In today’s digital-first world, cyber threats are evolving faster than ever. Traditional, rule-based detection tools can no longer keep pace with the sophistication of modern attacks. Organizations need a smarter, adaptive, and automated approach — this is where Machine Learning (ML)-powered anomaly detection comes in.
This technology lies at the heart of next-generation Security Operations Centers (SOCs), enabling real-time visibility, faster detection, and proactive defense. Let’s explore how it works, why it matters, and how Seceon’s Unified Platform delivers world-class anomaly detection with measurable results.
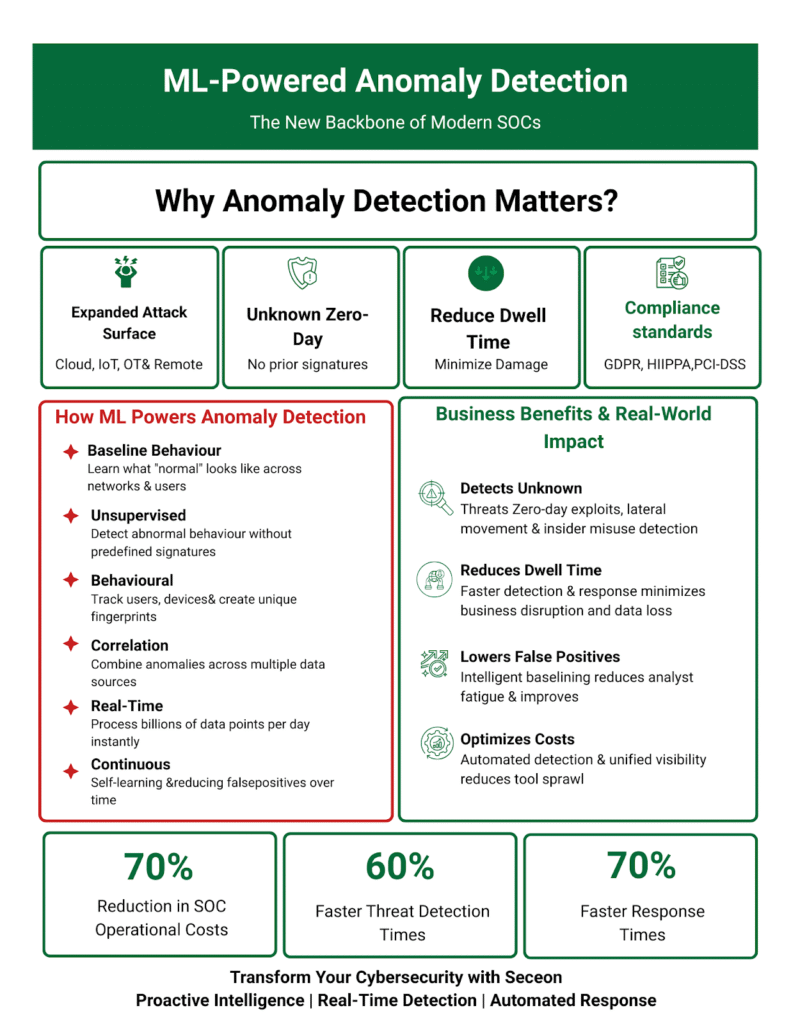
Anomaly detection is the process of identifying patterns in data that deviate from normal or expected behavior. In cybersecurity, it means spotting unusual network activity, suspicious user logins, or unauthorized data transfers — before these deviations turn into breaches.
Why it’s critical for modern enterprises:
In short, anomaly detection allows security teams to detect unknown threats early, protect critical assets, and reduce business risk.
ML brings intelligence, adaptability, and automation to anomaly detection. It learns normal behavior across networks, users, and devices — and flags anything that deviates.
Machine learning models analyze large volumes of telemetry data to understand what “normal” looks like. Once baseline patterns are built, any deviation (for example, a sudden spike in data transfers or a login from an unfamiliar location) is flagged as suspicious.
Since many attacks have no labeled examples, ML uses clustering and outlier detection to identify abnormal behavior without relying on predefined signatures.
ML tracks the behavior of users, devices, and applications — creating unique behavioral fingerprints. When entities deviate from their normal pattern, it triggers alerts, giving the SOC team actionable insights.
By combining anomalies across multiple data sources (network, endpoint, identity, and cloud), ML can recognize complex, multi-vector attack patterns that static rules would miss.
As new threats appear and environments evolve, ML models refine themselves — reducing false positives and increasing accuracy over time.
ML-driven systems can process billions of data points per day, delivering real-time detection and scoring even in large, distributed networks.
This end-to-end process ensures that every deviation is analyzed in context, not isolation — turning raw data into actionable intelligence.
ML identifies subtle deviations in user or system behavior, helping discover zero-day exploits, lateral movement, and insider misuse.
Organizations detect and respond to threats faster, minimizing business disruption and data loss.
Intelligent baselining ensures fewer unnecessary alerts, reducing analyst fatigue and improving SOC efficiency.
Continuous monitoring ensures readiness for audits and regulatory frameworks like GDPR, HIPAA, and PCI-DSS.
Automated detection and unified visibility reduce tool sprawl, lowering total cost of ownership (TCO).
Seceon’s Open Threat Management (OTM) Platform provides a unified view across networks, users, devices, and applications — eliminating data silos and enabling comprehensive anomaly detection.
At Seceon’s core lies a self-learning AI/ML engine that continuously adapts to evolving threats. It performs deep behavioral analytics, correlates anomalies across multiple data sources, and automatically detects deviations that traditional tools miss.
Seceon’s patented Dynamic Threat Modeling technology correlates user, network, and endpoint data to create a real-time risk picture. This allows detection of multi-stage attacks that unfold gradually across the environment.
Seceon continuously monitors traffic flows, device communications, and application behaviors. It detects unusual outbound traffic, exfiltration attempts, or protocol misuse — key indicators of compromise.
Detection is just the beginning. Seceon automates the response process — isolating infected hosts, blocking malicious traffic, and generating reports for analysts. This ensures faster mitigation with minimal human intervention.
Whether for large enterprises or managed security service providers (MSSPs), Seceon’s platform is built to scale. Multi-tenant architecture, flexible deployment options, and predictable licensing models make it ideal for diverse use cases.
Organizations using Seceon report:
These outcomes translate to measurable value — reduced risk, faster ROI, and higher team productivity.
ML-powered anomaly detection is transforming cybersecurity from reactive defense to proactive intelligence. By learning what’s normal and instantly identifying deviations it allows organizations to stop attacks before they cause damage.
Seceon’s Unified Threat Management Platform brings this intelligence to life — combining machine learning, dynamic threat modeling, behavioral analytics, and automation to deliver faster, more accurate detection with lower operational costs.
For organizations seeking to modernize their SOC and future-proof their cybersecurity operations, Seceon stands as the benchmark for ML-powered anomaly detection.