
How Artificial Intelligence Transforms Security Operations
Security Operations Centers (SOCs) face a growing operational challenge: overwhelming alert volumes. Modern enterprise environments generate thousands of security notifications daily across endpoint, network, identity, cloud, and application layers. This continuous stream of alerts creates what the industry describes as alert fatigue, a condition where analysts are overwhelmed by volume, leading to slower investigations, missed threats, and operational inefficiencies.
Alert fatigue is not simply an inconvenience. When security teams must sift through excessive noise, distinguishing real threats from false positives becomes increasingly difficult. Over time, this erodes response effectiveness and introduces risk into the organization’s security posture.
Artificial intelligence (AI) and machine learning (ML) are reshaping how security teams manage this challenge. By automating analysis, improving prioritization, and surfacing high-confidence incidents, AI enables SOC teams to focus on meaningful threats instead of repetitive triage.
The Alert Fatigue Challenge
Security infrastructures are composed of multiple specialized tools-SIEM, EDR, NDR, firewalls, cloud security platforms, identity systems, email gateways, and more. Each generates its own alert stream, often without shared context or intelligent correlation.
As environments grow more complex, alert volume scales accordingly. A significant portion of alerts generated across enterprise environments turn out to be low-risk or false positives. However, each alert still demands review, investigation, or enrichment.
This creates several operational issues:
Fragmented tooling and excessive noise reduce visibility rather than improving it. Attackers increasingly exploit this overload, blending malicious activity into routine operational noise.
Operational and Business Impact
The impact of alert fatigue extends beyond the SOC.
High alert volumes contribute to analyst stress and burnout in an already constrained cybersecurity talent market. Retaining skilled professionals becomes difficult when their daily work consists largely of repetitive alert triage.
From a business perspective, delayed detection and response can significantly increase breach impact. The longer a threat remains undetected, the greater the potential operational disruption, financial damage, and reputational harm.
Organizations need a scalable way to reduce noise without reducing visibility.
Artificial intelligence addresses alert fatigue through multiple complementary capabilities that improve both efficiency and accuracy.
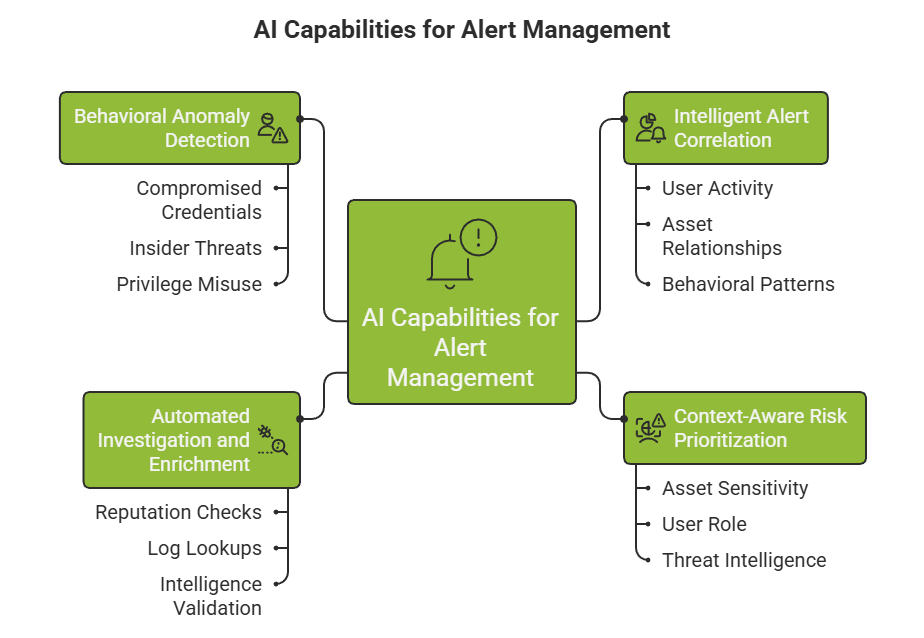
AI-powered systems automatically identify relationships between alerts generated across different tools and timeframes. Instead of presenting isolated notifications, machine learning models correlate related events into consolidated incidents that reflect an entire attack chain.
