Seceon replaces manual tuning, expensive ingestion pricing, and scattered point tools with a single unified AI-driven platform that delivers faster, more accurate detection, fewer false positives, and dramatically lower TCO.
Compare SIEM
































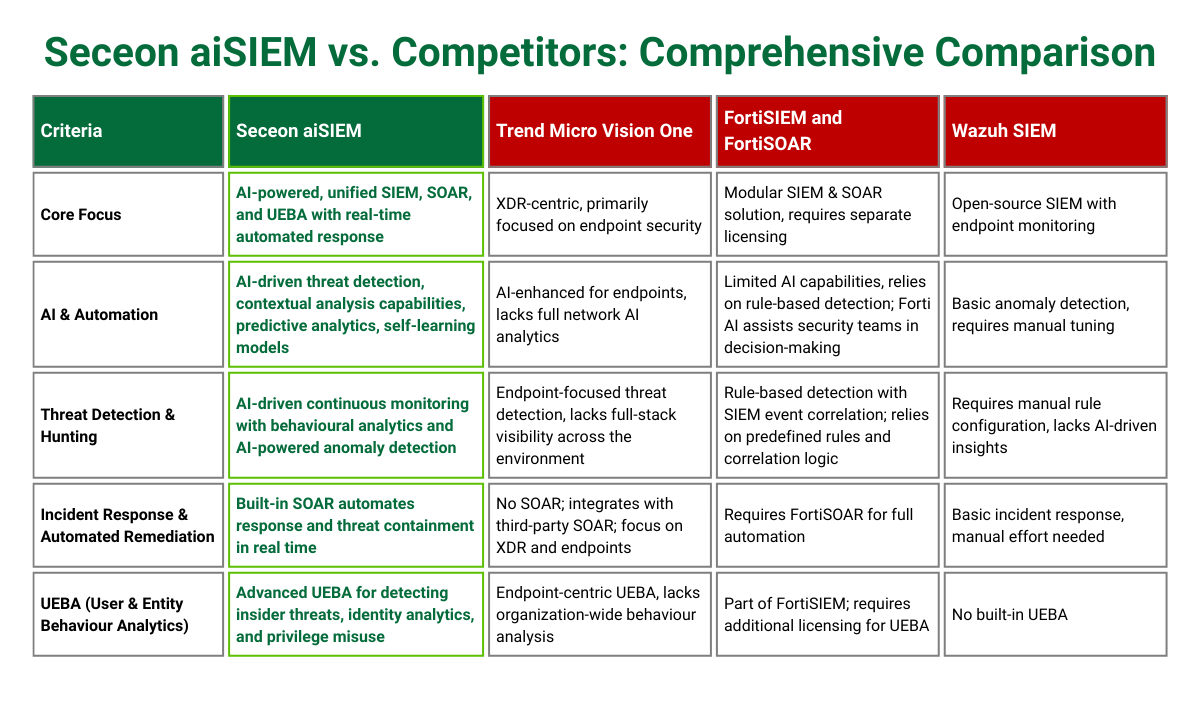
See why Seceon's unified native platform outperforms industry leaders

Splunk is a market leader in SIEM, but when it comes to building a complete security platform, you're forced into a multi-vendor nightmare. SOAR comes via partnerships, integrations are complex, and costs spiral.
