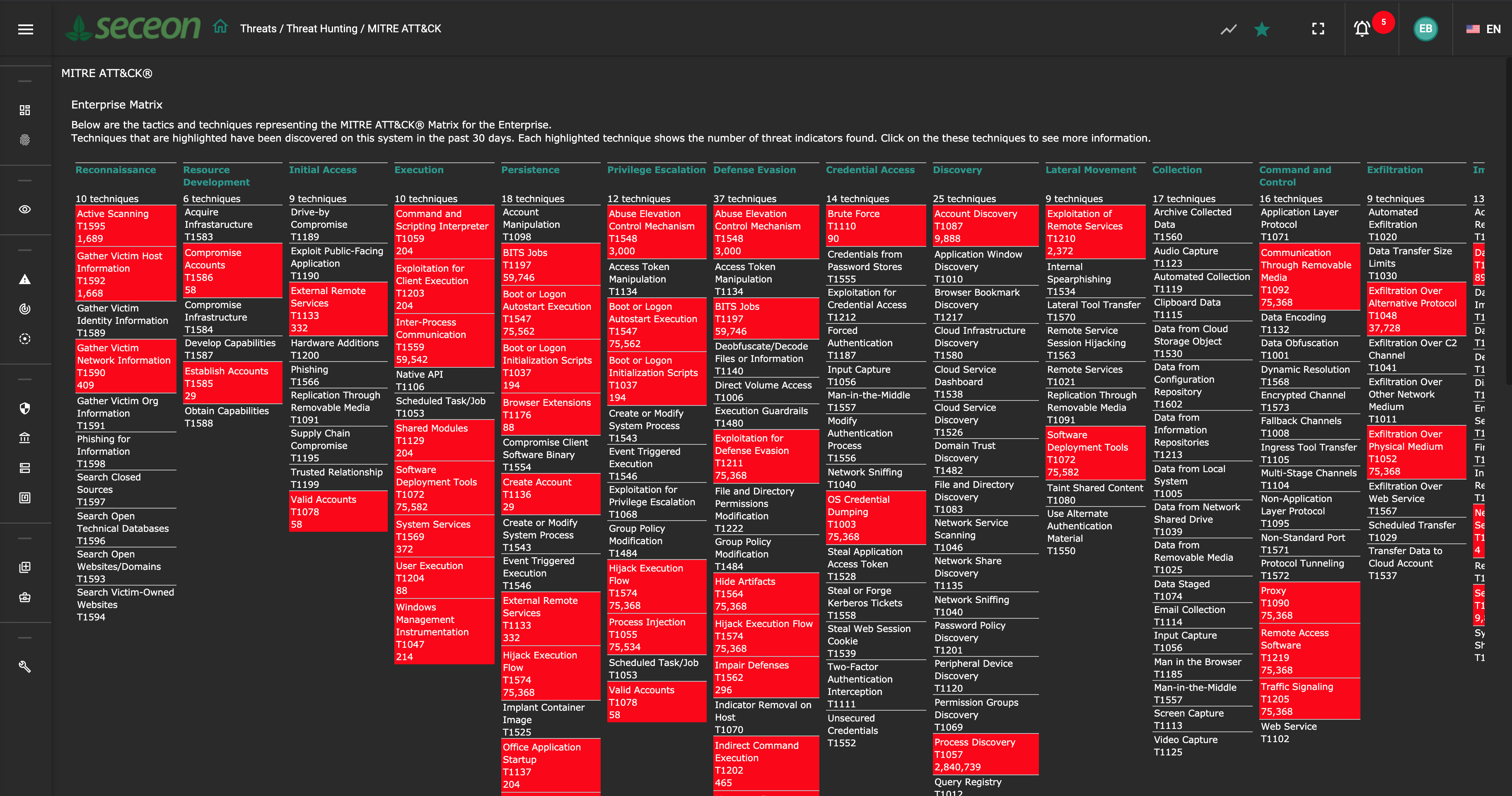
Rest assured with assimilated threat indicators across IT, OT and IoT, contextually enriched with Threat Intelligence, Behavioral Anomalies and Vulnerability Assessment.
Rich and Pertinent Evidence Derived From Various Sources
Uncover evidences of suspicious process, harmful executable, evasive tactics, recon activities and more through combination of lightweight agents and agentless technologys.
