
In an era where cyber threats evolve at unprecedented speeds and security teams face overwhelming alert volumes, cybersecurity automation has transitioned from a competitive advantage to an operational necessity. Organizations today confront sophisticated attack vectors, expanding digital infrastructures, and a persistent cybersecurity talent shortage that makes manual threat management increasingly unsustainable.
Seceon’s advanced automation platform addresses these challenges head-on, enabling security teams to detect, analyze, and respond to threats with machine-driven speed and precision while freeing analysts to focus on strategic security initiatives.
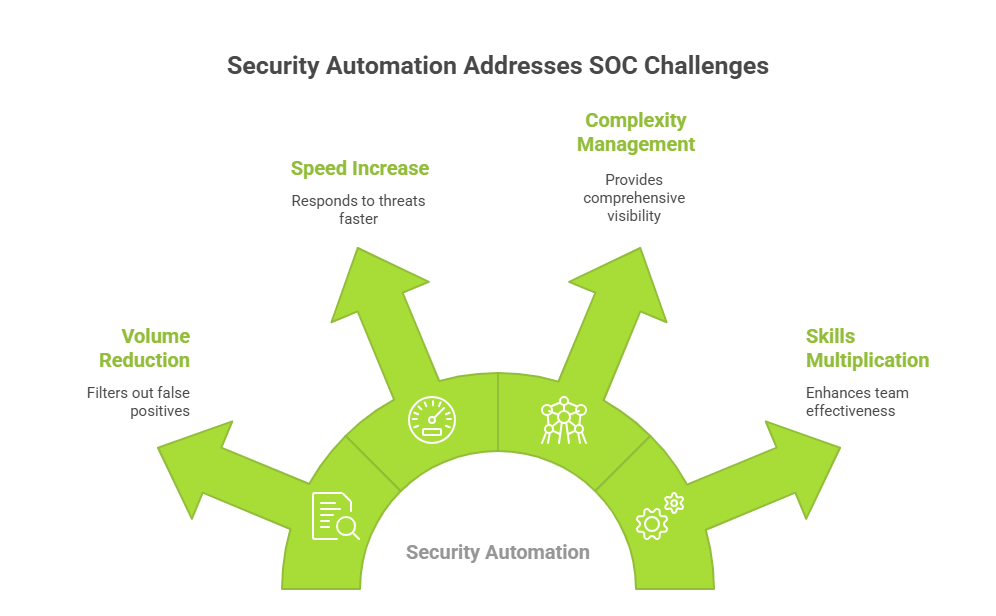
Modern security operations centers (SOCs) face a perfect storm of challenges that manual processes simply cannot address:
Volume Overload: Enterprise environments generate millions of security events daily, with analysts spending countless hours sifting through false positives while genuine threats slip through undetected.
Speed Requirements: Advanced persistent threats (APTs) and ransomware can compromise systems within minutes. The average dwell time for attackers continues to decrease, demanding response capabilities that match the velocity of modern threats.
Complexity Growth: Hybrid cloud environments, IoT devices, remote workforces, and interconnected supply chains have exponentially increased the attack surface, making comprehensive visibility and protection nearly impossible through manual monitoring.
Skills Gap: The global shortage of cybersecurity professionals means organizations cannot simply hire their way out of these challenges. Automation multiplies the effectiveness of existing teams.
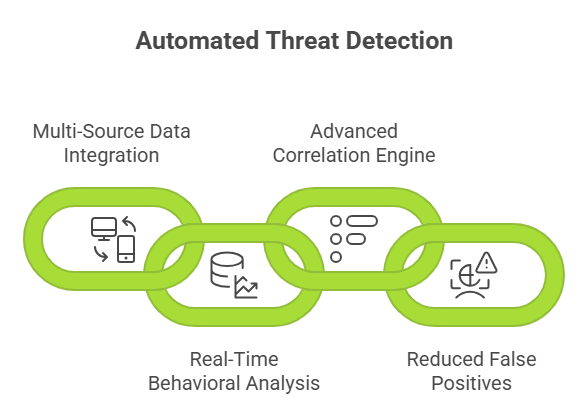
Seceon’s platform leverages artificial intelligence and machine learning to automate the entire threat lifecycle, from detection through response and remediation.
