
The modern cybersecurity landscape is defined by relentless complexity. Today’s Security Operations Centers (SOCs) face an unprecedented volume of threats – from sophisticated ransomware campaigns and supply chain attacks to insider threats and zero-day exploits. The traditional model of manually reviewing thousands of alerts daily is no longer sustainable.
SOC automation has emerged not as a luxury, but as an operational necessity. By intelligently integrating artificial intelligence (AI), machine learning (ML), orchestration, and automated response capabilities, modern SOCs can dramatically reduce response times, minimize analyst fatigue, and focus human expertise where it matters most – on complex, high-priority threats that require strategic judgment.
At Seceon, we have built our platform philosophy around this reality. This blog explores the defining automation trends reshaping security operations today, and the proven strategies organizations are deploying to build faster, smarter, and more resilient SOCs.
The automation revolution in security operations is not a single shift but a convergence of multiple transformative trends. Understanding these trends equips security leaders with the strategic foresight needed to invest wisely and build resilient operations.
Artificial intelligence is fundamentally redefining how SOCs detect threats. Traditional signature-based detection methods are increasingly ineffective against polymorphic malware, zero-day vulnerabilities, and living-off-the-land (LotL) attacks. AI-driven behavioral analytics offers a paradigm shift: instead of looking for known malicious patterns, it establishes dynamic baselines of normal behavior and flags deviations in real time.
Key capabilities enabled by AI-powered detection include:
● User and Entity Behavior Analytics (UEBA) that identify anomalous activity across users, devices, and network flows
● Unsupervised machine learning models that detect novel attack patterns without relying on pre-defined signatures
● Contextual threat scoring that correlates weak signals across multiple data sources into a unified risk picture
● Adaptive models that continuously learn and evolve with the organization’s environment
Seceon’s aiSIEM™ platform exemplifies this approach, using streaming machine learning to analyze billions of network events, logs, and flows in real time – delivering high-fidelity threat detection that dramatically reduces noise and false positives.
Security Orchestration, Automation, and Response (SOAR) has matured from a complementary technology into a core operational pillar of the modern SOC. SOAR platforms enable teams to codify their institutional knowledge into repeatable, automated playbooks – ensuring that routine and high-volume threats are handled consistently and at machine speed.
SOAR automation delivers value across several critical dimensions:
Alert triage and enrichment – automatically gathering threat intelligence context before analysts even open a ticket
Containment actions – isolating compromised endpoints, blocking malicious IPs, and revoking credentials without manual intervention
Incident workflow management – routing cases, documenting evidence, and maintaining audit trails automatically
Cross-tool orchestration – integrating with firewalls, EDR, IAM, and ITSM platforms for coordinated response
Organizations that have deployed mature SOAR capabilities report Mean Time to Respond (MTTR) reductions of 60-80%, alongside significant analyst productivity gains. The strategic value lies not in replacing analysts but in amplifying their capacity to handle complex, high-severity incidents.
XDR represents the natural evolution of siloed security tools toward a unified, correlated view of threats across the entire attack surface. By integrating telemetry from endpoints, networks, cloud workloads, email, and identity systems, XDR eliminates the blind spots that attackers routinely exploit when moving laterally between environments.
The automation advantages of XDR are particularly compelling:
● Unified telemetry ingestion removes the manual effort of correlating data across disparate tools
● Automated attack chain reconstruction surfaces the full scope of an incident – from initial access to lateral movement and data exfiltration
● Coordinated, cross-layer response actions ensure containment happens simultaneously across all affected vectors
● Reduced tool sprawl lowers operational overhead while improving analyst context and efficiency
As enterprise infrastructure migrates to hybrid and multi-cloud environments, SOC automation platforms must evolve accordingly. Cloud-native security architectures offer elastic scalability, near-zero deployment friction, and the ability to ingest telemetry from geographically dispersed assets without performance degradation.
