
Security teams invest heavily to eliminate blind spots, yet many organizations unintentionally create them through fragmented security architectures. These blind spots are not caused by a lack of telemetry. They are created when security platforms fail to interpret activity as a unified story across cloud, endpoint, identity, and network environments.
Modern attacks are designed to exploit this exact weakness. They do not rely on obvious malware or noisy exploitation. Instead, they move quietly across multiple domains, ensuring each individual action appears legitimate when viewed by a single tool. By the time the activity is recognized as malicious, the attacker has already progressed.
This is not a failure of access controls alone. It is a failure of visibility.
In stitched security environments, visibility is divided by design. Endpoint platforms monitor devices rather than user intent. Cloud tools focus on configurations instead of behavior. Identity systems record authentication events without understanding misuse. Network tools observe traffic but lack business context.
Each system functions correctly within its own scope. Logins succeed, processes appear approved, and network traffic is authorized. However, no single platform understands how these actions connect. When attackers chain these activities together, the attack passes through every control unnoticed.
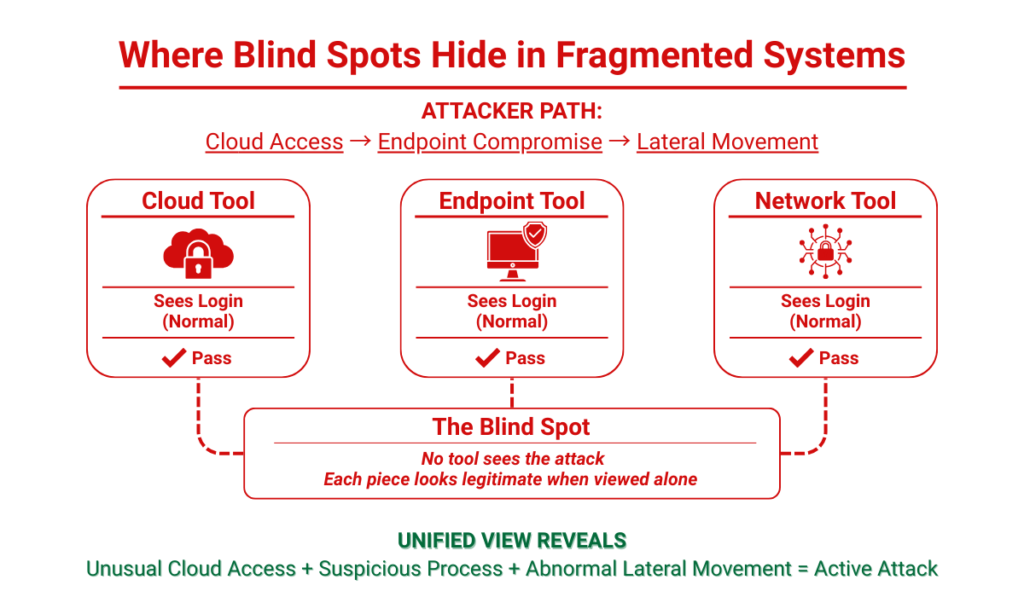
By the time the threat is identified, the opportunity to stop it early has already passed.
Advanced attackers rarely attempt to defeat security controls directly. Instead, they operate between them. Legitimate credentials are used to avoid alerts. Approved administrative tools enable lateral movement. Cloud APIs are abused in ways that resemble normal operations. Actions are spread over time to remain below detection thresholds.
When analyzed individually, these behaviors appear harmless. When correlated together, they reveal a coordinated attack. Fragmented platforms analyze each signal separately, allowing attackers to move freely across domains without triggering meaningful response.
Cross domain attacks now represent the most damaging incidents across enterprise environments. Cloud access followed by endpoint compromise, email attacks that lead to lateral movement, and VPN access paired with privilege escalation are increasingly common patterns.
Organizations operating with disconnected security tools experience delayed detection, prolonged investigations, and increased business disruption. SOC teams are forced to manually stitch alerts together, often under pressure and after damage has occurred.
