
Cybersecurity is a race against time. Every day, businesses face sophisticated threats designed to exploit the smallest vulnerabilities. Among the most dangerous of these are Zero Day Malware attacks — malicious software that targets unknown flaws before vendors or defenders even know they exist.
Zero day malware represents the pinnacle of stealth and danger. Unlike conventional malware that exploits known weaknesses, zero days take advantage of unpatched, undiscovered vulnerabilities. This means that traditional defenses — signature-based antivirus or rule-based firewalls — are often powerless to stop them.
For organizations across industries, defending against zero day threats requires proactive, AI/ML-driven approaches, real-time monitoring, and rapid response capabilities. With Seceon’s Open Threat Management (OTM) platform, powered by AI, ML, and Dynamic Threat Modeling (DTM), enterprises and MSSPs gain the visibility, intelligence, and automation needed to combat zero day malware at machine speed.
Zero day malware is a type of malicious software designed to exploit vulnerabilities that are unknown to the software vendor, security community, or public.
Zero day malware is not only a threat to individual organizations but also a risk to global supply chains and national security.
Most traditional cybersecurity solutions rely on signatures, static rules, or patch cycles. Unfortunately, these approaches are insufficient for zero day threats.
Antivirus and intrusion detection systems match malware against known signatures. Since zero day malware exploits unknown vulnerabilities, there are no signatures to detect.
Even when a vulnerability is discovered, patches take time to develop and deploy. Attackers exploit the “window of exposure” between discovery and patching.
Legacy security tools often work in silos (endpoint-only or network-only). Zero day malware thrives in these blind spots, moving laterally until detected.
Modern zero day malware uses obfuscation, polymorphism, and fileless execution to evade traditional tools.
By the time conventional tools detect suspicious behavior, attackers may have already stolen sensitive data or compromised critical systems.
This is why organizations need proactive, adaptive, and automated solutions to stay ahead of zero day threats.
While no single measure guarantees prevention, organizations can dramatically reduce risk through layered defenses, AI-driven monitoring, and strong cyber hygiene.
Use solutions like Seceon’s aiSIEM and aiXDR-PMax to analyze behavior, detect anomalies, and spot unknown malware in real time.
DTM continuously builds behavioral baselines for users, devices, and applications, flagging anomalies that may indicate zero day exploits.
Stay ahead with continuous vulnerability management, automated patching, and external attack surface monitoring.
Adopt a Zero Trust model — never trust, always verify. Continuously authenticate users, devices, and applications.
Limit the spread of malware by segmenting networks and isolating compromised devices immediately.
Ingest global threat intelligence feeds to correlate patterns and identify potential zero day campaigns.
Secure all endpoints, workloads, and cloud assets with advanced monitoring and behavioral analysis.
Educate employees to recognize phishing, social engineering, and suspicious behavior — common vectors for zero day attacks.
