
India’s Defence Industrial Base is entering a defining phase. The shift toward “Indigenization 2.0” is accelerating the development of sovereign platforms, indigenous operating systems, and AI-enabled warfighting capabilities. At the same time, cyber hostilities have intensified dramatically. In 2025 alone, India recorded hundreds of millions of cyber detections, and hybrid conflicts demonstrated that digital sabotage is now inseparable from modern warfare.
Cybersecurity in the defence sector is no longer a supporting function. It is a strategic pillar of national security.
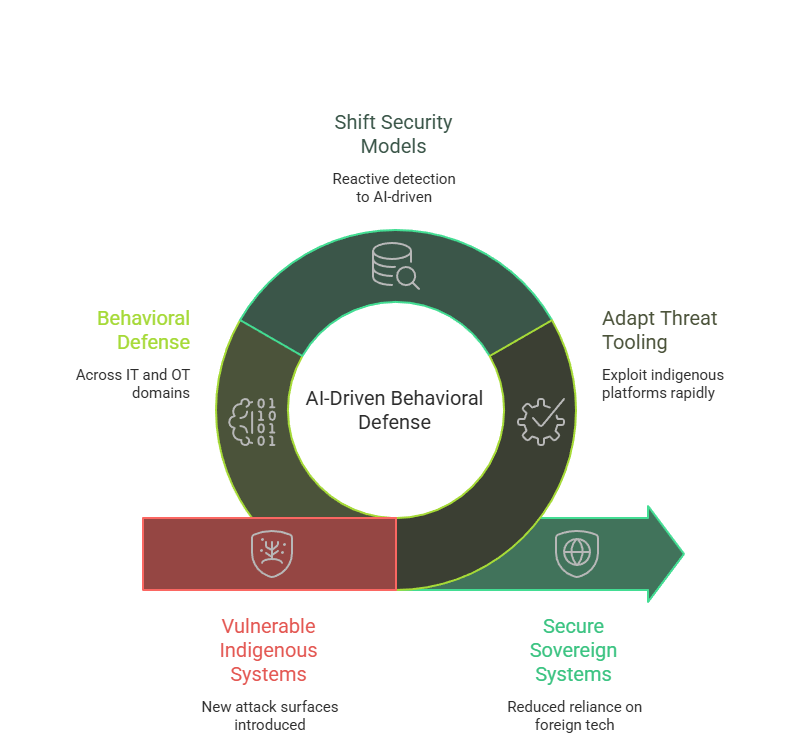
India’s defence modernization strategy emphasizes self-reliant digital ecosystems. Initiatives such as indigenous operating systems, secure MPLS-based communication networks, and AI-integrated battlefield systems reduce reliance on foreign technology. However, these sovereign systems also introduce new attack surfaces.
Threat actors are rapidly adapting their tooling to exploit indigenous platforms. Signature-based security models designed for commercial IT environments struggle to detect adversaries targeting customized defence infrastructure. This requires a shift from reactive detection to AI-driven behavioral defense across IT and OT domains.
The events of 2025 marked a turning point. Following geopolitical tensions, India experienced coordinated cyber campaigns that included Distributed Denial-of-Service attacks, GPS spoofing, and misinformation operations. Millions of targeted attacks were launched within a compressed timeframe, affecting military institutions, municipal services, and energy infrastructure.
Even when the majority of attacks were thwarted, the scale revealed a hard truth. Defence cybersecurity must operate at machine speed, because adversaries already do.
State-sponsored actors continue to focus on intellectual property theft, espionage, and supply chain compromise within the defence sector.
Recent campaigns demonstrate evolving tactics:
These campaigns are not opportunistic. They are strategic and long-term, designed to erode operational integrity and national advantage.
One of the most instructive incidents in recent years involved a misconfigured cloud storage bucket within a government pension administration system. The breach was not caused by sophisticated exploitation, but by a basic configuration oversight. Sensitive data was exposed, and credentials surfaced on underground marketplaces.
The broader lesson is clear. In critical sectors, small configuration errors can create national-level exposure. Cloud, IT, and OT environments require continuous validation, not periodic review.