Powerful AI, ML And DTM To Preempt Incidents
Reap the benefits of Machine Learning, Artificial Intelligence and Dynamic Threat Models as alerts are generated preemptively with confidence scores.
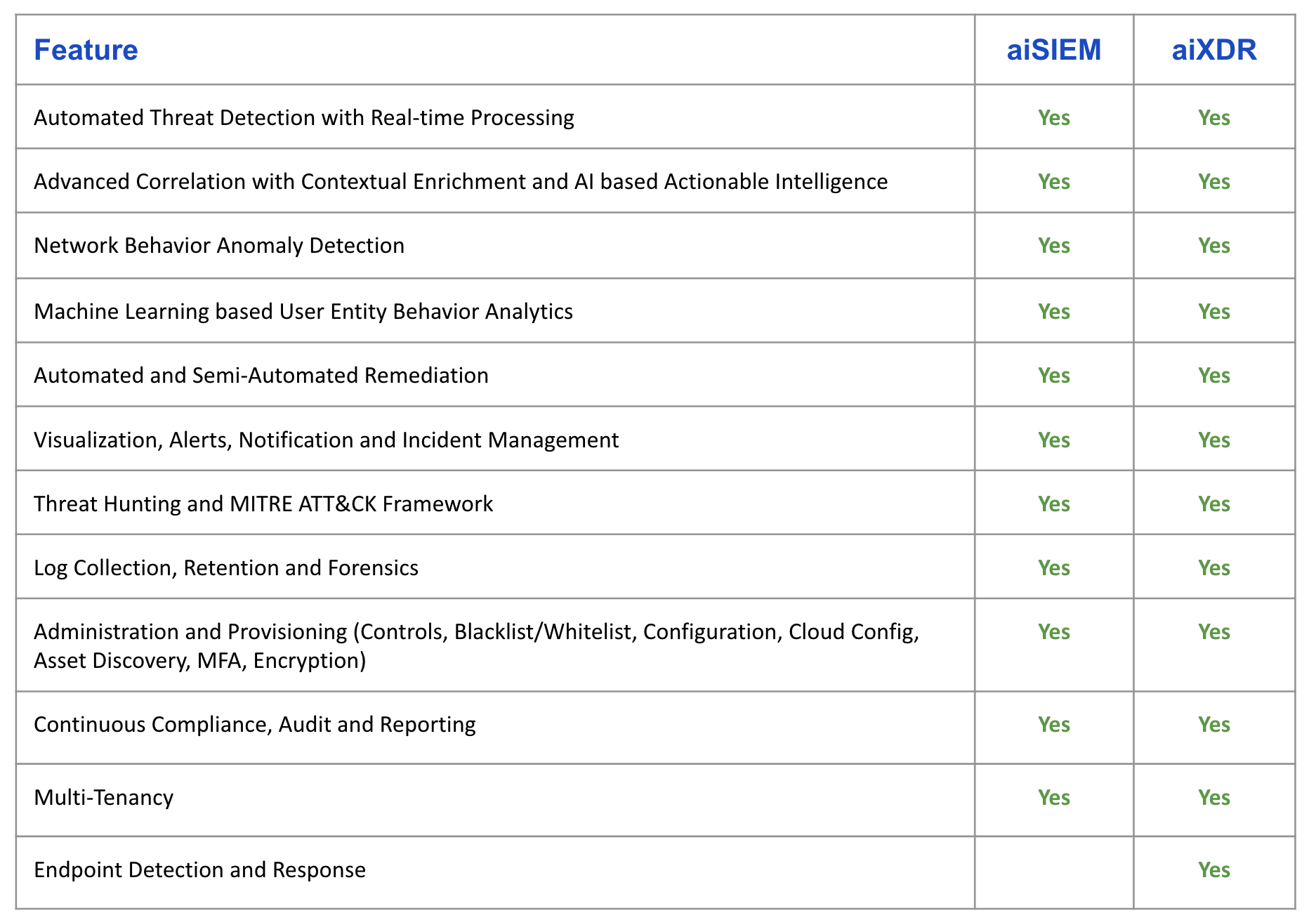
Product Feature Comparison