| Seceon Solution | Splunk Challenges |
|---|---|
| Single unified platform (SIEM + SOAR + UEBA + XDR + NDR) | Multi-vendor stack complexity |
| 40-60% lower TCO with consolidation | High costs at scale |
| Cloud-ready, deploy in minutes | Long deployment cycles |
| Unified threat chains across domains | Fragmented visibility |
| Native SOAR with AI automation | Limited automation |
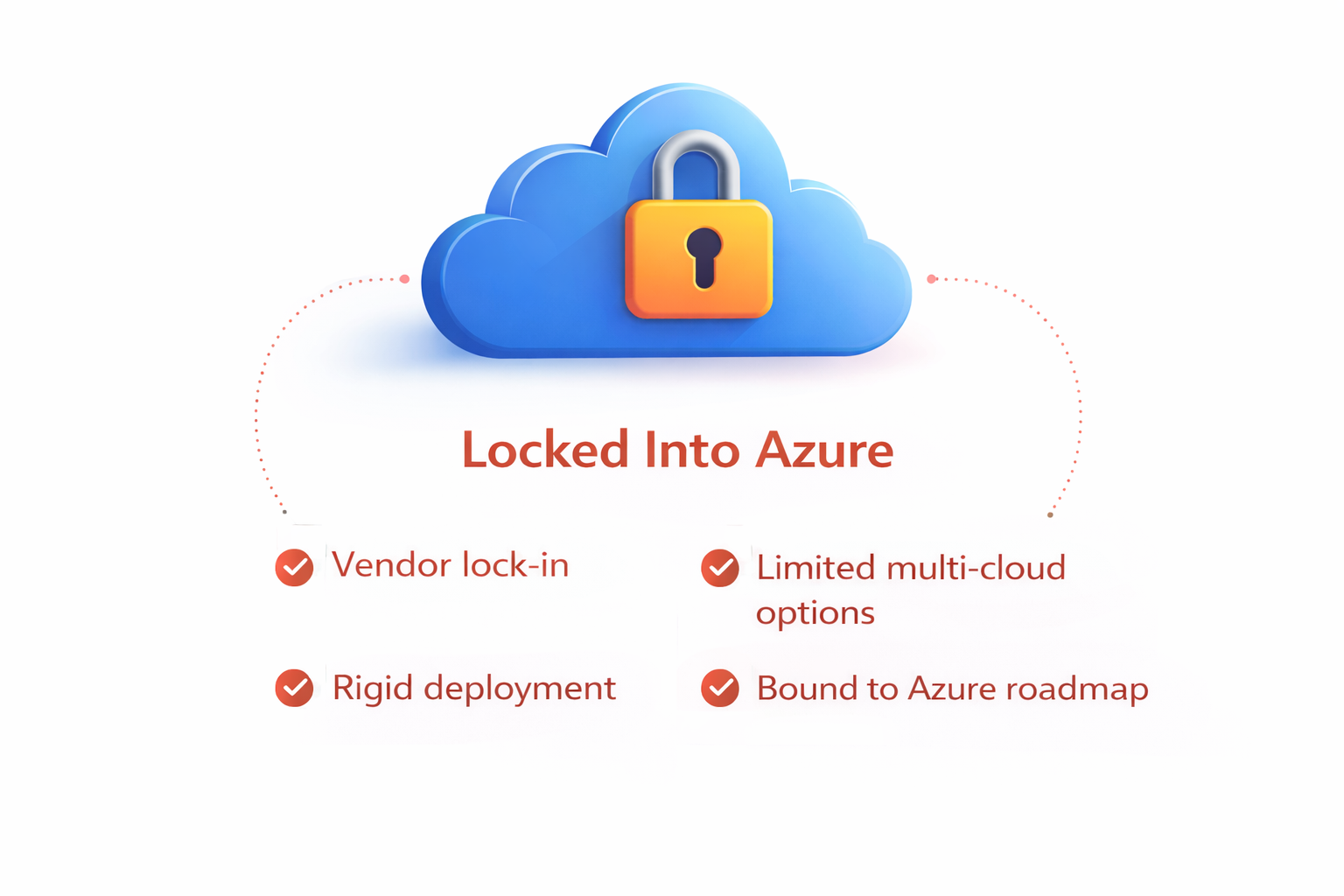
Microsoft Sentinel is powerful within Azure, but if you use AWS, GCP, or hybrid clouds, you're at a disadvantage. You're bound to Azure's roadmap and can't easily move your security stack if needs change.