Cloud-native SOC automation capabilities that are gaining traction include:
● SaaS-delivered SIEM and SOAR platforms that eliminate on-premises infrastructure costs and maintenance burdens
● Automated cloud security posture management (CSPM) that continuously monitors for misconfigurations and policy drift
● Container and Kubernetes security monitoring integrated into unified SOC workflows
● Multi-cloud visibility ensuring consistent detection policies across AWS, Azure, GCP, and hybrid on-premises environments
Technology alone does not transform a SOC. Successful automation requires a deliberate strategy – one that aligns people, processes, and technology around clear operational objectives. Below are the proven strategies that security leaders are adopting to maximize the value of SOC automation investments.
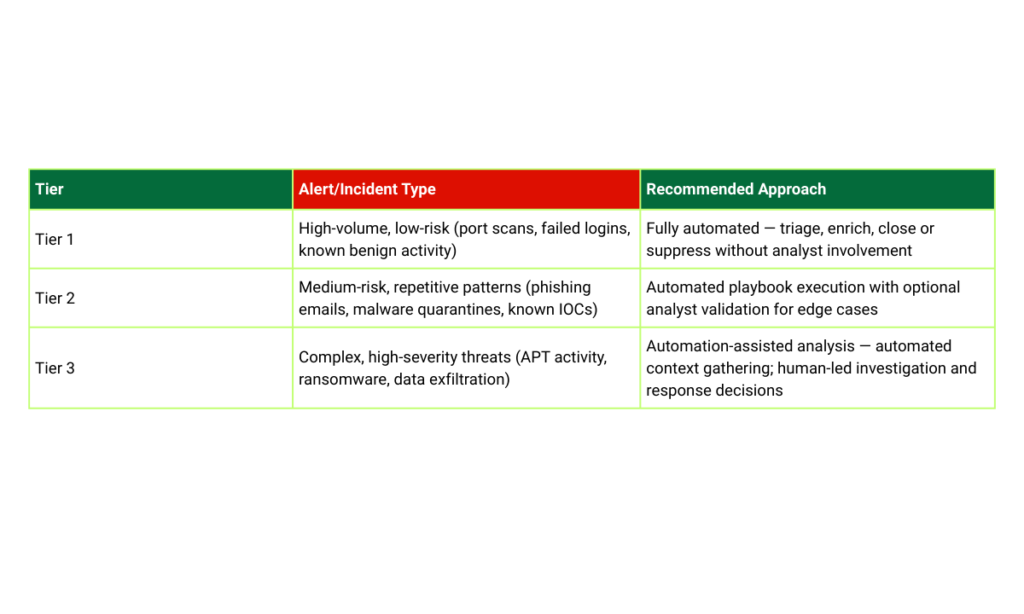
Not all security tasks are equal candidates for automation. Leading SOCs implement a tiered model that categorizes alerts and incidents by complexity, risk, and required expertise – ensuring automation is applied where it delivers the highest value without introducing unacceptable operational risk.
A SOC automation platform is only as powerful as its integrations. Automated response is only meaningful if the platform can actually take action across your security stack – blocking IPs at the firewall, disabling compromised accounts in Active Directory, or quarantining endpoints through your EDR. Comprehensive API integration is not optional; it is the foundation of automated response value.
Integration priorities for modern SOC automation include:
Identity and Access Management (IAM) – automated account lockout and privilege revocation during active threats
Network security controls – bi-directional integration with NGFWs, proxies, and DNS security for automated blocking
ITSM platforms (ServiceNow, Jira) – seamless ticketing and SLA tracking for compliance and governance
Threat intelligence feeds – automated enrichment with context from industry and commercial intelligence sources
Cloud provider APIs – direct integration with AWS Security Hub, Azure Sentinel, and GCP Security Command Center
Organizations should evaluate automation platforms on integration breadth and depth – the number of connectors available as well as the richness of bidirectional actions they support, not just data ingestion.
SOC automation must be measured to be managed. Organizations that treat automation as a measurable capability – tracking, benchmarking, and continuously improving performance – consistently outperform those that deploy automation without governance frameworks.
