
In June 2025, the cybersecurity world witnessed something extraordinary-a massive data breach that pulled back the curtain on one of North Korea’s most sophisticated intelligence operations. The leaked data from Kimsuky (also known as APT43) revealed thousands of stolen government certificates, complete source code from foreign ministry systems, and custom exploit tools that confirmed what security researchers had long suspected: we’re dealing with a world-class espionage apparatus.
Unlike their counterparts in the Lazarus Group, who chase financial gain, Kimsuky has a singular mission-intelligence collection at scale. Operating under North Korea’s Reconnaissance General Bureau, they’re targeting governments, think tanks, academic institutions, and media organizations worldwide with surgical precision.
Known Aliases: APT43, Emerald Sleet, THALLIUM, Sparkling Pisces
Primary Mission: Strategic intelligence collection supporting North Korean regime objectives
Kimsuky isn’t your typical cybercriminal group. They’re after foreign policy intelligence, diplomatic communications, nuclear negotiations data, academic research, and strategic government information. If your organization deals with policy, security, or Korean Peninsula issues, you’re on their radar.
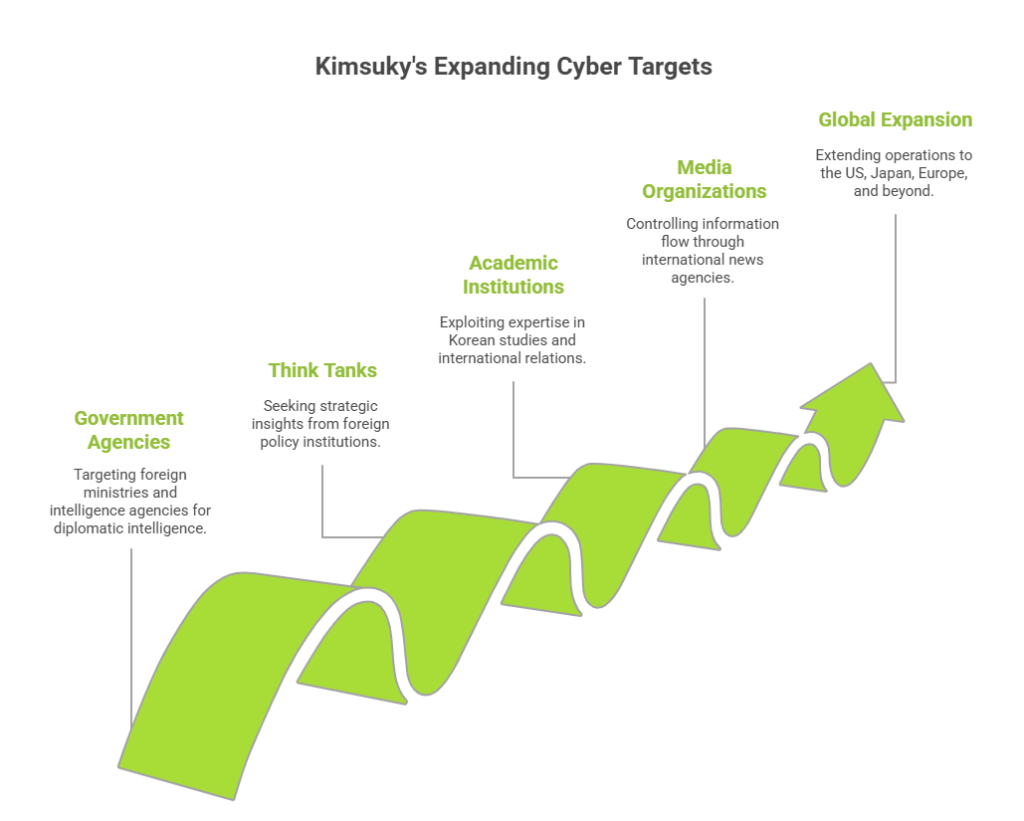
Government Agencies: Foreign ministries, defense departments, presidential offices, and intelligence agencies are prime targets for diplomatic and policy intelligence.
Think Tanks: Foreign policy institutions and defense research centers provide valuable strategic insights that inform government decisions.
Academic Institutions: Korean studies programs, international relations departments, and policy research centers harbor expertise that Kimsuky actively seeks to exploit.
Media Organizations: International news agencies and investigative journalism teams covering North Korea face persistent targeting for information control.
While South Korea remains its primary focus (60% of operations), its reach has expanded dramatically into the United States, Japan, Europe, and even the Middle East and Latin America.