By analyzing user activity, asset relationships, behavioral patterns, and network connections, AI reduces alert noise while preserving investigative depth. Analysts receive structured incidents rather than disconnected signals.
Not all alerts represent equal risk. AI-driven prioritization engines evaluate alerts using contextual factors such as:
This contextual scoring ensures that security teams focus first on activity that presents the highest operational or business risk. Over time, models refine prioritization based on analyst feedback and environmental learning.
Many investigative steps follow repeatable workflows-reputation checks, log lookups, behavior comparisons, historical correlation, and intelligence validation.
AI-driven automation performs these enrichment steps instantly and consistently. Alerts reaching analysts already contain relevant context, related activity, and recommended actions. This reduces manual triage effort and improves investigative consistency.
Signature-based systems detect known threats. AI-based behavioral analytics detect deviations from normal patterns.
Machine learning establishes baselines for users, endpoints, applications, and network activity. When behavior diverges meaningfully from expected patterns, the system flags anomalies for review.
This approach strengthens detection of:
Because behavioral models continuously adapt, they reduce unnecessary noise while maintaining detection sensitivity.
Organizations adopting AI-driven security operations typically observe improvements such as:
Rather than expanding headcount to keep pace with alert growth, teams scale operational capability through automation and intelligent analytics.
The Shift from Reactive Alert Handling to Autonomous Security Operations
Reducing alert fatigue is not simply about filtering notifications – it requires rethinking how security operations function at their core. Traditional SOC models rely heavily on manual triage, rule-based detection, and tool-by-tool analysis. As digital environments grow more distributed and attack techniques become more adaptive, this approach struggles to scale.
AI introduces a structural shift. Instead of responding to alerts in isolation, modern security operations platforms continuously analyze behavioral patterns, correlate cross-domain activity, and automate investigative workflows in real time. The goal is not just efficiency – it is operational precision.
By embedding intelligence directly into detection, prioritization, and response processes, organizations move from overwhelmed alert management to autonomous, context-driven security operations. This shift enables SOC teams to operate proactively, reduce cognitive overload, and focus on high-impact threat mitigation rather than repetitive triage.
Seceon’s aiSIEM platform is built specifically to reduce alert fatigue while strengthening detection and response.
The platform correlates activity across infrastructure layers, identifying attack sequences that would otherwise appear as unrelated alerts. This consolidation provides full incident visibility and eliminates redundant investigation efforts.
Integrated orchestration capabilities enable automated containment and remediation workflows. Actions such as isolating endpoints, blocking malicious traffic, or disabling compromised accounts can be executed rapidly, minimizing attacker dwell time.
Built-in User and Entity Behavior Analytics (UEBA) capabilities establish dynamic baselines and detect anomalous activity. This behavioral layer enhances detection of advanced and insider threats while minimizing unnecessary alert generation.
By integrating SIEM, SOAR, and behavioral analytics within a single architecture, Seceon eliminates data silos. Security teams gain correlated visibility across endpoints, networks, cloud environments, and identity systems without managing fragmented tools.
Successful AI adoption depends on thoughtful execution:
When implemented correctly, AI enhances-not replaces-human expertise.
Alert fatigue remains one of the most pressing challenges in modern security operations. As digital environments expand and threat sophistication increases, manual investigation models cannot scale effectively.
AI-powered platforms provide a sustainable path forward. Through intelligent correlation, contextual prioritization, automation, and behavioral analytics, organizations can transform security operations from reactive alert handling to focused threat management.
By reducing noise and elevating signal, AI enables SOC teams to operate with clarity, speed, and confidence-strengthening security posture while improving operational resilience.
