
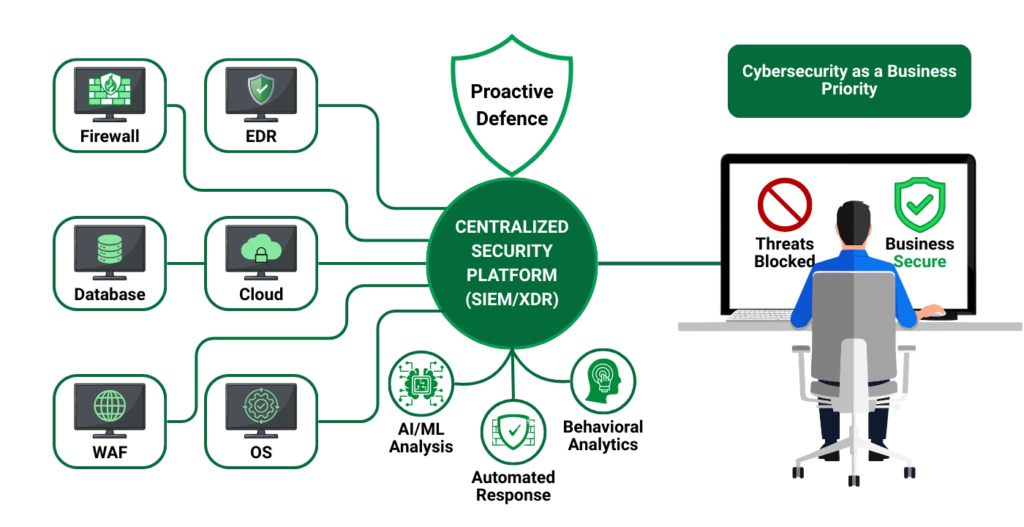
In today’s digital world, cybersecurity is no longer just an IT problem, it is a business survival requirement. Organizations are deploying multiple tools such as firewalls, EDR, databases, operating systems, cloud platforms, WAFs, proxies, and more. However, simply deploying tools does not guarantee security.
What truly matters is how effectively you monitor, correlate, and respond to security events.
Below is a practical, experience-driven view of cybersecurity awareness that every organization should understand.
Modern environments generate massive amounts of security data. Monitoring each tool separately is inefficient, risky, and unsustainable.
A centralized monitoring platform (SIEM/XDR) provides:
Without centralized monitoring, attackers often remain invisible until real damage is done.
Organizations use dozens of security and IT tools:
It is humanly impossible to continuously monitor every individual console. Important alerts get missed, dashboards are ignored, and incidents slip through.
A centralized platform eliminates this problem by bringing all telemetry into one place.
Centralized monitoring often increases EPS (Events Per Second), which can significantly increase SIEM costs.
A more practical approach:
This model provides predictable costs while still allowing full visibility.
Each security tool requires specialized expertise. Hiring experts for:
…is extremely expensive and unrealistic.
Centralized monitoring reduces this dependency by:
A centralized security platform must:
It should not act as a log storage system, but as a detection and response brain for the organization.
One of the biggest threats today is lack of awareness:
Cybersecurity awareness must exist at all levels, not only within the SOC.
Organizations should strictly ask vendors for:
Every security-related activity must generate logs. These logs are the backbone of centralized monitoring and SIEM-based detection.
Many vendors:
Organizations must clearly understand:
Security should not become optional due to licensing.
At a minimum:
Without logs, detection and investigation become impossible, no matter how advanced your SIEM is.
Attackers now use AI to design attack patterns that:
To handle this, centralized security platforms must analyze:
Relying only on static rules is no longer sufficient.
The most important point: organizations must understand the value of cybersecurity.
Every organization should:
Cybersecurity is not about buying more products, it is about visibility, correlation, intelligence, and people.
Centralized monitoring, combined with awareness and skilled professionals, transforms security from a reactive function into a proactive defense strategy.
Tools alone don’t protect organizations.
People, processes, and centralized intelligence do.