Core metrics for a mature SOC automation program:
Mean Time to Detect (MTTD) – tracking improvements in detection latency as automation coverage expands
Mean Time to Respond (MTTR) – measuring how quickly automated playbooks resolve or contain incidents
Alert-to-Incident ratio – monitoring false positive rates as AI models mature and are tuned
Automation coverage rate – percentage of alert categories handled without analyst intervention
Analyst productivity ratio – cases handled per analyst per shift, reflecting capacity liberation from automation
Playbook execution success rate – ensuring automated actions are executing reliably and producing intended outcomes
The most effective SOC automation strategies do not pursue automation for its own sake – they pursue the amplification of human expertise. Automation should handle the repetitive, high-volume, and time-sensitive work while human analysts focus on what they do best: contextual judgment, threat hunting, adversary emulation, and strategic decision-making.
Principles of effective human-machine collaboration in the SOC:
● Design automated workflows with clear escalation paths – analysts must be able to intervene, override, or audit any automated action
● Provide analysts with rich automated context so they spend time on decisions, not data gathering
● Invest in continuous playbook refinement – treat automation as a living capability that evolves with the threat landscape
● Build analyst feedback loops into AI models – human validation of automated decisions improves model accuracy over time
● Foster a culture of automation ownership – empower analysts to propose, design, and iterate on playbooks
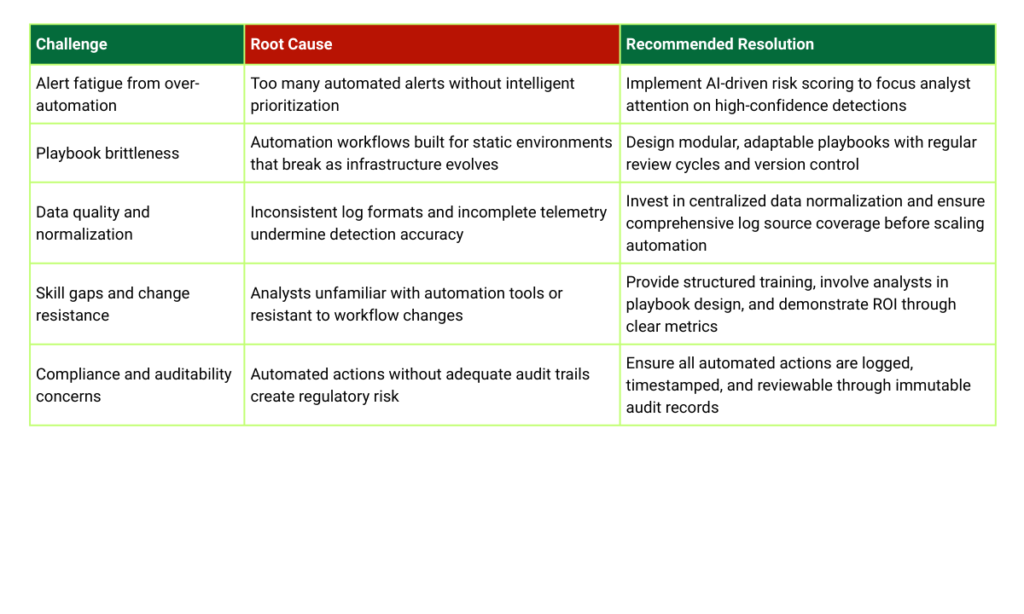
Despite its compelling benefits, SOC automation is not without challenges. Organizations that rush into automation without addressing foundational issues often find themselves with complex, brittle workflows that create new problems rather than solving existing ones. Anticipating and proactively managing these challenges is essential for sustainable success.