Organizations looking to build resilience against zero day malware should begin with these steps:
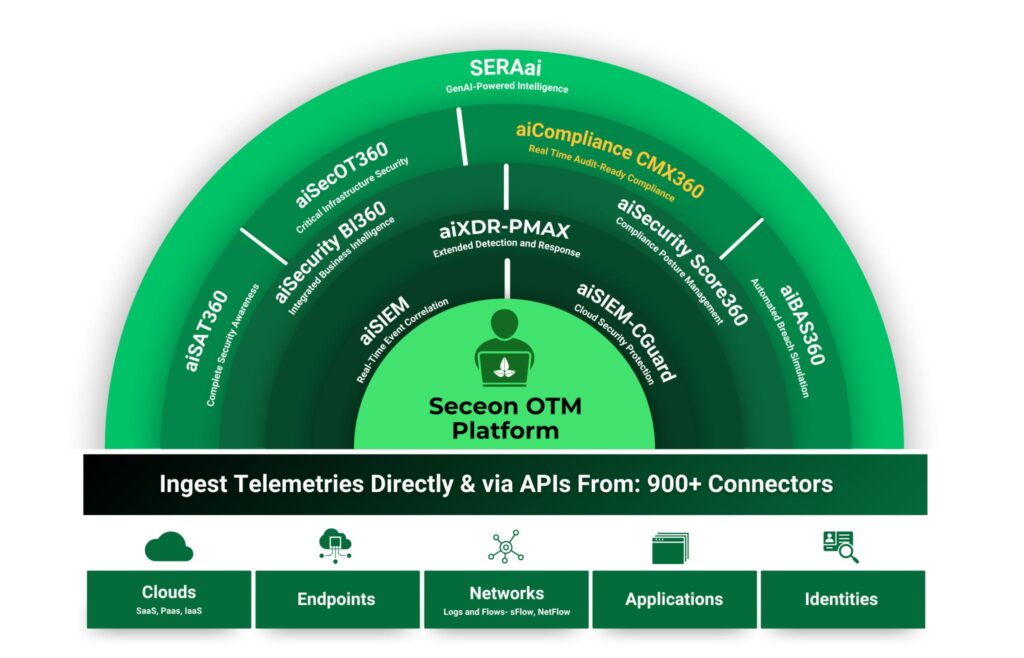
Seceon’s Open Threat Management (OTM) platform is purpose-built to combat sophisticated threats like zero day malware. By unifying AI/ML-driven analytics, Dynamic Threat Modeling, and automated response, Seceon provides unmatched protection against evolving cyberattacks.
Seceon’s platform applies advanced AI and ML models to analyze raw data streams (logs, flows, identities, applications, endpoints, and IoT/OT). Unlike signature-based tools, it identifies unknown and zero day threats based on behavior.
Patented DTM technology continuously maps user, device, and application behaviors. It spots unusual activities — like unauthorized access, lateral movement, or data exfiltration — that may indicate zero day exploits.
Seceon automatically:
This reduces dwell time from months to minutes.
Seceon consolidates monitoring across endpoints, networks, applications, IoT/OT, and cloud, ensuring there are no blind spots for attackers to exploit.
Seceon simplifies compliance with audit-ready reporting for standards like GDPR, HIPAA, PCI-DSS, and ISO 27001 — critical for regulated industries.
With multi-tenancy and scalability, Seceon enables MSSPs to deliver advanced zero day protection to hundreds of clients efficiently.
Q1: What is zero day malware?
Zero day malware is malicious software that exploits unknown or unpatched vulnerabilities, bypassing traditional defenses.
Q2: Why are zero day attacks so dangerous?
They target vulnerabilities defenders don’t yet know exist, leaving no time for patching or signature updates.
Q3: Can zero day malware be detected?
Yes, with AI/ML-driven anomaly detection and behavior analytics, organizations can spot suspicious activity even without known signatures.
Q4: How does Seceon detect zero day threats?
Seceon uses AI/ML analytics, Dynamic Threat Modeling, and real-time monitoring of logs, flows, and endpoints to detect unusual patterns.
Q5: What industries are most targeted by zero day malware?
Healthcare, financial services, energy, government, and technology sectors are frequent targets due to sensitive data and critical operations.
Q6: How can small businesses protect themselves?
Leverage managed detection and response (MDR) services, enforce Zero Trust security, patch frequently, and adopt AI-powered tools like Seceon.
Zero day malware represents one of the most significant challenges in cybersecurity. Traditional tools cannot keep up with its stealth and sophistication. Organizations must adopt proactive, intelligent, and automated defenses to mitigate the risk.
Seceon delivers exactly that. With AI/ML-driven detection, Dynamic Threat Modeling, automated response, and unified visibility, Seceon ensures enterprises and MSSPs can detect, prevent, and respond to zero day malware — before it causes lasting damage.
Zero day threats won’t wait. Neither should your defense. Protect your business today with Seceon.