Executive dashboards may show high coverage, large data volumes, and controls enabled, but they rarely reveal what was not correlated, what required analyst assumption, or what appeared benign until it was too late. This creates a false sense of security maturity.
When behavioral context is missing, security teams chase symptoms rather than causes. Response actions become cautious and incomplete. Investigations stretch from minutes into hours or days. Business operations suffer while attackers gain time to expand their presence.
Fragmentation does not just slow detection. It actively works in the attacker’s favor.
True visibility is not about collecting more data. It is about understanding behavior across security domains in real time. Effective detection requires a unified data model, continuous behavioral baselining, cross domain analytics, and automated context preservation.
Without these capabilities, blind spots are inevitable, regardless of how many tools are deployed.
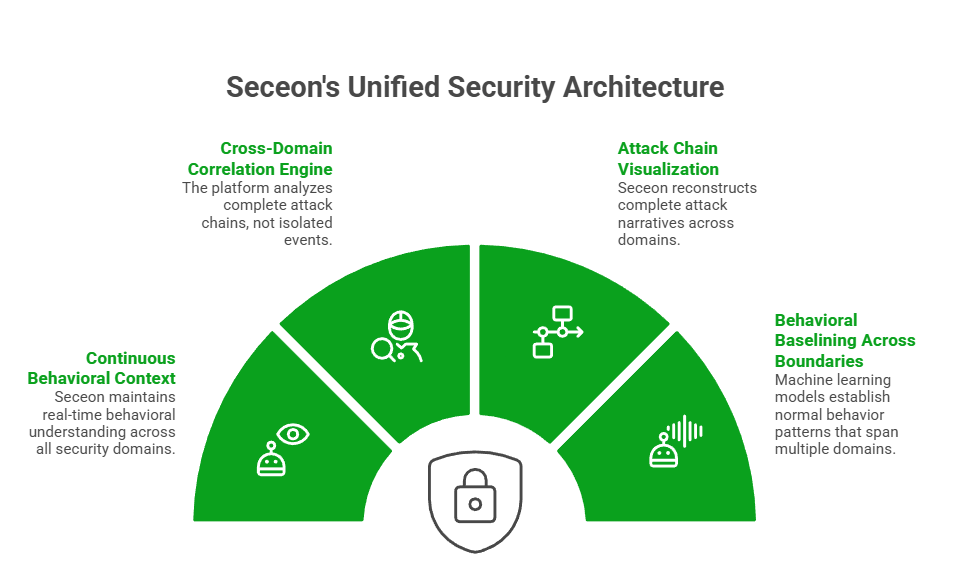
Seceon’s unified architecture was specifically designed to eliminate the gaps between security domains where attackers hide.
Continuous Behavioral Context: Seceon doesn’t just collect telemetry, it maintains behavioral context across all security domains simultaneously. When a cloud login occurs, the platform already understands that user’s typical endpoint behavior, network patterns, and privilege usage.
Cross-Domain Correlation Engine: The platform’s analytics operate on complete attack chains, not isolated events. A credential compromise in the cloud automatically triggers enhanced monitoring of that identity’s endpoint activity and network behavior without manual playbook execution.
Attack Chain Visualization: Seceon reconstructs complete attack narratives across domains, showing security teams exactly how an attacker moved from initial access to lateral movement, even when those actions occurred weeks apart.
Behavioral Baselining Across Boundaries: Machine learning models establish normal behavior patterns that span cloud, endpoint, network, and identity making anomalies that cross these boundaries immediately visible rather than buried in separate tool queues.
Organizations using Seceon report detecting sophisticated attacks that their previous multi-tool environments missed entirely, particularly attacks that deliberately exploit the seams between security domains.
Attackers no longer need to hide from security tools. They simply move between them. As security stacks become more fragmented, these gaps grow wider and harder to defend. Real protection comes from unified, behavior driven security that understands activity as a whole. Without that foundation, even advanced tools can create the very blind spots attackers depend on.
