
The Middle East is undergoing one of the fastest digital transformations in the world. National initiatives such as Saudi Vision 2030, Kuwait Vision 2035, and the UAE Digital Government Strategy are fueling large-scale modernization across every sector. However, as this progress accelerates, the region faces a parallel rise in cyber threats, pushing cybersecurity to the forefront of national and enterprise priorities.
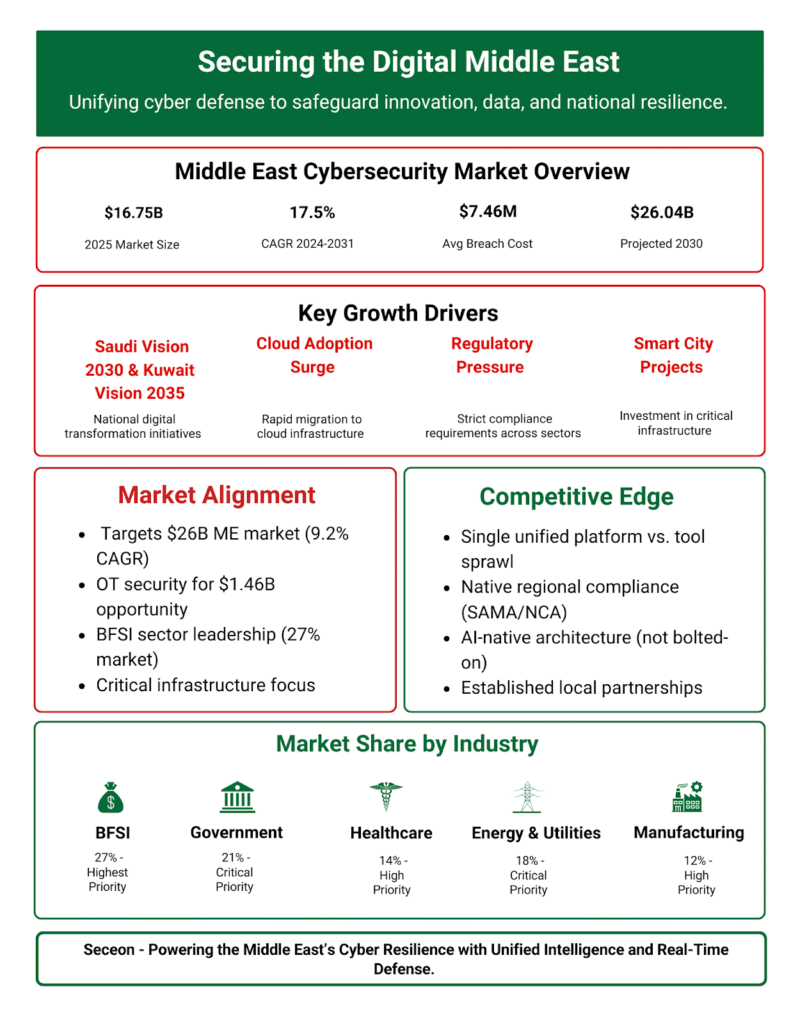
The Middle East cybersecurity market is valued at $16.75 billion (2025) and projected to reach $26.04 billion by 2030, growing at a 9.2% CAGR. The average breach cost has reached $7.46 million, one of the highest globally, a reminder that digital advancement must be matched by strong, adaptive cyber defenses.
A recent analysis of 50+ Middle East organizations revealed a troubling pattern – most enterprises operate with 8-12 disconnected security tools, manage three dashboards, retain two compliance consultants, and still face over 200 daily alerts. Despite spending $2-5 million annually on cybersecurity, many remain vulnerable and non-compliant even after 18 months.
The region’s growth is being driven by four major trends:
By industry share, BFSI (27%) leads in cybersecurity investment, followed by Government (21%), Energy & Utilities (18%), Healthcare (14%), Manufacturing (12%), and others. Each sector faces unique risks, but all share one common goal – achieving resilience through intelligence.