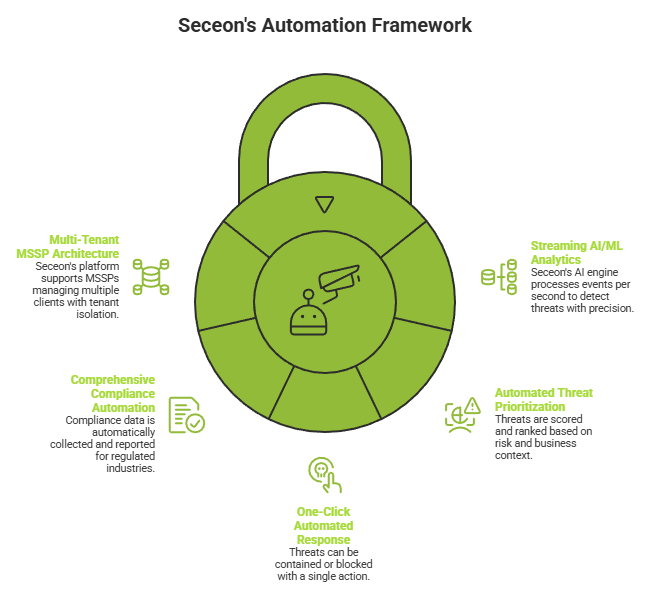
At Seceon, we designed the Open Threat Management (OTM) platform from the ground up around the principles of intelligent automation, real-time detection, and actionable response. Our platform is purpose-built to help MSSPs, enterprises, and mid-market organizations operationalize SOC automation without requiring large specialist teams or complex deployment projects.
Seceon’s patented AI engine processes millions of events per second using a combination of supervised and unsupervised machine learning models. By continuously profiling behavior across users, devices, applications, and network flows, the platform detects threats that evade signature-based tools – with precision that minimizes alert noise.
Every detected threat is automatically scored and prioritized based on risk, confidence, and business context. Analysts are presented with a curated, ranked threat queue – not a raw flood of alerts – enabling them to immediately focus on the highest-risk incidents.
Seceon’s platform supports automated and semi-automated response actions across integrated security controls. Threats can be contained, blocked, or quarantined directly from the analyst console with a single action, dramatically compressing time-to-contain for critical incidents.
For regulated industries, Seceon automates the collection, correlation, and reporting of compliance-relevant data across HIPAA, PCI DSS, SOC 2, NIST, and other frameworks – reducing the manual burden of audit preparation while maintaining continuous compliance posture.
Seceon’s platform is architected for MSSPs managing security for multiple clients, with full tenant isolation, centralized playbook management, and the ability to scale automation capacity across a broad client portfolio without proportional headcount growth.
The pace of innovation in SOC automation shows no signs of slowing. Several emerging developments will define the next generation of security operations capabilities, and forward-looking organizations are already positioning themselves to capitalize on them.
Generative AI for Security Operations
Large language models (LLMs) are beginning to find meaningful application in security operations – from natural language querying of SIEM data and automated incident report generation to AI-assisted playbook authoring and analyst coaching. While still maturing, generative AI will substantially lower the barrier to automation for organizations that lack deep engineering resources.
Autonomous Threat Response
As AI confidence levels improve and automation governance frameworks mature, more organizations will implement fully autonomous response for defined threat categories. This is particularly relevant for MSSPs operating at scale, where the economics of manual response are unsustainable across large client portfolios.
Identity-Centric Automation
As identity increasingly becomes the primary attack vector, SOC automation is evolving to place identity at its center – automatically detecting abnormal authentication patterns, privilege escalations, and lateral movement, and taking instant action to protect identity infrastructure as the first line of cyber defense.
SOC automation is no longer a competitive advantage – it is a competitive necessity. Organizations that fail to automate will find themselves outpaced by adversaries who have already automated their attack infrastructure and increasingly leverage AI to accelerate and scale their campaigns.
But the greatest benefit of SOC automation is not merely operational efficiency. It is the elevation of your security team – freeing analysts from the grinding monotony of alert triage to focus on the strategic, creative, and adversarial-thinking work that machines cannot replicate. Automation multiplies human capability and builds the kind of resilient, adaptive security posture that organizations need to thrive in an increasingly hostile digital environment.
At Seceon, we are committed to making intelligent SOC automation accessible, measurable, and continuously improving – for enterprises, MSSPs, and the communities they protect. Whether you are just beginning your automation journey or scaling toward fully autonomous operations, we are here to accelerate your path to security excellence.
