
In today’s threat landscape, cybersecurity teams face an overwhelming challenge: managing dozens of disconnected security tools while defending against increasingly sophisticated attacks. The average enterprise uses 45+ different security solutions, creating data silos, alert fatigue, and dangerous visibility gaps. Enter the centralized security operations platform – a unified solution that consolidates multiple security functions into a single, intelligent ecosystem. These platforms are revolutionizing how organizations detect, analyze, and respond to cyber threats by breaking down silos and empowering security teams with AI-powered automation.
What is a Centralized Security Operations Platform?
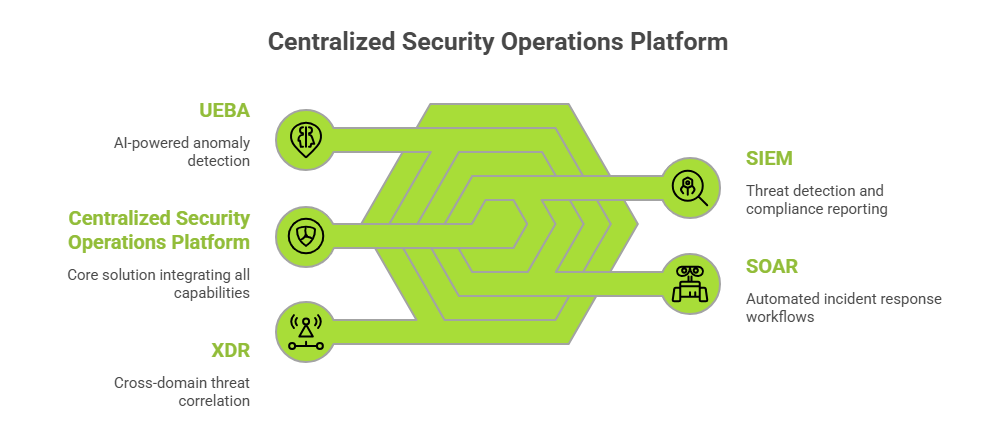
A centralized security operations platform integrates multiple cybersecurity capabilities into a unified solution, eliminating the complexity of managing disparate tools. Unlike traditional SIEM systems that focus solely on log management, modern platforms combine:
This convergence eliminates the need for security analysts to pivot between multiple consoles, manually correlate data, or struggle with integration challenges. Leading platforms deliver this unified approach through AI-driven technology, reducing mean time to detect (MTTD) from hours to minutes and empowering teams to respond faster than ever before.
The Business Case: Why Organizations Are Making the Switch
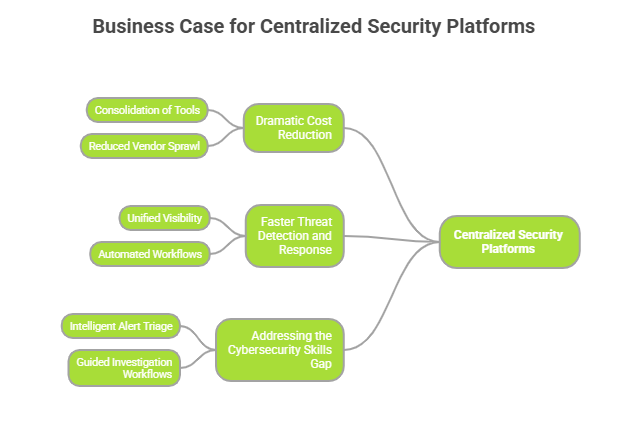
1. Dramatic Cost Reduction: Managing multiple security tools is expensive. Organizations spend millions on licensing, maintenance, and integration costs. A centralized platform consolidates 10-15 point solutions into one, delivering 40-60% cost savings while actually improving security outcomes. By eliminating redundant tools and reducing vendor sprawl, IT budgets can be redirected toward strategic initiatives rather than tool maintenance.
2. Faster Threat Detection and Response
According to industry data breach reports, organizations often take a long time to identify security breaches, allowing attackers to remain undetected for extended periods. Centralized security platforms significantly reduce this gap by correlating data across multiple security domains in real time.By providing unified visibility and automated workflows, these platforms enable security teams to detect threats faster, respond more efficiently, and focus on genuine incidents instead of noise. When every second counts, automated detection and response capabilities can be the difference between a minor security event and a major, organization-wide breach.
3. Addressing the Cybersecurity Skills Gap
With a global shortage of 3.4 million cybersecurity professionals, organizations can’t rely on hiring their way out of security challenges. Centralized platforms leverage AI and automation to multiply the effectiveness of existing teams. Features like intelligent alert triage, guided investigation workflows, and automated response playbooks enable junior analysts to handle incidents that previously required senior expertise
Key Capabilities of Modern Security Platforms
AI-Powered Threat Detection
Advanced platforms use proprietary artificial intelligence engines that go beyond traditional rule-based detection. These systems establish behavioral baselines for every user, device, and application in your environment, then use machine learning to identify anomalies that signal potential threats. This behavior-based approach detects zero-day attacks, insider threats, and advanced persistent threats (APTs) that evade signature-based tools.