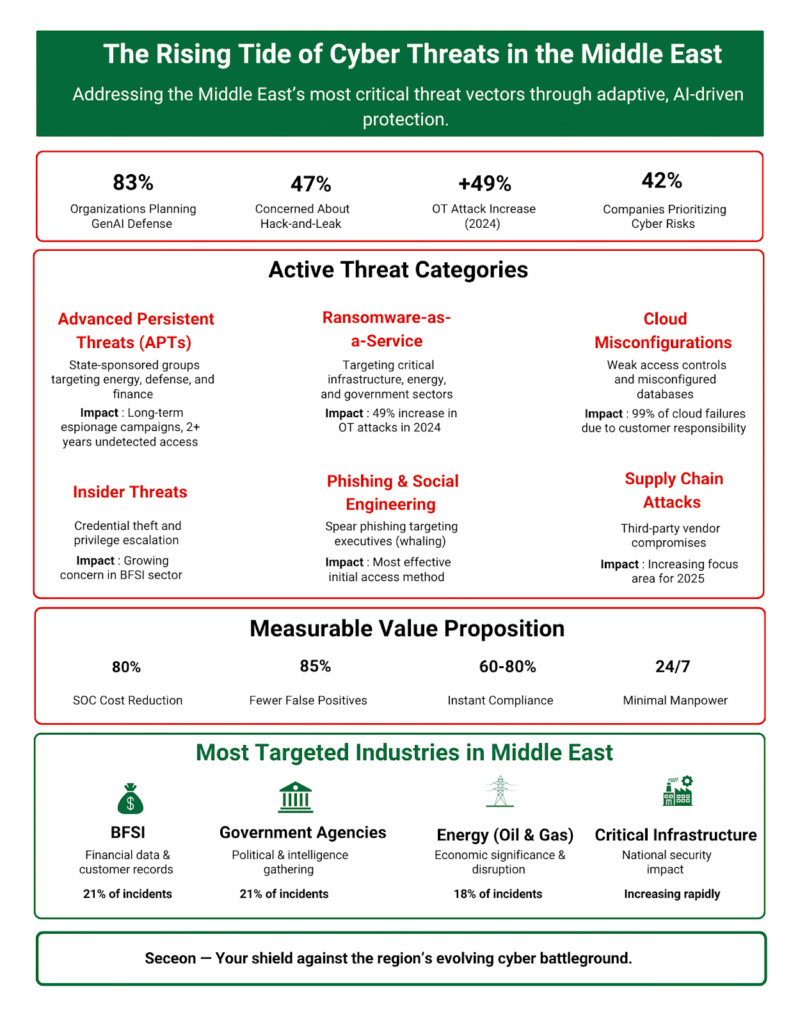
As digital ecosystems grow, so does the threat exposure. 83% of organizations admit struggling to keep pace with the evolving landscape, while OT attacks surged 49% in 2024, especially against energy and utilities. 47% of enterprises cite data leakage as a top concern, and 42% now treat cyber risk as a board-level issue.
Top active threats include:
One CISO in Dubai summarized the regional frustration:
“We spent $3 million on tools, we’re still not compliant with SAMA, we still got breached, and my team is exhausted.”
This isn’t a tool problem; it’s an architecture problem. Attackers exploit the gaps between systems, while security teams drown in noise instead of intelligence.