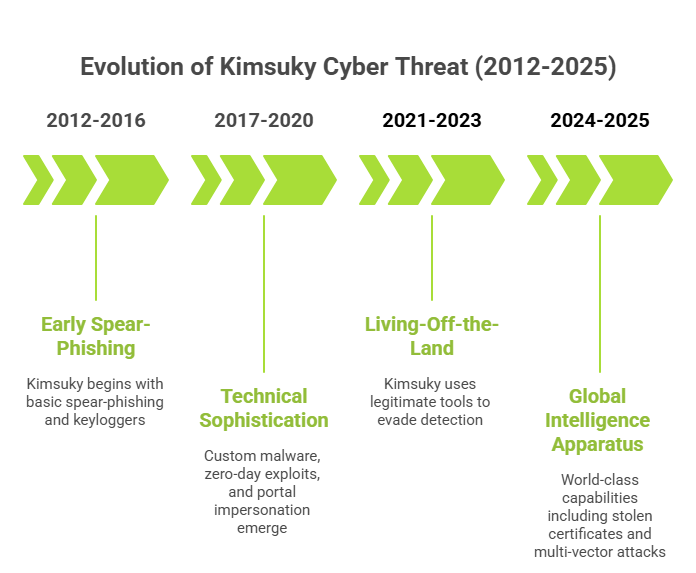
Kimsuky started with relatively unsophisticated spear-phishing campaigns using basic keyloggers and publicly available exploit code.
They developed custom malware like TruRat, began using zero-day exploits, and perfected government portal impersonation techniques.
The group evolved to use “living-off-the-land” techniques, avoiding traditional malware by abusing legitimate system tools that security software struggles to detect.
Today’s Kimsuky demonstrates world-class capabilities, including government impersonation using stolen certificates, months-long social engineering campaigns, and multi-vector attacks combining email, web, and mobile targeting.
Kimsuky’s spear-phishing represents the gold standard of social engineering. They clone official government portals down to the pixel, spoof diplomatic emails using stolen certificates, and impersonate senior officials with frightening accuracy.
For think tanks: Fake policy briefings from prestigious institutions arrive with exclusive research reports and conference invitations that look completely legitimate.
For academics: Research collaboration proposals from prominent scholars and peer review requests appear indistinguishable from real communications.
The weaponization: Malicious Office documents with embedded macros, PDFs with exploits, and browser-based attacks deliver their payload.
Kimsuky excels at fileless attacks that evade traditional security. They use PowerShell for execution, WMI for reconnaissance, and legitimate Windows binaries for malicious purposes-all tools already present on your systems that security software trusts by default.
Unlike ransomware gangs seeking quick payoffs, Kimsuky plays the long game. Their operations span months or years with extremely stealthy activities including slow data exfiltration, infrequent command-and-control communications, and dormant periods that blend seamlessly with normal user behavior.
TruRat: An advanced remote access trojan with comprehensive capabilities from remote command execution to credential theft, featuring process injection and anti-debugging techniques.
MECHANICAL Keylogger: Sophisticated keystroke capture specifically targeting email clients, messaging applications, and VPN clients with encrypted log transmission.
Tomcat Kernel Rootkit: Kernel-level persistence that hides processes, files, and network connections while surviving reboots and resisting removal.
SpawnChimera: A modular malware platform with a plugin architecture that dynamically extends functionality through encrypted plugin storage.
Messages perfectly mimic legitimate communications using stolen credentials and exploit trusted relationships. Traditional email filters based on keywords and sender reputation can’t detect this level of sophistication.
Fileless malware residing only in memory and abuse of native Windows tools leave no signature to detect. Traditional antivirus is completely blind to these living-off-the-land techniques.
Activities spanning months with slow data exfiltration and infrequent communications slip under traditional SIEM alert thresholds. Manual analysis cannot correlate events across such extended timelines.
Stolen credentials provide authorized access through legitimate VPN connections and valid certificates. Perimeter security cannot distinguish between legitimate users and attackers using stolen credentials.
Organizations with siloed security tools lack visibility across email, endpoints, network, and cloud environments-missing the comprehensive attack picture that Kimsuky exploits.

