
Security Operations Centers (SOCs) were never designed for today’s threat landscape. Cloud sprawl, hybrid workforces, encrypted traffic, and AI-driven adversaries have pushed traditional SOC models beyond their limits. Analysts are inundated with alerts, investigations are manual and time-consuming, and response often comes too late.
Despite investments in SIEM, EDR, and SOAR, many organizations still struggle with:
This reality has led to a fundamental rethinking of security operations – giving rise to the next-generation SOC automation platform.
Legacy SOC architectures are largely alert-centric and rule-driven. They depend on static correlation rules, known indicators of compromise, and human analysts to manually connect the dots.
Modern attackers exploit these limitations by:
As a result, SOC teams spend the majority of their time triaging noise instead of stopping real threats. More tools do not solve this problem – better intelligence and automation do.
A next-gen SOC automation platform is not just an upgraded SIEM or a bolt-on SOAR solution. It represents a new operational model that unifies detection, investigation, and response through intelligence and automation.
The core shift is from:
This approach aligns security operations with how attacks actually unfold in modern environments.
At the heart of next-gen SOC automation lies behavioral analytics.
Instead of analyzing events in isolation, the platform continuously models the normal behavior of:
Deviations from these baselines – even subtle ones – are evaluated over time to identify malicious intent. This enables detection of:
Behavior-driven detection significantly reduces false positives while improving threat fidelity.
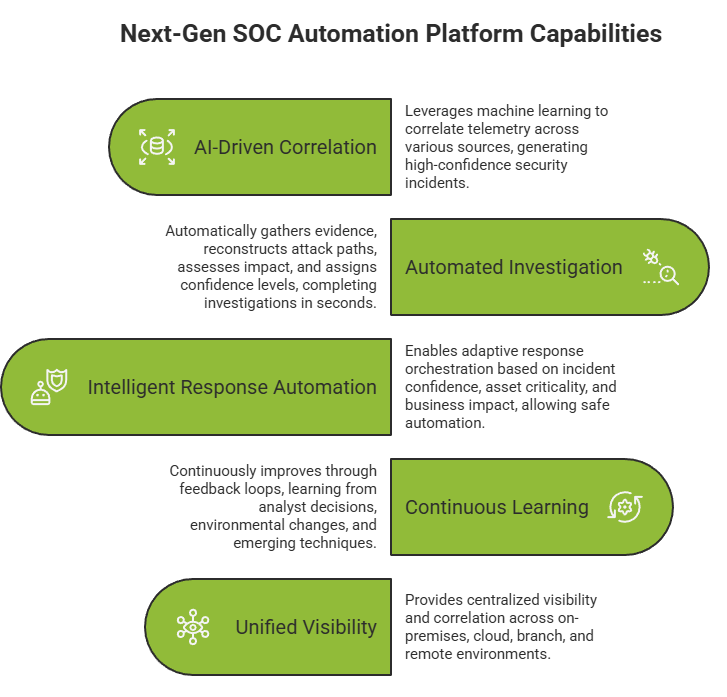
Next-gen platforms leverage machine learning to correlate telemetry across:
Rather than producing thousands of alerts, the system generates high-confidence security incidents, enriched with context, risk scoring, and attack narratives.
One of the most impactful advancements is machine-led investigation.
A next-gen SOC automation platform can automatically:
Investigations that once took hours are completed in seconds – allowing analysts to focus only on validated threats.
Unlike traditional SOAR tools that rely on rigid playbooks, next-gen platforms enable adaptive response orchestration.
Response actions are determined based on:
This allows safe automation such as:
Human oversight remains available, but automation handles the speed and scale attackers exploit.
Next-gen SOC platforms continuously improve through feedback loops.
They learn from:
Over time, the SOC becomes more accurate, faster, and less dependent on individual expertise, addressing one of the biggest operational challenges in cybersecurity today.
Modern enterprises operate across on-premises, cloud, branch, and remote environments. Next-gen SOC automation platforms provide centralized visibility and correlation across these domains.
Identity-centric analytics ensure that users – not just IPs or devices – are at the center of security decisions, eliminating blind spots created by tool silos.
Seceon is purpose-built to enable this next-generation SOC model.
The Seceon platform delivers:
By integrating detection, investigation, and response into a single platform, Seceon enables SOC teams to move from alert management to outcome-driven security operations.
For enterprises and MSSPs, Seceon helps:
Organizations adopting next-gen SOC automation platforms consistently achieve:
This enables CISOs to shift conversations from tool metrics to security outcomes and resilience.
As attackers increasingly leverage automation and AI, security operations must evolve accordingly. The future SOC will be:
Next-generation SOC automation platforms – powered by intelligence and platforms like Seceon – are becoming the foundation of modern cyber defense.
Security is no longer about collecting more data or generating more alerts.
It is about understanding behavior, reducing uncertainty, and acting decisively at machine speed.
The next-generation SOC automation platform – enabled by Seceon -makes that possible.