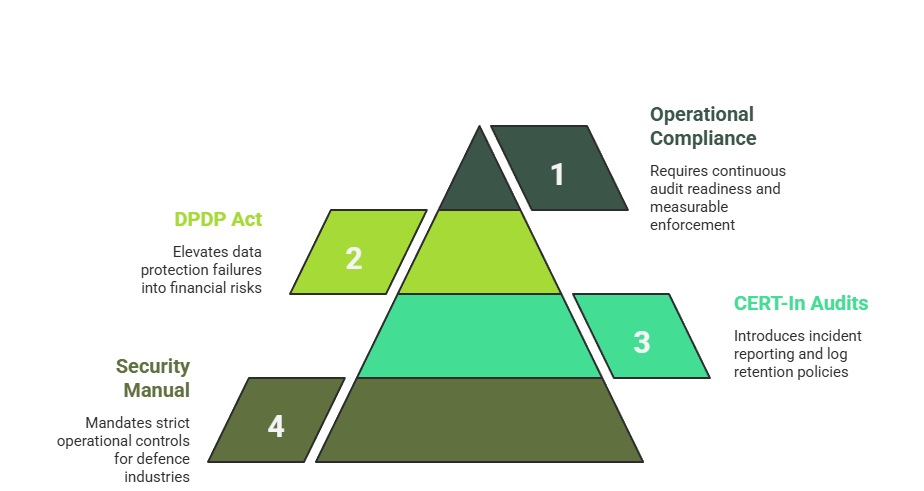
India’s regulatory framework has matured rapidly. The Security Manual for Licensed Defence Industries mandates strict operational controls, including biometric access baselines and air-gapped networks for classified projects. CERT-In’s comprehensive audit policy introduces six-hour incident reporting windows and extended log retention requirements. The DPDP Act elevates data protection failures into significant financial and legal risk.
Compliance is no longer theoretical. It is operational, measurable, and enforceable.
Organizations must demonstrate continuous audit readiness, not static compliance snapshots.
Legacy security architectures face structural limitations in defence environments:
In environments where residual breaches still occur despite high prevention rates, the cost of slow detection is strategic risk.
To meet the scale and speed of modern hybrid threats, defence organizations require integrated, AI-driven cybersecurity platforms.
An effective modern architecture must:
When detection times shrink from months to minutes and automated response executes in seconds, dwell time collapses. False positives drop dramatically, enabling even junior analysts to operate with expert-level efficiency.
This is not incremental improvement. It is architectural transformation.
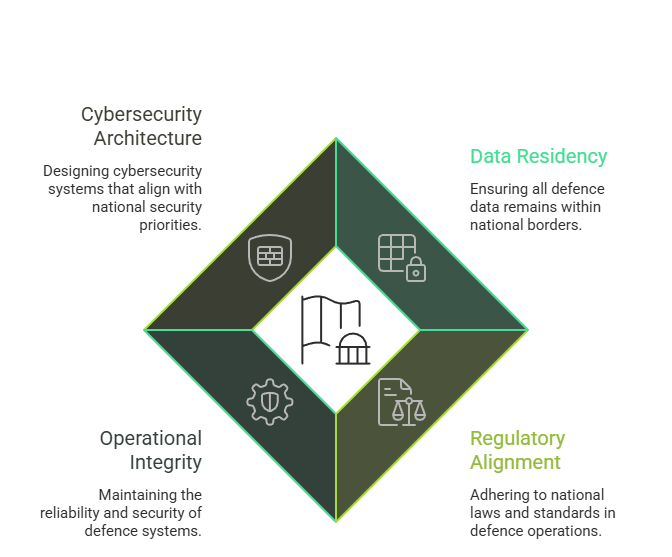
For the defence sector, sovereignty is non-negotiable. Security platforms must operate entirely within national borders, ensuring that telemetry, logs, and threat intelligence remain under domestic jurisdiction. Data residency, regulatory alignment, and operational integrity are foundational requirements.
Cybersecurity architecture must reflect national security priorities.
Organizations adopting unified, AI-driven security models report measurable impact:
More importantly, they gain operational resilience against state-backed adversaries.
India’s Defence Industrial Base operates at the intersection of rapid modernization and persistent cyber hostility. Fragmented, compliance-driven security models are no longer sufficient to protect mission-critical infrastructure in an era of AI-powered hybrid warfare.
A unified, AI-driven, autonomous cybersecurity architecture is now essential. It enables continuous visibility, rapid response, regulatory alignment, and sovereign control. In modern defence environments, cybersecurity is not just protection. It is strategic capability.
