
Advanced threat detection has become an indispensable pillar in the fight against cybercrime. In a world where threats are not only growing in number but also increasing in sophistication, organizations must evolve their security strategies to stay ahead. Cyberattackers no longer rely on basic malware or simple exploits; instead, they leverage multi-stage attacks, living-off-the-land techniques, identity compromise, lateral movement, and AI-assisted evasion methods to stay undetected for weeks, if not months. Traditional security solutions, which typically depend on static rules and known signatures, are ill-equipped to detect these advanced threats in real-time. As a result, enterprises need to adopt advanced threat detection powered by artificial intelligence (AI), machine learning (ML), and behavioral analytics to ensure the protection of their digital assets, business continuity, and brand integrity.
The Evolution of Threats: From Simple Malware to Advanced Attacks
As the threat landscape evolves, attackers have become more methodical in their approach. The days of simple malware strains designed to cause immediate harm are long gone. Today, adversaries employ advanced persistent threats (APTs), ransomware campaigns, and even tactics used by nation-state actors to infiltrate networks. These sophisticated adversaries often begin with reconnaissance, followed by credential harvesting, privilege escalation, and then lateral movement across an organization’s infrastructure. Throughout this process, their activities can appear entirely legitimate, making them hard to distinguish from normal system operations.
The key to detecting these complex attack strategies lies in a comprehensive approach to behavioral analytics and correlated threat intelligence. A successful attack may appear to be a series of unrelated events when viewed in isolation. However, by correlating behavior over time and across multiple systems, organizations can build a timeline of the attack’s progression and identify anomalies at an early stage. AI-driven detection systems make this possible by continuously analyzing large volumes of data from across the network, endpoints, cloud, and other digital environments.
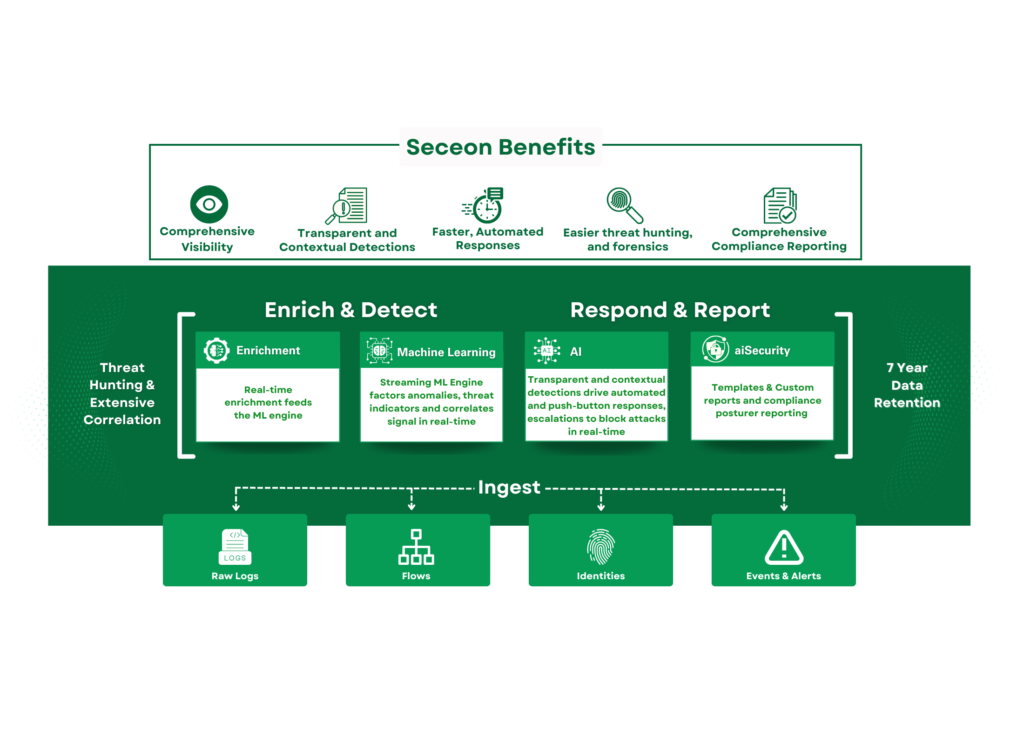
The Foundations of Advanced Threat Detection
Advanced threat detection systems focus on uncovering suspicious behaviors, subtle anomalies, and the correlation of signals across multiple digital environments. These platforms go far beyond merely detecting known malware and look for deviations from normal behavior—patterns that could indicate a security breach in progress.
Here’s how modern advanced threat detection platforms work:
The Increasing Complexity of Today’s Cyber Threat Landscape
Today’s enterprises operate in highly complex, hybrid infrastructures that span on-premises networks, cloud environments, SaaS platforms, mobile devices, IoT (Internet of Things) systems, and more. Each of these environments generates vast amounts of telemetry that needs to be continuously ingested and analyzed to detect potential threats.