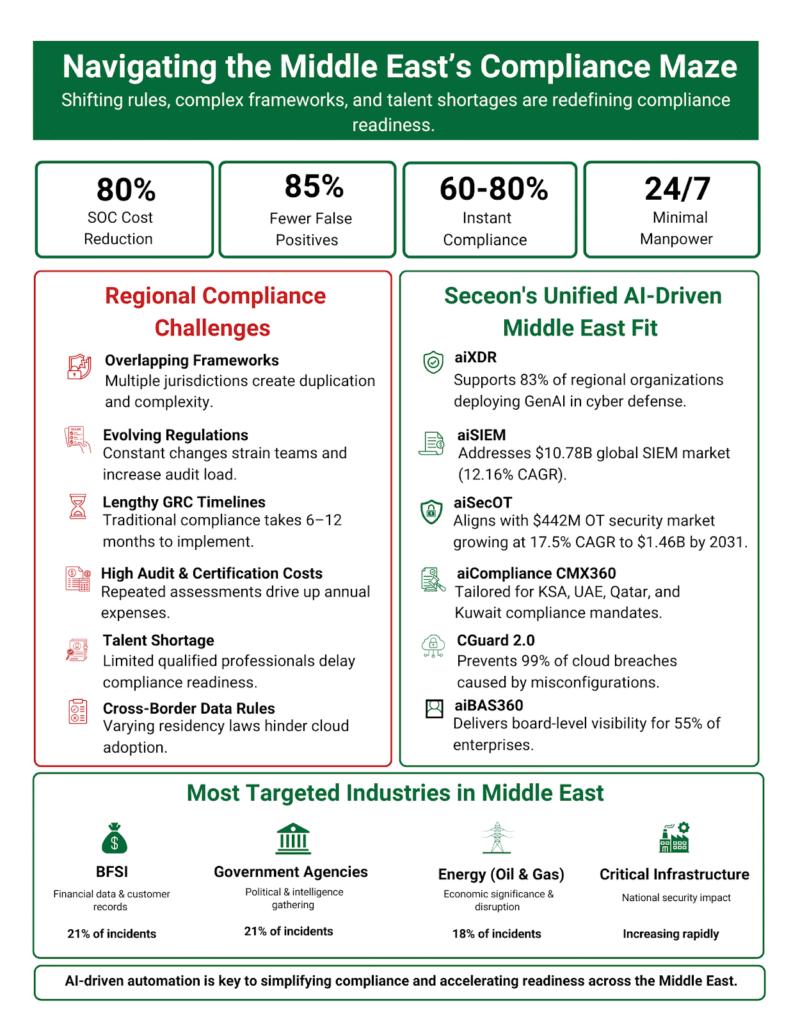
The Middle East’s cybersecurity frameworks are among the most dynamic in the world. Each nation enforces its own controls while aligning with global standards like ISO 27001, PCI-DSS, GDPR, HIPAA, SOC 2, NIST, and CMMC 2.0.
While these policies have strengthened regional resilience, compliance remains time-consuming, averaging 6-12 months. Traditional GRC approaches can’t keep up with today’s regulatory speed.

Seceon addresses this challenge with its AI-driven unified platform, eliminating tool sprawl and replacing silos with intelligence. It merges threat detection, response automation, and compliance validation into a single, intelligent ecosystem.
A compliance analytics platform offering deep insights, real-time dashboards, and automated audits. Supports CMMC, HIPAA, PCI-DSS, NIST, and GDPR, helping organizations achieve 72% faster compliance readiness while cutting audit fatigue.
An AI-powered Breach & Attack Simulation engine that continuously tests and validates defenses. Provides risk scoring, SIEM integration, and executive summaries, used by 55% of enterprises to quantify and improve cyber posture.
A cloud-native protection suite combining CWPP, CSPM, and CNAPP capabilities. Delivers multi-cloud visibility, automated remediation, and Kubernetes-native security, mitigating 90% of misconfiguration-based risks.
A next-generation AI-driven SIEM that replaces rule-based detection with machine learning, correlating events across IT, OT, and cloud environments in real time.
Provides end-to-end protection for endpoints, networks, and cloud workloads, ensuring unified visibility across the enterprise.
