
The Middle East telecommunications sector has entered its most volatile cyber era. With the rapid rollout of 5G, the expansion of cloud native architectures, and the rise of massive IoT ecosystems, operators across the region are facing unprecedented targeting from nation state APTs, cybercriminal groups, and political threat actors.
In 2025, telecom providers experienced an average of 3,200 plus attacks per organization per week, reflecting sharp geopolitical tensions and a surge in targeting of telecom infrastructure.
With widespread adoption of O RAN, hyperscale data centers, and roaming heavy environments, the attack surface now spans legacy SS7 and Diameter to 5G core, SBA APIs, and multi-country interconnect ecosystems.
Traditional tools cannot handle this shift.
Legacy SIEMs cannot ingest petabyte scale telemetry, and enterprise SOC models cannot analyze telecom signaling in real time. This leads to blind spots, slow detection, and fragmented visibility.
📌 Full whitepaper here:
https://info.seceon.com/middle-east-telecommunications-cybersecurity-landscape-2025
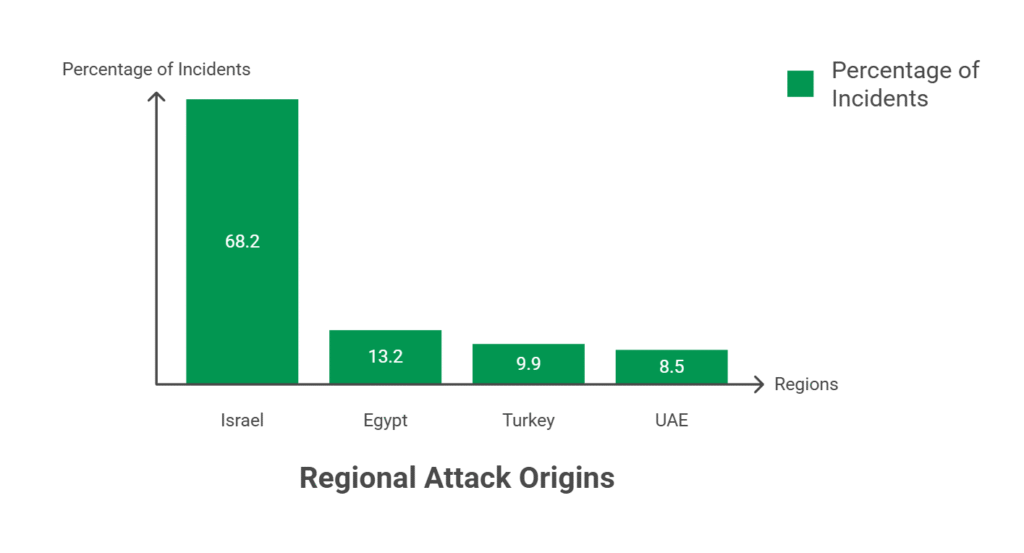
The region shows a sharp concentration of telecom-related cyber activity:
The GCC accounts for 27.5 percent of overall cyber threats targeting telecom.
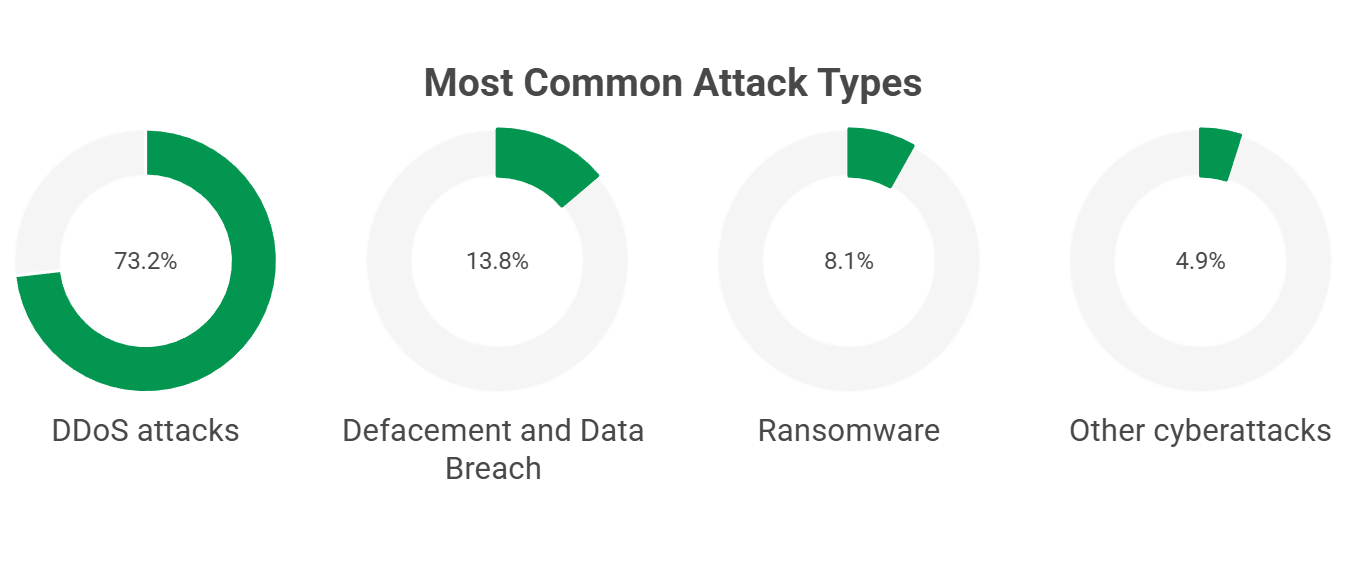
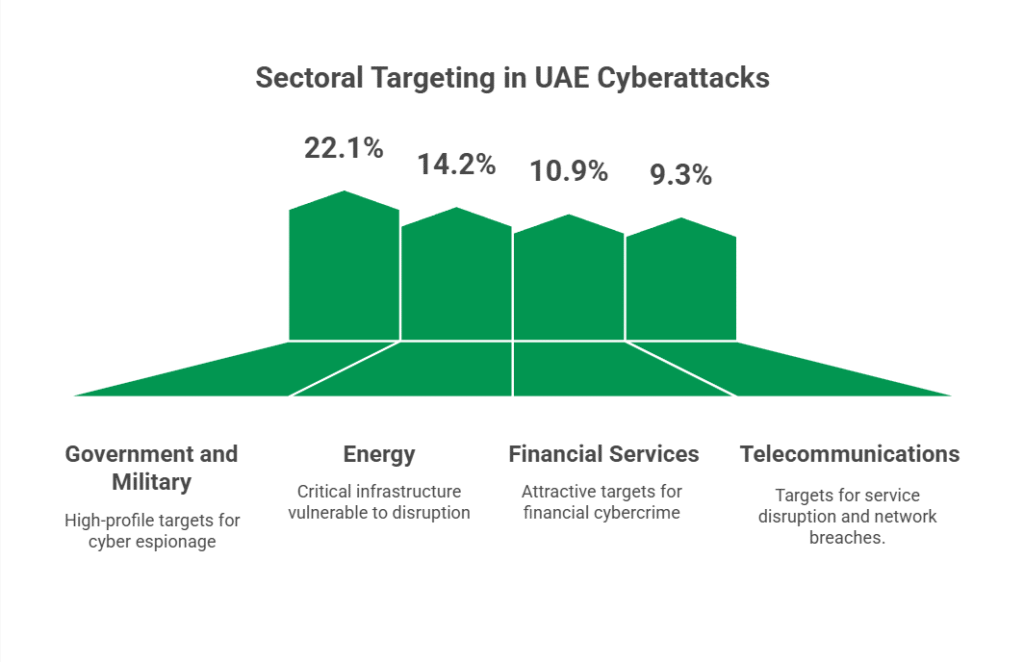
Telecom providers face unique challenges that legacy security tools cannot solve:
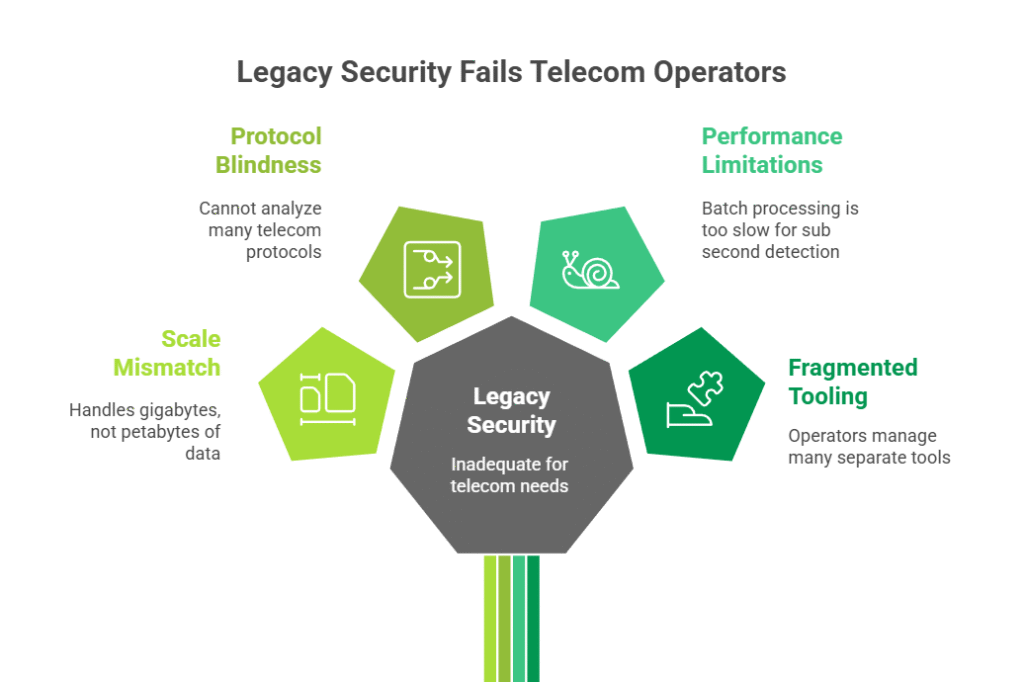
Telecom processes petabytes of data daily, while traditional SIEMs are built for gigabytes.