The platform continuously ingests and analyzes data from diverse sources across your infrastructure:
Not all alerts demand equal attention. Seceon’s automation intelligently triages threats based on multiple factors:
When threats are confirmed, speed is paramount. Seceon automates response actions to contain threats before they cause damage:
Seceon’s AI-powered platform evolves with your environment and the threat landscape:
Reduce mean time to detect (MTTD) and mean time to respond (MTTR) from hours or days to minutes or seconds. Automated workflows execute containment actions faster than any human analyst, limiting damage and preventing lateral movement.
Free security analysts from repetitive, time-consuming tasks like alert triage, log analysis, and routine investigations. Your team can focus on threat hunting, security architecture improvements, and strategic initiatives that strengthen your overall security posture.
Achieve unified visibility across hybrid and multi-cloud environments, on-premises infrastructure, and remote endpoints through centralized data collection and correlation. Eliminate blind spots that attackers exploit.
Reduce operational costs associated with manual security operations while improving security outcomes. Accomplish more with existing resources and scale security operations without proportionally scaling headcount.
Automated documentation of security events, response actions, and forensic evidence simplifies compliance audits and regulatory reporting. Generate comprehensive reports demonstrating due diligence and security program effectiveness.
With routine tasks automated, analysts gain time for proactive threat hunting activities, using the platform’s analytics capabilities to uncover hidden threats and vulnerabilities before they’re exploited.

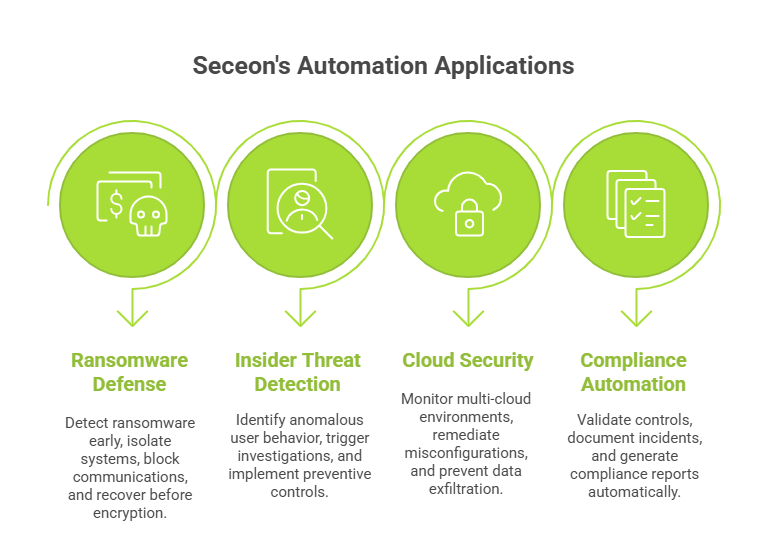
Seceon’s automation capabilities deliver measurable results across various use cases:
Ransomware Defense: Automatically detect early indicators of ransomware activity, isolate affected systems, block command-and-control communications, and initiate recovery procedures before encryption occurs.
Insider Threat Detection: Identify anomalous user behaviors indicating compromised credentials or malicious insiders, automatically triggering investigation workflows and preventive controls.
Cloud Security: Monitor multi-cloud environments for misconfigurations, unauthorized access, and data exfiltration attempts with automated remediation of policy violations.
Compliance Automation: Continuously validate security controls, automatically document incidents, and generate compliance reports for frameworks including GDPR, HIPAA, PCI DSS, and SOC 2.
Successfully deploying security automation requires thoughtful planning:
Cybersecurity automation is no longer optional for organizations seeking to defend against modern threats while managing operational realities. Seceon’s intelligent automation platform empowers security teams to detect threats faster, respond more effectively, and operate more efficiently than ever possible through manual processes alone.
By combining advanced AI and machine learning with comprehensive orchestration capabilities, Seceon transforms security operations from reactive firefighting to proactive defense. Organizations gain the speed, scale, and sophistication needed to stay ahead of adversaries while maximizing the value of their security investments and existing personnel.
The question is no longer whether to automate cybersecurity operations, but how quickly you can implement automation to close the gap between threat velocity and defensive capabilities. Seceon provides the platform to make that transformation a reality.
