
North Korea’s state-sponsored Lazarus Group has transcended traditional cybercrime. Operating under the Reconnaissance General Bureau (RGB), this threat actor has become a major driver of global financial cybercrime, generating over an estimated $2.1 billion in cryptocurrency theft in the first half of 2025 alone. These attacks have been linked by multiple industry and government reports to North Korea’s broader strategic objectives, elevating the risk from a financial loss to a broader geopolitical security concern.
This post breaks down Lazarus’s advanced tactics and demonstrates how the Seceon Open Threat Management (OTM) Platform functions as a defensive tool that helps organizations detect, investigate, and respond to elements of these attacks.
Lazarus (also known as APT38, Bluenoroff, and Hidden Cobra) has dramatically increased its sophistication over time. They no longer rely on simple malware but employ multi-stage, cross-platform attacks that resemble the tradecraft of advanced espionage units.
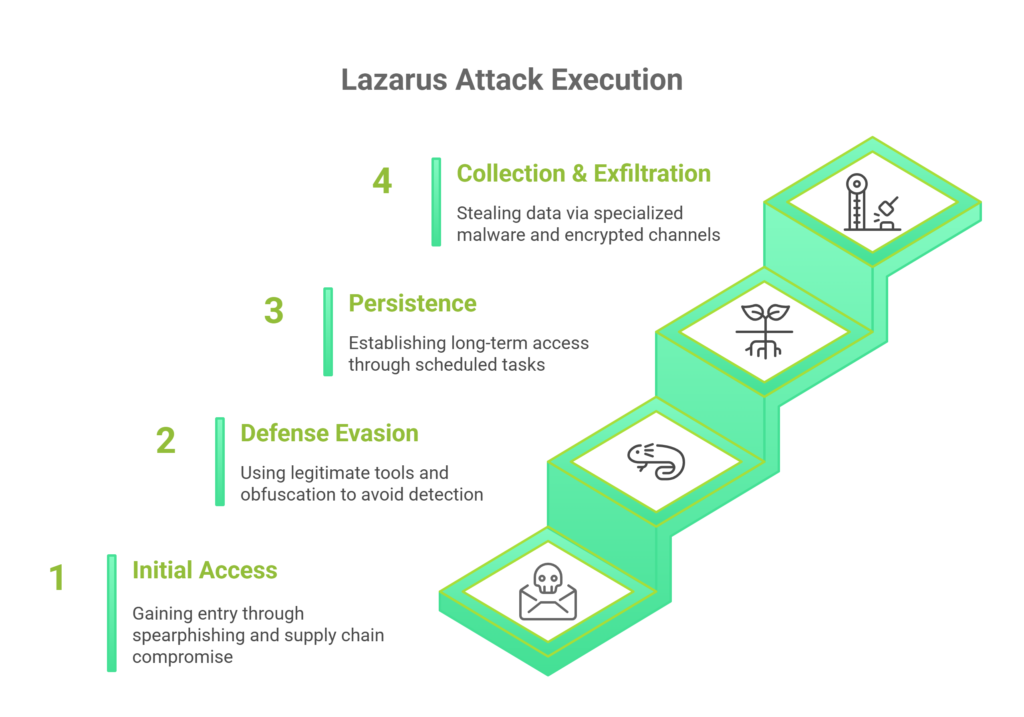
Lazarus TTPs map extensively to the MITRE ATT&CK Framework, with a heavy focus on evasion and long-term persistence:
Legacy security solutions – built on signatures, static rules, and manual correlation – struggle against Lazarus Group’s speed, scale, and stealth.
The Seceon Platform as a Defensive Tool in a Unified Security Strategy
The Seceon Open Threat Management (OTM) Platform is designed to serve as a centralized detection and response layer that supports organizations in identifying, correlating, and responding to advanced attack behaviors associated with threats like Lazarus.
Seceon applies behavioral analytics to establish baselines of normal user and entity behavior. This enables earlier identification of anomalies that commonly appear during sophisticated intrusions.
Detection Example:
A developer account accesses sensitive cryptocurrency code at an unusual hour, downloads a disproportionately large data set, and initiates network connections to previously unseen foreign IPs.
Result:
Rather than treating these as isolated low-priority alerts, Seceon correlates them into a single high-risk investigation item for security teams to review with full operational context.
The platform is designed to help reduce visibility gaps across diverse environments:
Seceon provides automation capabilities designed to help security teams respond more quickly once threats are identified.
| Action | Typical Manual Process | Seceon-Enabled Automation |
| Threat Detection | Hours to Days | Near real time |
| Containment Action | 1-2 hours | Seconds via playbooks |
| Full Response Cycle | 4-24 hours | Minutes, depending on policy |
Automation playbooks can assist with actions such as:
These controls help reduce attacker dwell time and limit blast radius, even in fast-moving intrusion scenarios.
Seceon is designed to support detection and response across attack phases commonly used by advanced threat groups:
The operational model demonstrated by Lazarus Group reflects a convergence of nation-state capability and financially motivated cybercrime at unprecedented scale. The risks now extend beyond individual organizations to broader economic and geopolitical stability.
Organizations in high-risk sectors – such as cryptocurrency, financial services, and critical infrastructure – benefit from transitioning away from siloed, manual security operations toward more unified, analytics-driven defense models. Platforms such as Seceon’s OTM contribute to this shift by supporting faster detection, broader visibility, and more coordinated response across security teams.
Rather than assuming any single platform can stop a nation-state adversary outright, the goal is to materially reduce exposure, shorten attacker dwell time, and improve the organization’s ability to defend against the tactics, techniques, and behaviors commonly used by advanced threat groups like Lazarus.