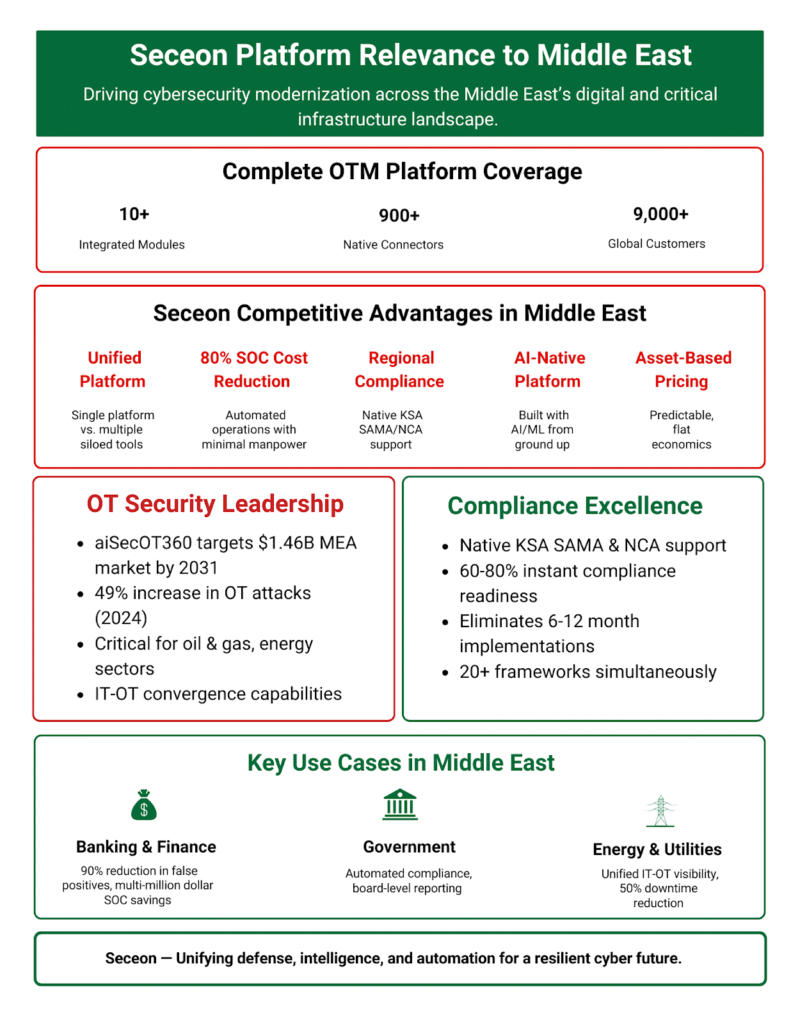
Built for the Middle East’s expanding OT security market ($442M → $1.46B by 2031), it protects industrial control and SCADA environments from sophisticated attacks.
Delivers instant compliance readiness (60-80%) for SAMA, NCA, and 18+ global frameworks, reducing compliance cycles from months to weeks.
Seceon’s unified architecture replaces complexity with clarity. Customers typically achieve:
Its regional advantage includes native support for SAMA, NCA, NESA, and CITRA frameworks and deep partnerships with Tech First Gulf (TFG) and AZCOM IT Distribution, ensuring localized deployment and support. Its AI-native design aligns perfectly with the region’s move toward GenAI adoption as 83% of Middle East organizations now leverage AI for cyber defense.
With digital transformation reaching into energy, oil, and utilities, OT security has become critical.
Seceon’s OT suite bridges IT and OT with:
By integrating IT-OT convergence, Seceon enables resilient protection for the industries powering Vision 2030.
Seceon delivers measurable outcomes, simplifying security while enhancing resilience.
The Middle East cybersecurity market is on track to hit $26 billion by 2030. Two kinds of organizations are emerging:
1. Those managing 15+ tools, overwhelmed by complexity and cost.
2. Those adopting unified, AI-driven platforms that simplify, automate, and protect.
Seceon helps enterprises shift from reactive defense to proactive intelligence aligning with the region’s drive for digital sovereignty and cyber self-reliance.
Threat groups like APT33 and APT34 don’t use ten tools; they use one coordinated strategy. Defenders must do the same. The future belongs to organizations that unify their defenses, automate compliance, and build intelligence into their core.
Through platforms like aiSecurity BI360, aiBAS360, CGuard 2.0, aiSIEM, aiSecOT360, and aiCompliance CMX360, and strong partnerships with TFG and AZCOM IT Distribution Seceon is helping enterprises across the Middle East achieve true cyber resilience.
The question isn’t whether to modernize, it’s whether your organization will lead the transition or react to the breach.