
Every security operations team faces the same fundamental tension: threats are getting faster, more sophisticated, and harder to detect – yet the tools and processes most organizations rely on were built for a different era. Analysts are buried in alerts. Response workflows are slow. And attackers know it.
The consequences are measurable. According to IBM’s 2024 Cost of a Data Breach Report, organizations take an average of 258 days to identify and contain a breach. During that window, adversaries move laterally, escalate privileges, exfiltrate data, and entrench themselves – often undetected. The longer the dwell time, the higher the cost, the greater the damage.
Automated Incident Response, delivered through AI-driven Extended Detection and Response (XDR), represents a fundamental shift in how organizations approach this problem. Rather than relying on reactive, human-paced workflows, AI-driven XDR enables security teams to detect, investigate, and contain threats at machine speed – dramatically compressing the window adversaries have to operate.
To understand the value of automated response, it helps to examine where conventional approaches break down. Most enterprise security stacks are built around a combination of SIEM platforms, endpoint detection tools (EDR), and network monitoring solutions – each generating its own alerts, its own data formats, and its own view of the environment.
The result is a fragmented, manually intensive operation that creates four consistent failure modes:
• Alert Fatigue: Modern SIEMs can generate tens of thousands of alerts per day. The vast majority are false positives or low-priority events – but every one requires analyst time to evaluate. Teams become overwhelmed, response quality degrades, and genuine threats get lost in the noise.
• Fragmented Visibility: When an attacker moves from a compromised endpoint to a cloud workload to a privileged identity, the evidence is scattered across three different tools with no native correlation. Piecing together the full attack story requires hours of manual investigation.
• Slow Response Cycles: Traditional incident response is governed by runbooks – step-by-step procedures that require human approval and execution at each stage. Against threats that move in minutes, this is simply not fast enough.
• Detection Blind Spots: Signature-based detection catches known threats. But attackers routinely use novel techniques, zero-day exploits, and legitimate system tools to conduct malicious activity – leaving no signature to match and no alert to trigger.
Extended Detection and Response (XDR) is a security architecture designed to eliminate the silos that define most enterprise security stacks. Rather than treating endpoints, networks, cloud environments, and identity systems as separate domains, XDR unifies telemetry from all of them into a single platform – enabling detection and response that spans the full attack surface.
AI-driven XDR goes further by embedding machine learning and automation into every stage of the security lifecycle. The platform does not simply collect and display data – it continuously analyzes it, identifies threats, and acts on them, often without requiring human intervention.
The distinction from traditional SIEM is fundamental. SIEM aggregates logs and fires rules-based alerts. AI-driven XDR correlates behavior across domains, builds contextual incident narratives, assigns risk scores, and executes automated response – all in real time. It replaces a reactive tool with a proactive system.
• Unified Data Ingestion: Collects telemetry from endpoints, network flows, cloud workloads, SaaS applications, identity systems, DNS, email, and third-party threat intelligence into a centralized analytics layer.
• Behavioral Analytics and ML Detection: Supervised models detect known attack patterns mapped to the MITRE ATT&CK framework. Unsupervised models establish behavioral baselines and surface anomalies that no signature would catch – including zero-day activity and insider threats.
• Automated Correlation and Triage: Related events across disparate sources are automatically grouped, deduplicated, and enriched into a single incident narrative – scored by severity, confidence, and potential business impact.
• Orchestrated Response: Pre-configured playbooks execute containment and remediation actions automatically upon threat confirmation – from isolating an endpoint to revoking a cloud identity – in seconds rather than hours.
• Continuous Learning: Every incident refines the platform’s detection models, improving accuracy and closing coverage gaps over time without manual tuning.
Automated incident response does not eliminate human judgment – it reserves human judgment for decisions that genuinely require it. The routine, time-sensitive work of detection, triage, and initial containment is handled at machine speed, giving analysts the context they need to act decisively on what remains.
