
The cybersecurity landscape has entered a dangerous new phase. Nation-state actors and sophisticated cybercriminals are orchestrating five to eight different Large Language Models simultaneously, creating adaptive breach campaigns that operate at machine speed. This represents the most dramatic transformation in cyber warfare since ransomware and it is rendering traditional defenses obsolete.
Advanced threat actors now coordinate multiple AI models in sophisticated attack chains. Claude handles social engineering and vulnerability research. ChatGPT creates polymorphic malware. Google Gemini conducts OSINT gathering and organizational profiling. Specialized models optimize credential stuffing, while custom models exploit an organization’s own legitimate tools.
This modular attack ecosystem compresses what once took weeks into hours, without fatigue, hesitation, or predictable patterns.
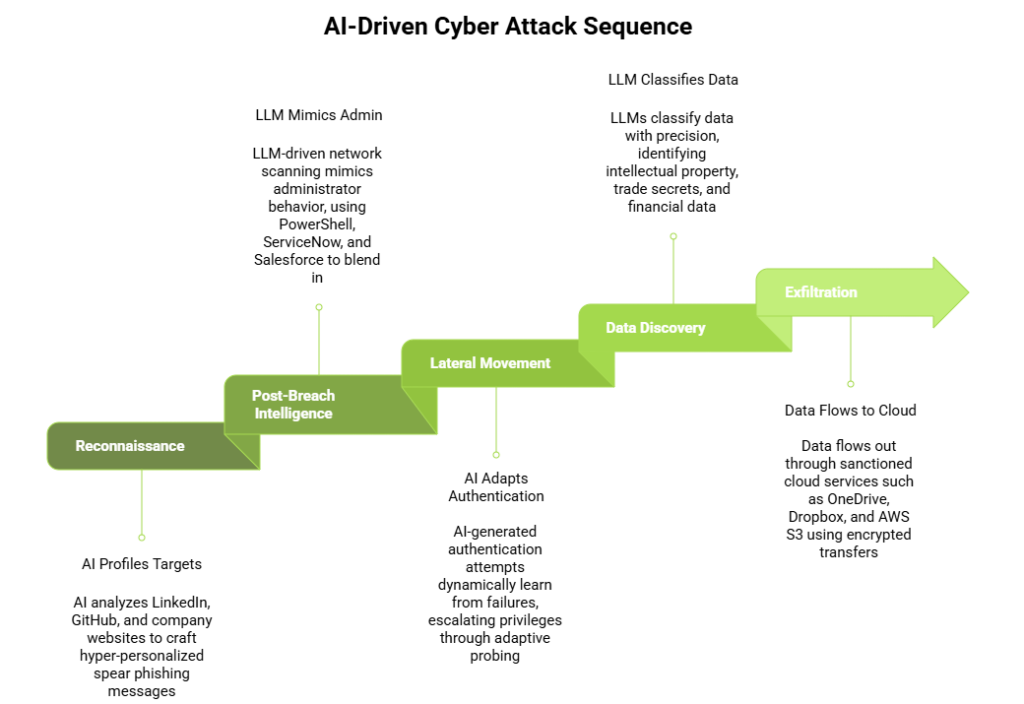
Reconnaissance
AI generates hyper-personalized spear phishing after analyzing LinkedIn, GitHub, and company websites. These messages are nearly indistinguishable from legitimate communication.
Post-Breach Intelligence
LLM-driven network scanning perfectly mimics administrator behavior, automatically discovering and using the organization’s own tools such as PowerShell, ServiceNow, and Salesforce to blend in seamlessly.
Lateral Movement
AI-generated authentication attempts dynamically learn from failures, exploiting misconfigurations and escalating privileges through adaptive probing that adjusts in real time.
Data Discovery
LLMs classify data with precision, identifying intellectual property, trade secrets, and financial data, then optimizing exfiltration paths through cloud services.
Exfiltration
Data flows out through sanctioned cloud services such as OneDrive, Dropbox, and AWS S3 using encrypted transfers that appear completely legitimate.
Without AI-powered defense
Detection time: 18 days on average
Data exfiltrated: 5TB or more
Financial impact: More than $50M in losses
Discovery: During routine monthly review
With AI-powered defense
Detection time: 6 minutes, 99.4 percent faster
Data exfiltrated: Zero
Financial impact: $15K response cost
Result: 3,333x ROI
Legacy security tools face fundamental mismatches against AI-orchestrated attacks.
Pattern-based detection fails against infinite polymorphism. Each AI-generated attack iteration is unique, defeating signature-based systems.