| Seceon Solution | Sentinel Challenges |
|---|---|
| Cloud agnostic (AWS, Azure, GCP, on-premise) | Azure lock-in limits multi-cloud options |
| No lock-in, deploy anywhere freely | Vendor lock-in reduces flexibility |
| Works with any EDR/NDR tool | Dependent on Microsoft Defender |
| Better economics across clouds | Higher multi-cloud operating costs |
| Native multi-cloud & hybrid support | Limited hybrid deployment support |
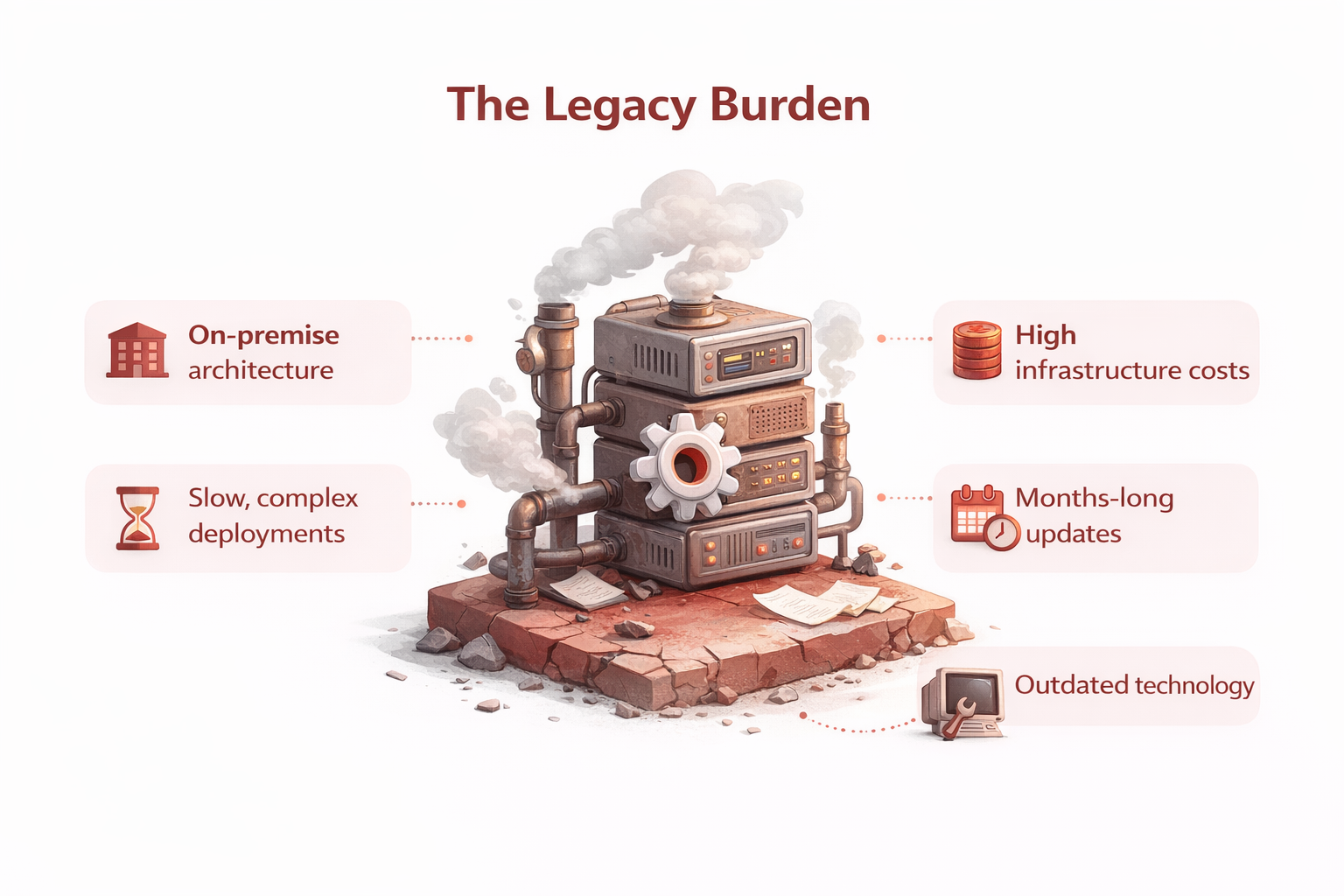
QRadar pioneered SIEM, but its on-premise first architecture shows its age. Complex deployments, limited UEBA, and operational overhead make it expensive to run and difficult to scale for modern cloud-native security.