Automated Response at Machine Speed
When threats are detected, automated playbooks spring into action immediately isolating compromised endpoints, blocking malicious IPs, disabling user accounts, and gathering forensic evidence without human intervention. Security teams can customize these workflows or leverage pre-built playbooks aligned to the MITRE ATT&CK framework, ensuring consistent and effective responses across all incident types.
Comprehensive Integration Ecosystem
Enterprise environments are complex, requiring seamless integration with hundreds of security and IT tools – from firewalls and endpoint protection to cloud infrastructure and identity management systems. Native connectors and RESTful APIs ensure that your entire security stack works together as a cohesive defense system, not a collection of isolated tools.
Implementation Best Practices
Successfully deploying a centralized security platform requires thoughtful planning:
The Future of Security Operations
As cyber threats evolve, centralized security platforms continue advancing. The next generation will feature:
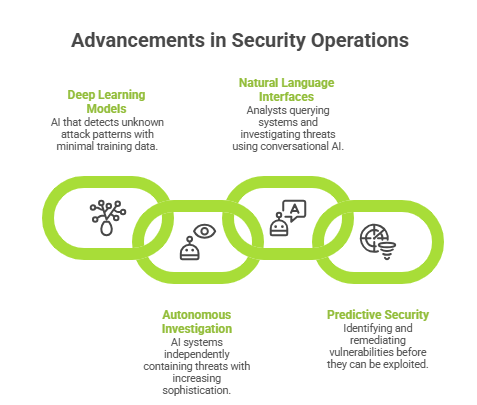
These innovations will continue to push the boundaries of what’s possible in cybersecurity, making security operations more efficient, effective, and proactive.
How Seceon Delivers Comprehensive Security Operations
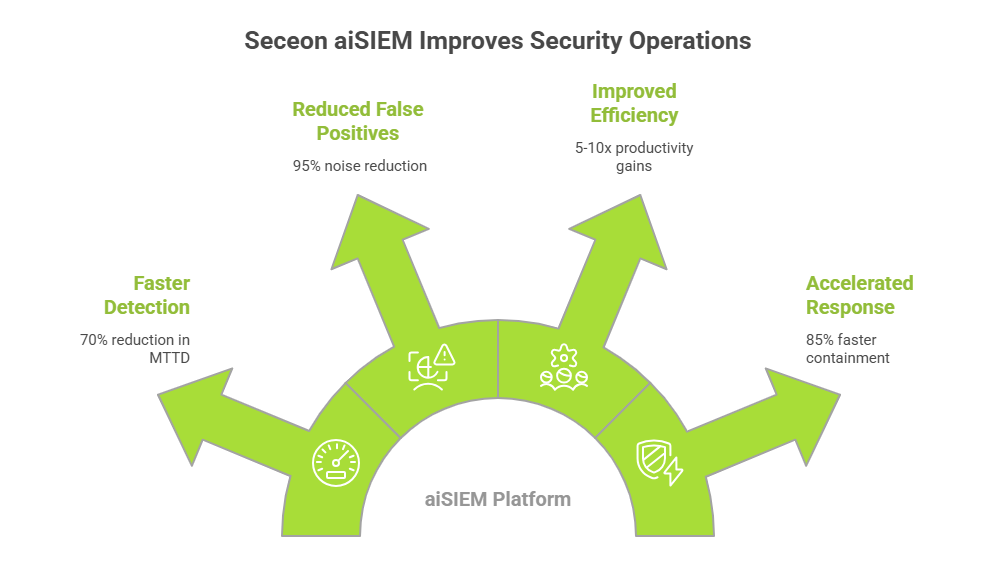
Seceon delivers comprehensive, next-generation security operations through its AI-powered aiSIEM platform, which brings together SIEM, SOAR, UEBA, XDR, and Threat Intelligence Management into a single, centralized solution. By leveraging proprietary self-learning machine-learning algorithms, Seceon continuously analyzes behavior across the enterprise, automatically builds baselines, and detects anomalies without manual rule tuning-enabling accurate detection of advanced threats such as zero-day attacks, APTs, and insider threats.
Key capabilities and outcomes include:
Accelerated incident response: Around 85% faster containment and remediation, reducing overall breach impact.
Built on a cloud-native, enterprise-grade architecture, Seceon scales seamlessly from mid-sized organizations to global enterprises, processing millions of events per second with sub-second detection latency. It supports on-premises, cloud, and hybrid environments and integrates natively with hundreds of security and IT tools, ensuring a unified, silo-free security ecosystem that maximizes existing investments.
Conclusion
The era of managing security through dozens of disconnected tools is ending. Organizations that embrace centralized security operations platforms gain unified visibility, accelerated threat detection, automated response capabilities, and significant cost savings. Most importantly, they empower their security teams to focus on strategic initiatives rather than fighting tool sprawl and alert fatigue.
Whether you’re struggling with compliance requirements, facing a cybersecurity skills shortage, or simply seeking to improve your security posture, a centralized platform delivers measurable results. The question isn’t whether to adopt a centralized security operations platform, but how quickly you can implement one to protect your organization from tomorrow’s threats.