Enterprise tools cannot analyze:
Batch processing is too slow for telecom’s need for sub second detection.
Operators manage 15 to 20 separate tools, creating silos, delays, and visibility gaps.
These case studies show how AI powered unified security transforms major telecom operators:
Challenge:
Increasing SS7 and Diameter attacks used for subscriber tracking and signaling interception.
Seceon’s Role:
Results:
Challenge:
5G and O RAN traffic volumes exceeded legacy SIEM capacity.
Seceon’s Role:
Results:
Challenge:
Difficulty detecting APT activity across roaming and interconnect traffic.
Seceon’s Role:
Results:
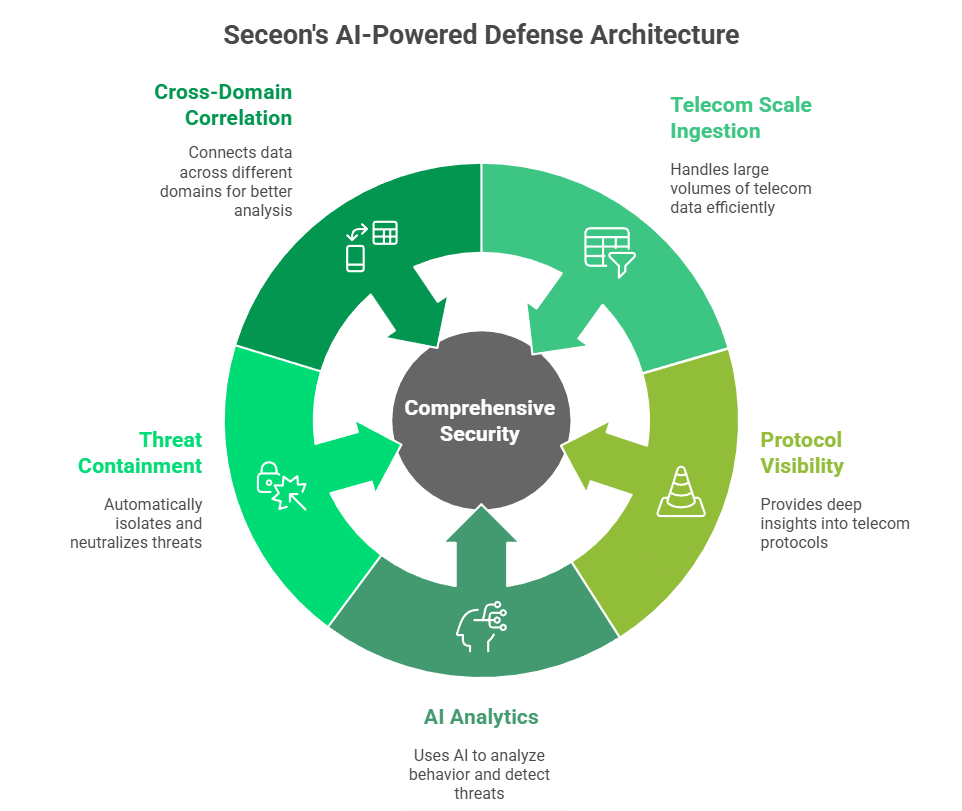
Seceon’s unified aiSIEM, aiXDR PMax and aiCompliance deliver full stack protection built for telecom scale.
The Middle East cybersecurity market is accelerating quickly:
Major investments include:
Telecom networks are now national security assets powering government platforms, financial systems, and cross-border data ecosystems.
With rising APT activity, signaling layer exploitation, and 5G complexity, it is clear that traditional security cannot protect telecom operators in 2025 and beyond.
The whitepaper emphasizes that:
Only unified, AI-driven, telecom native cybersecurity can provide real-time resilience at a national scale.
Seceon delivers:
With Seceon, operators achieve a future-ready, high-resilience security posture built for the Middle East’s next decade of digital growth.