| Seceon Solution | QRadar Challenges |
|---|---|
| Cloud-native, built for modern scale | Legacy on-premise architecture |
| Deploy in minutes, ready to use | Months-long deployments |
| Native UEBA & threat hunting built-in | Limited UEBA, needs integration |
| Lower costs with managed cloud | High infrastructure costs |
| Continuous updates & innovation | Slow innovation, infrequent updates |
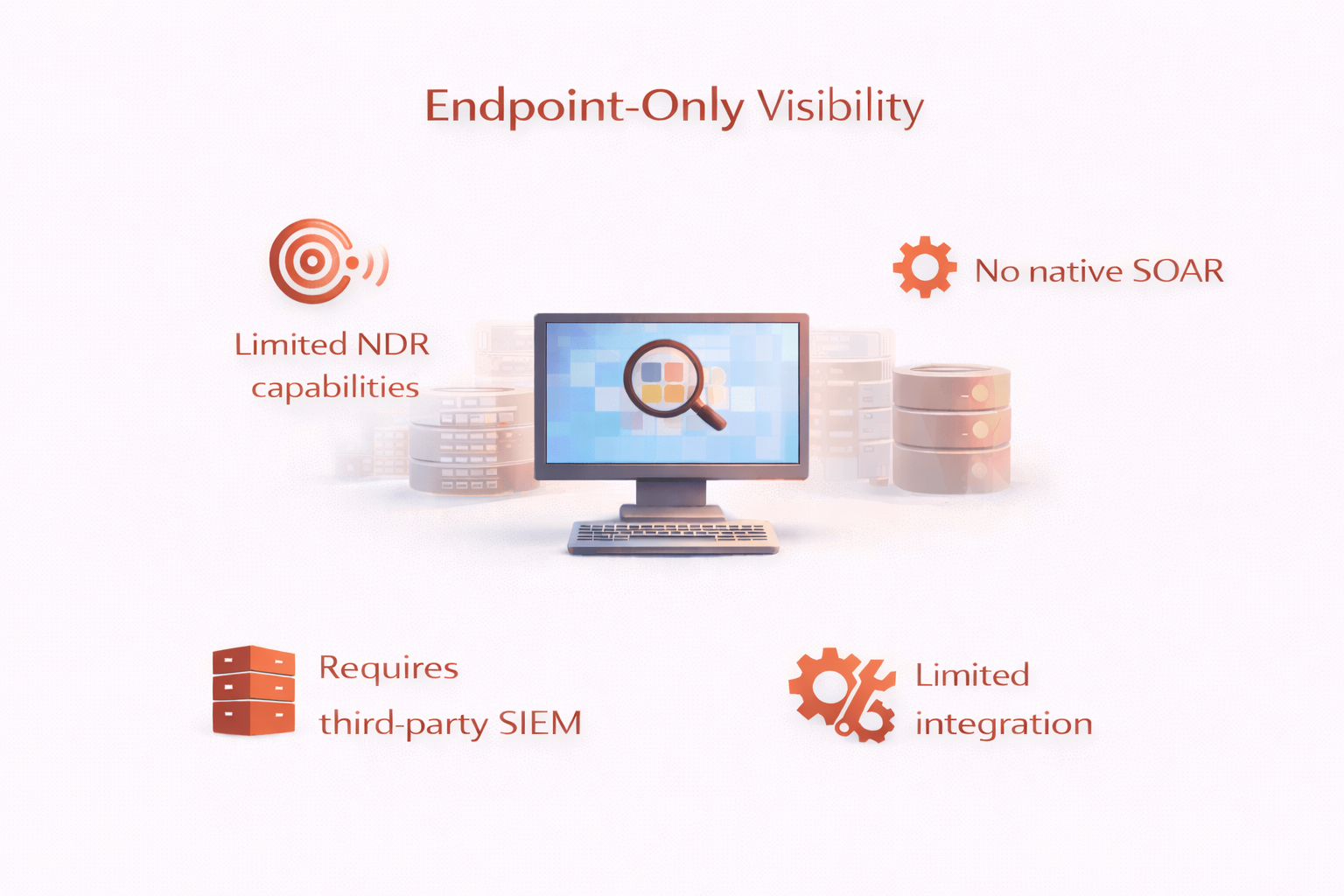
CrowdStrike excels at endpoint protection, but when it comes to SIEM, it's still tied to an EDR-centric model. Detection is limited to what the endpoint sees, third-party integrations are constrained, and full functionality requires buying into their entire Falcon suite.
| Seceon Solution | CrowdStrike Challenges |
|---|---|
| Full-spectrum visibility across all domains | Endpoint-only visibility |
| Enterprise SIEM with 700+ integrations | Lacks SIEM & log management |
| Native NDR for network threat detection | Limited NDR capabilities |
| Native SOAR + advanced UEBA | No native SOAR |
| Works with any EDR, no lock-in | Requires third-party SIEM |

Palo Alto's XSIAM is built on stitching together multiple platforms. While comprehensive, it requires managing separate modules, complex licensing, and costly professional services for integration and optimization.
| Seceon Solution | Palo Alto Challenges |
|---|---|
| Truly unified native platform | Stitched-together modules |
| Fast time-to-value out-of-box | Expensive professional services |
| Simple transparent single license | Complex multi-model pricing |
| Unified data model for better detection | Limited cross-module correlation |
| No integration overhead to maintain | Ongoing integration maintenance |



See how leading organizations are achieving unparalleled security and operational efficiency with our AI-powered platform.

Kunal Panchamia from eProtects shares how they’re transforming cybersecurity delivery for clients by leveraging Seceon’s unified platform.
Copyright @Seceon Inc 2025. All Rights Reserved.