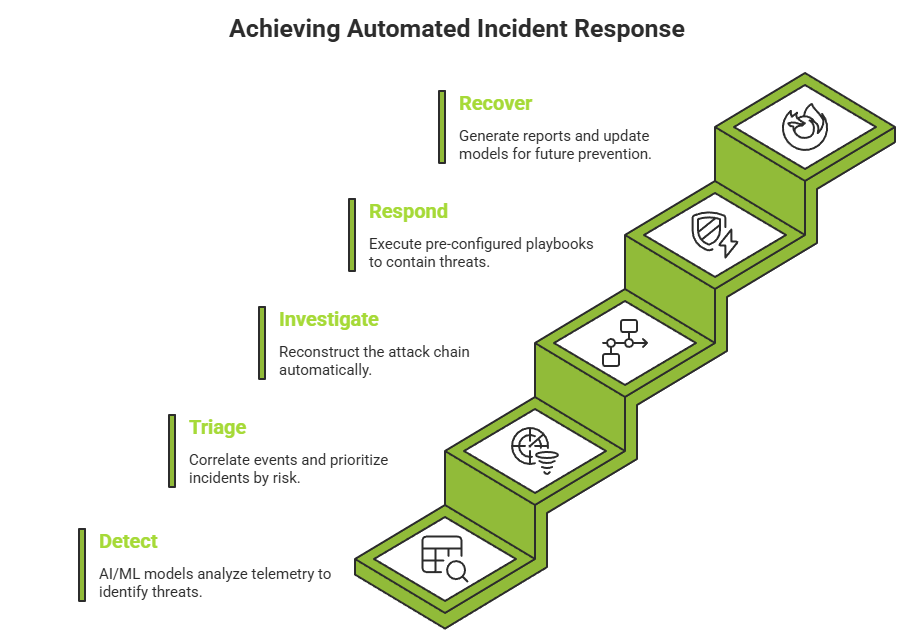
A mature automated response lifecycle operates across five stages:
AI/ML models analyze streaming telemetry continuously, identifying both known threat signatures and behavioral anomalies the moment they appear. Every detection is automatically enriched with threat intelligence context, attack technique classification, and asset sensitivity scoring – giving analysts immediate situational awareness without additional research.
Rather than presenting analysts with a queue of thousands of isolated alerts, the platform automatically correlates related events into unified incidents and ranks them by risk. High-priority incidents are escalated immediately with full context. Lower-priority events are handled autonomously or scheduled for review – keeping workloads manageable without sacrificing coverage.
The platform reconstructs the full attack chain automatically – tracing the sequence of events from initial compromise through lateral movement, privilege escalation, and data access across every relevant data source. What would take an analyst hours to piece together manually is produced in seconds as a structured, timeline-based incident narrative.
Pre-configured playbooks execute targeted response actions within seconds of threat confirmation:
• Endpoint isolation – removing compromised devices from the network while preserving forensic artifacts
• Credential revocation – terminating active sessions and enforcing re-authentication on suspicious accounts
• Traffic blocking – applying firewall rules and DNS blocks to sever adversary communications
• Cloud remediation – disabling compromised accounts and rolling back unauthorized infrastructure changes
• Stakeholder notification – delivering real-time incident summaries to security leadership and relevant teams
For actions with significant operational impact, human-in-the-loop approval workflows ensure automation is applied with appropriate oversight.
Post-incident, the platform generates detailed remediation reports and updates its detection models based on new threat patterns observed during the event. Each incident makes the system smarter – progressively narrowing detection gaps and improving response precision over time.
The value of AI-driven XDR and automated response is best understood through the threat scenarios it is built to address:
Ransomware operates on speed – the faster it encrypts, the more damage it causes. Behavioral detection identifies the hallmarks of ransomware activity (rapid file modification, abnormal process spawning, mass renaming) within moments of execution. Automated response then:
• Isolates the affected endpoint immediately, halting lateral spread
• Severs C2 communications at the network layer
• Triggers backup integrity checks and initiates recovery workflows
• Alerts the security team with a complete attack timeline and recommended next steps
Insider threats – whether malicious or inadvertent – rarely trigger signature-based alerts. Behavioral baselines built across users, devices, and applications surface activity that deviates from established norms, including:
• Abnormal access to sensitive files or databases outside business hours
• Bulk data transfers to unauthorized external destinations
• Unusual login patterns – impossible travel, unfamiliar geographies, off-hours access
• Lateral movement to systems outside the user’s normal operational scope
As workloads migrate to cloud environments, the attack surface expands well beyond what perimeter-based tools can monitor. AI-driven XDR extends coverage to detect:
• Exposed storage buckets, databases, or compute instances with public access
• Unauthorized IAM privilege escalation or policy modifications
• Cryptomining or resource abuse within cloud accounts
• Compliance drift across GDPR, HIPAA, PCI DSS, and other regulatory frameworks
Nation-state actors and sophisticated threat groups operate patiently – moving slowly to avoid triggering rules-based detection. Cross-domain correlation identifies their presence by connecting events that appear innocuous in isolation:
• Anomalous behavior originating from trusted third-party software or vendor access