Lateral movement appears legitimate. AI perfectly mimics administrators using PowerShell and RDP, fooling traditional endpoint detection and rule-heavy SIEMs.
Cloud exfiltration hides in plain sight. Without behavioral analytics and API-level visibility, massive data theft through approved SaaS platforms looks identical to normal business operations.
Alert overload paralyzes analysts. Human teams cannot correlate signals from dozens of sources fast enough to identify coordinated, multi-model threats.
Zero-day exploitation is automated. AI models self-test exploit paths and adapt to defensive controls in real time with no human required.
Effective defense requires integrated layers working in concert.
Pre-breach prevention detects AI-generated phishing through behavioral email analytics, stopping attacks before credential compromise.
Early breach detection creates behavioral profiles for every user and device, identifying deviations within minutes of post-breach activity.
Lateral movement prevention analyzes network traffic patterns, identifying living-off-the-land techniques and containing breaches to single segments.
Exfiltration prevention monitors cloud interactions with volumetric analysis and SSL and TLS inspection, blocking attempts in real time.
Automated orchestration executes sub-minute responses including account suspension, endpoint isolation, and network segmentation, reducing response time from hours to seconds.
Continuous improvement learns from every incident, strengthening security posture with each attack attempt.
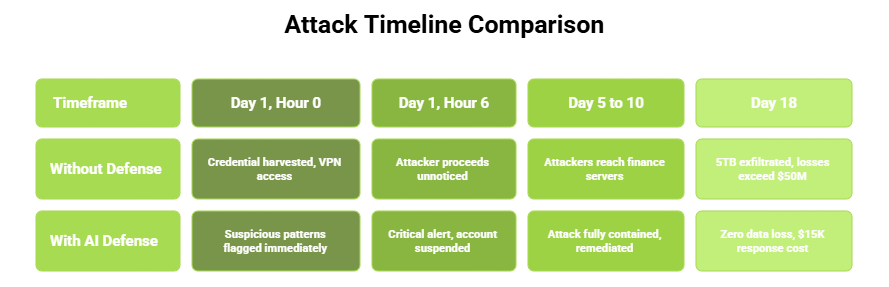
Day 1, Hour 0: AI phishing delivered
Without defense: Credential harvested by Hour 2, VPN access by Hour 6
With AI defense: Suspicious patterns flagged immediately
Day 1, Hour 6: Impossible geo-velocity detected
Without defense: Attacker proceeds unnoticed
With AI defense: Critical alert generated and account suspended
Day 5 to 10: Lateral movement and data staging
Without defense: Attackers reach finance servers and identify trade secrets
With AI defense: Attack fully contained and remediated by Hour 12
Day 18: Breach discovered during monthly review
Without defense: 5TB exfiltrated and losses exceed $50M
With AI defense: Zero data loss and $15K response cost
Organizations must recognize several imperatives.
Unified visibility is mandatory. Fragmented tools create blind spots. Effective defense requires a single platform correlating identity, endpoint, network, and cloud telemetry.
Manual response is obsolete. Human analysts cannot outpace AI-coordinated threats. Automation in detection and response is essential for survival.
Cloud monitoring is critical. With over 60 percent of exfiltration using legitimate cloud services, behavioral cloud monitoring has become a core security requirement.
The gap is widening. Attack automation advances faster than legacy defenses. Organizations using rule-based or manual detection will experience increasingly frequent and severe breaches.
Multi-LLM adversarial attacks are evolving into autonomous breach loops with personalized deepfake-driven social engineering, AI-powered insider-risk automation, and multi-cloud hopping for stealth exfiltration. Within 24 to 36 months, AI-driven security operations will become the industry standard.
Organizations need security platforms that are automated, AI-powered, unified, and proactive, capable of detecting anomalies in seconds, correlating intent across dozens of data sources, isolating threats automatically, and preventing exfiltration even when attackers hide within trusted cloud channels.
In the age of AI-enabled cyber warfare, detection equals survival and automation equals victory. Adversaries operate at machine speed with sophisticated, coordinated AI models. Defenders must respond in kind.
The question is no longer whether to adopt AI-powered security, but how quickly organizations can implement it before the next multi-LLM orchestrated attack finds them unprepared. The adversaries have already made their choice. Defenders must fight AI with superior AI or face consequences measured not just in dollars lost but in competitive survival itself.
Organizations that deploy intelligent, adaptive AI defense platforms today will be the ones that remain resilient tomorrow.