Cloud environments, in particular, pose unique challenges for threat detection. Cloud platforms are inherently dynamic, with resources constantly being provisioned and decommissioned. This makes it harder to track who has access to what, when, and why. Furthermore, common misconfigurations, overly permissive identities, and exposed APIs are frequent entry points for attackers.
Advanced threat detection platforms that monitor cloud activity in real time are critical for identifying risky changes, suspicious API calls, and unauthorized access attempts across cloud environments. By correlating these signals with network and identity telemetry, organizations gain a comprehensive view of their digital estate’s risk profile.
The Importance of Detecting Identity-Based Attacks
One of the most prevalent and damaging forms of compromise today is identity-based attacks. Attackers use various techniques such as phishing, social engineering, multi-factor authentication (MFA) fatigue, and token theft to obtain credentials and blend into legitimate user behavior. Once they gain access, they often escalate privileges and move laterally within the network.
Advanced threat detection systems help uncover these subtle attacks by leveraging User and Entity Behavior Analytics (UEBA). By continuously monitoring and analyzing user and entity behaviors, these systems can identify indicators of compromise (IoCs), such as:
These types of activities may be indicative of a compromised account, and the AI-driven correlation within advanced detection systems can highlight these behaviors before an attacker can escalate their efforts.
Leveraging AI for Endpoint and Network Detection
Endpoints and networks are primary targets for attackers, and therefore, effective threat detection across both is critical. Traditional endpoint detection often relies on signature-based detection of known threats. However, modern malware increasingly operates in a fileless manner, using legitimate tools such as PowerShell or WMI to carry out malicious activities without leaving traces on the disk.
Advanced endpoint threat detection focuses on monitoring system behavior, process execution, and memory usage. By combining this data with network analytics, organizations can correlate endpoint activity with lateral movement or data exfiltration attempts.
Network-based threat detection also plays a crucial role. Even in highly encrypted environments, attackers must communicate, move laterally, and exfiltrate data. Through flow-based analytics, advanced systems analyze traffic flows, connection patterns, and communication behaviors to identify activities such as command-and-control (C2) communication, lateral movement, and data exfiltration.
Automation and Alert Fatigue: Addressing the Challenges of Detection and Response
One of the biggest challenges in threat detection is alert fatigue. Legacy systems often generate massive volumes of alerts, many of which are false positives, which can overwhelm security teams and obscure real threats. Advanced threat detection platforms address this issue by automating response and prioritizing alerts based on risk and potential impact.
When high-confidence threats are identified, automated responses—such as isolating compromised devices, disabling accounts, or blocking malicious connections—can be triggered immediately. This reduces the mean time to respond (MTTR) and ensures that attacks are neutralized before they can do significant damage. Automation is particularly important when dealing with fast-moving attacks like ransomware, where timely intervention is critical.
Advanced Threat Detection: A Business Imperative
From a business perspective, implementing advanced threat detection provides immense value. It helps reduce breach risks, minimize downtime, and protect sensitive data. Moreover, many regulations now require continuous monitoring and timely detection of security incidents. Advanced threat detection platforms help organizations meet these compliance requirements by providing comprehensive visibility, audit trails, and detailed reporting capabilities.
For Managed Security Service Providers (MSSPs), advanced threat detection represents a critical differentiator. Customers expect proactive protection, not just passive alerting. AI-driven detection platforms enable MSSPs to monitor multiple environments simultaneously, scale their services, and deliver higher-quality outcomes, all while improving operational efficiency.
The Road Ahead: The Future of Advanced Threat Detection
As cyberattackers increasingly adopt AI and automation, the defensive landscape must evolve in parallel. Future threat detection systems will need to be more autonomous, predictive, and integrated. By leveraging technologies like AI and dynamic threat modeling, these platforms will be able to anticipate attacker behavior and respond in real-time, protecting organizations from tomorrow’s cyber threats today.
Conclusion: Advanced Threat Detection as the Foundation of Cybersecurity
In conclusion, advanced threat detection is a fundamental component of any modern cybersecurity strategy. With increasingly complex attacks, traditional detection methods are no longer sufficient. Advanced threat detection systems—powered by AI, machine learning, behavioral analytics, and dynamic threat modeling—offer the insights and capabilities organizations need to stay ahead of cybercriminals. By combining visibility across cloud, network, endpoint, identity, and OT environments, these platforms provide not just detection but real, actionable resilience. For enterprises, governments, and service providers, investing in advanced threat detection is an essential step in protecting against today’s sophisticated threats and ensuring a secure digital future.