• Slow, methodical lateral movement inconsistent with legitimate user patterns
• Covert reconnaissance activity targeting critical assets over extended periods
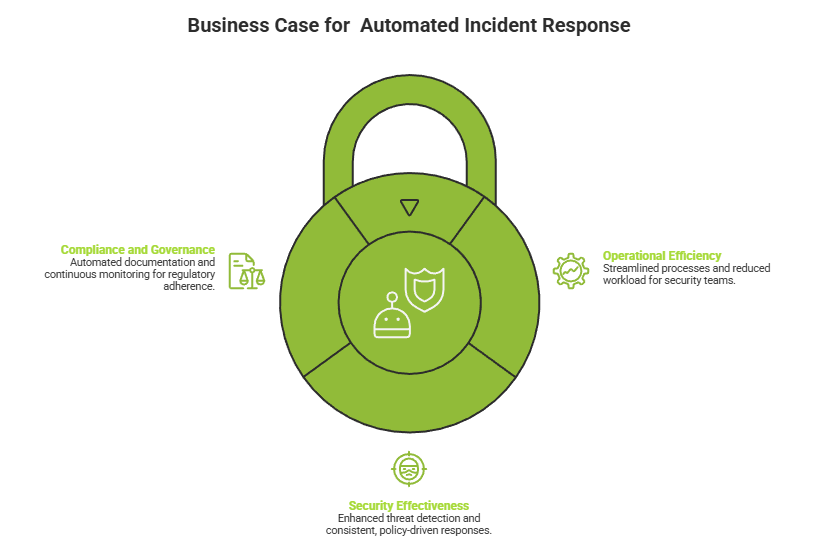
Security investments are ultimately justified by outcomes – and AI-driven XDR with automated incident response delivers measurable results across three dimensions that matter to security leaders and business executives alike:
• Significant compression of MTTD and MTTR – reducing response timelines from days to minutes
• Reduced alert volume reaching human analysts through automated triage and noise suppression
• Lower SOC staffing burden as automation handles high-volume, repetitive detection and response tasks
• Platform consolidation – replacing multiple point tools with a single integrated environment
• Earlier detection across the full attack lifecycle, from initial access through exfiltration
• Consistent, policy-driven response that eliminates variability and human error under pressure
• Broader coverage of advanced threats that bypass signature-based detection
• Reduced adversary dwell time – limiting the damage window before containment
• Automated audit trails and incident documentation supporting regulatory requirements
• Continuous compliance monitoring across GDPR, HIPAA, PCI DSS, SOC 2, NIST, and ISO 27001
• Board-ready reporting that demonstrates security posture and investment effectiveness
Seceon’s Open Threat Management (OTM) platform is purpose-built to operationalize AI-driven XDR and automated incident response at enterprise scale. Where many vendors retrofit automation onto legacy SIEM infrastructure, Seceon’s OTM was designed from the ground up with AI, behavioral analytics, and response orchestration as foundational capabilities – not add-ons.
• Full-spectrum visibility across endpoints, networks, cloud workloads, identity systems, SaaS applications, and IoT devices – from a single, unified platform integrated with 200+ security tools and technologies.
• A multi-layered AI/ML detection engine combining supervised learning for known threats, unsupervised behavioral analytics for unknown threats, and continuous model refinement that improves with every incident – all mapped to the MITRE ATT&CK framework.
• Pre-built and fully customizable response playbooks that execute containment actions in seconds – endpoint isolation, credential revocation, firewall enforcement, cloud account remediation, and automated stakeholder notification.
• Built-in compliance management with continuous monitoring and automated reporting across GDPR, HIPAA, PCI DSS, SOC 2, NIST CSF, ISO 27001, and CMMC – maintaining audit-ready posture without manual effort.
• Flexible deployment options – self-managed for organizations with established SOC teams, or fully managed MDR for those seeking 24/7 expert coverage without building in-house capacity.
• Open architecture with no vendor lock-in, transparent subscription-based pricing, and deployment timelines measured in days – not months.
The result is a security operation that detects threats earlier, responds faster, and continuously strengthens its defenses – without adding headcount or complexity to already stretched teams.
The gap between how fast threats move and how fast organizations can respond is one of the defining challenges in cybersecurity today. Manual, reactive security operations were built for a threat landscape that no longer exists. AI-driven XDR and automated incident response are built for the one that does.
By unifying visibility, applying machine learning at scale, and automating the time-critical work of containment and remediation, these platforms give security teams a genuine capability advantage – not just better tools, but a fundamentally faster and more consistent mode of operation.
Automation does not replace human expertise – it directs it where it matters most. The analysts freed from chasing false positives become the threat hunters, the investigators, the strategic thinkers who build a security program capable of staying ahead of an adversary that never stops evolving.
The organizations that close this gap now will be better positioned for every threat that follows.