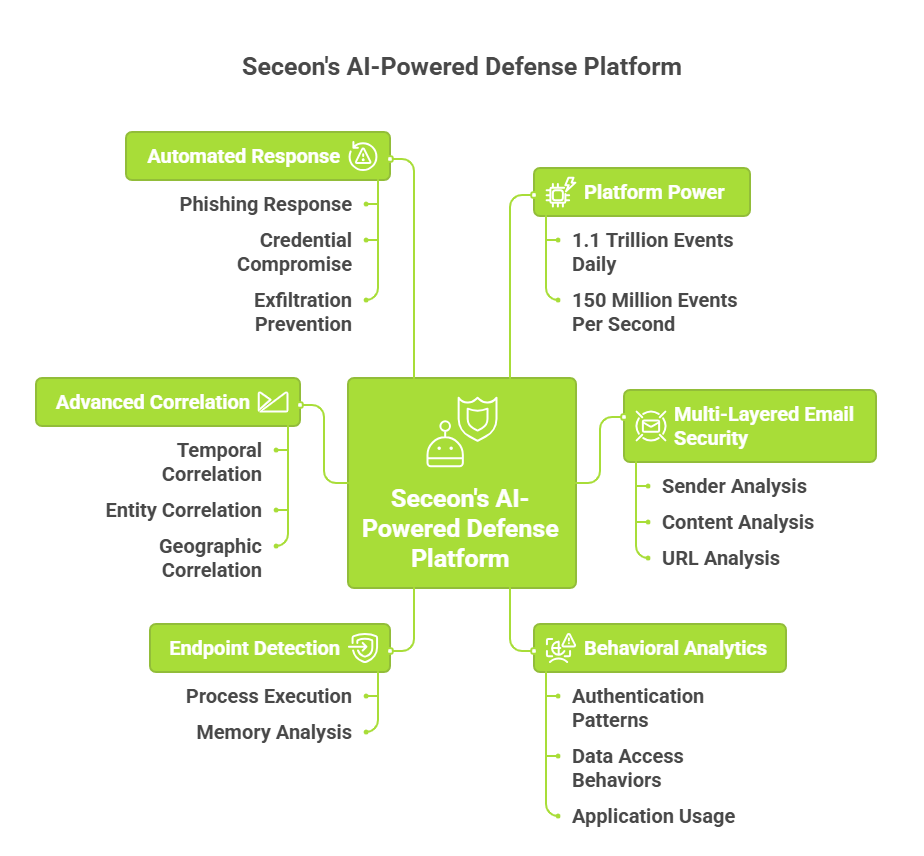
The Seceon Open Threat Management Platform monitors 1.1 trillion security events daily across 8,800+ customers, processing 150 million events per second with 70+ integrated threat intelligence feeds and Day 1 effectiveness.
Sender Analysis: Domain age and reputation checking, combined with certificate validation, detects sophisticated spoofing even when DKIM/SPF/DMARC are valid.
Content Analysis: Natural language processing identifies social engineering indicators, urgency manipulation, and government impersonation with linguistic analysis.
URL Analysis: Portal cloning detection, typo-squatting identification, and real-time threat intelligence correlation catch malicious links.
Seceon’s AI-powered UEBA establishes behavioral baselines for authentication patterns, data access behaviors, and application usage-then flags anomalies like impossible travel, off-hours access, and unusual data volumes.
Detection Example: When a government analyst’s account logs in at 3 AM from a foreign IP and downloads 500 documents in 10 minutes, Seceon correlates temporal, geographic, and behavioral anomalies into a “Compromised Account – Potential Exfiltration” alert.
Seceon’s aiXDR monitors process execution, parent-child relationships, and command-line arguments while detecting living-off-the-land abuse of PowerShell, WMI, and legitimate tools. Memory analysis catches in-memory malware and credential dumping.
Seceon’s correlation engine links events across time (weeks to months), entities (users, systems, assets), geography (attack infrastructure), and TTPs (known Kimsuky tactics) to reconstruct complete campaign narratives. Campaign Example: From initial spear-phishing (Day 1) through execution, credential access, discovery, lateral movement, collection, and exfiltration (Days 1-90), Seceon correlates all stages into a single comprehensive incident with a complete attack timeline and response recommendations.
Phishing Response: Quarantine email, block sender/domain, extract indicators, update firewall rules, and notify teams-all within 2 minutes versus 2-4 hours manual response.
Credential Compromise: Force password reset, terminate sessions, enforce MFA, isolate systems, and generate forensics-credential invalidation within 1 minute.
Exfiltration Prevention: Block destination, quarantine source, terminate processes, capture forensics, and classify data impact-exfiltration halted within 30 seconds.
Government Agency: 15 prevented spear-phishing campaigns in 6 months, zero successful credential compromises, 99.5% reduction in false positives, 90% reduction in analyst workload.
Think Tank: 8 detected Kimsuky attempts, zero successful research data breaches, 95% alert volume reduction, enabled secure international collaboration.
University: 12 prevented faculty compromises, zero thesis/dissertation theft, 70% cost reduction, improved academic collaboration security.
Organizations without comprehensive Kimsuky defense face severe consequences beyond just technical compromise.
Intelligence Loss: Theft of classified documents, sensitive policy research, diplomatic communications, and academic intellectual property directly supports adversarial intelligence operations.
Strategic Impact: Compromised decision-making, loss of diplomatic advantage, damaged international relationships, and impaired collaboration create long-term strategic disadvantages.
Financial Damage: Incident response ($500K-$2M), legal costs ($250K-$1M), lost productivity ($1M-$5M), and immeasurable reputation damage compound over time.
Kimsuky represents an elite intelligence threat operating at nation-state capability levels. The June 2025 breach confirmed the scale and sophistication of their operations targeting governments, think tanks, academic institutions, and media organizations worldwide.
The Reality: Traditional security is insufficient against sophisticated social engineering, living-off-the-land techniques, and long-term persistent operations.
The Solution: AI-powered behavioral analytics with comprehensive visibility across email, endpoints, network, and cloud, backed by automated response at machine speed.
The Choice: Organizations in high-risk sectors cannot afford inadequate protection. Kimsuky’s persistent targeting makes comprehensive defense mandatory, not optional.
The intelligence collection threat is real, sophisticated, and persistent. The defensive solution exists. The decision to implement comprehensive protection is yours.
