The global telecommunications ecosystem has entered its most dangerous cyber era .5G, O RAN, cloud workloads, and massive IoT ecosystems expand, telecom networks have become the number one target for nation-state APTs .
Attacks like Salt Typhoon , labeled the worst telecom breach in U.S. history , prove one reality:
Traditional enterprise security tools cannot defend networks operating at telecom scale .
Nation-state actors have infiltrated wiretap systems , maintained multi year persistence , and exfiltrated sensitive subscriber and network data . Telecom operators now face a crisis that threatens national security, economic stability, and global communication infrastructure .
📌 Full whitepaper here: https://info.seceon.com/telecommunications-network-security
The Reality: Telecom’s Scale Is Now Its Greatest Vulnerability Telecommunications networks operate on unmatched scale and complexity , including:
SS7, Diameter, GTP, SIP, and 5G protocols120 plus petabytes of data processed dailyBillions of signaling messages every dayUltra distributed multi vendor infrastructure Millions of IoT and MEC edge devices
Yet most operators still rely on fragmented, legacy tools never designed for this scale.
This results in:
Protocol blind spots High false positives Delayed detection Lateral movement across generations of technology Persistent APT access
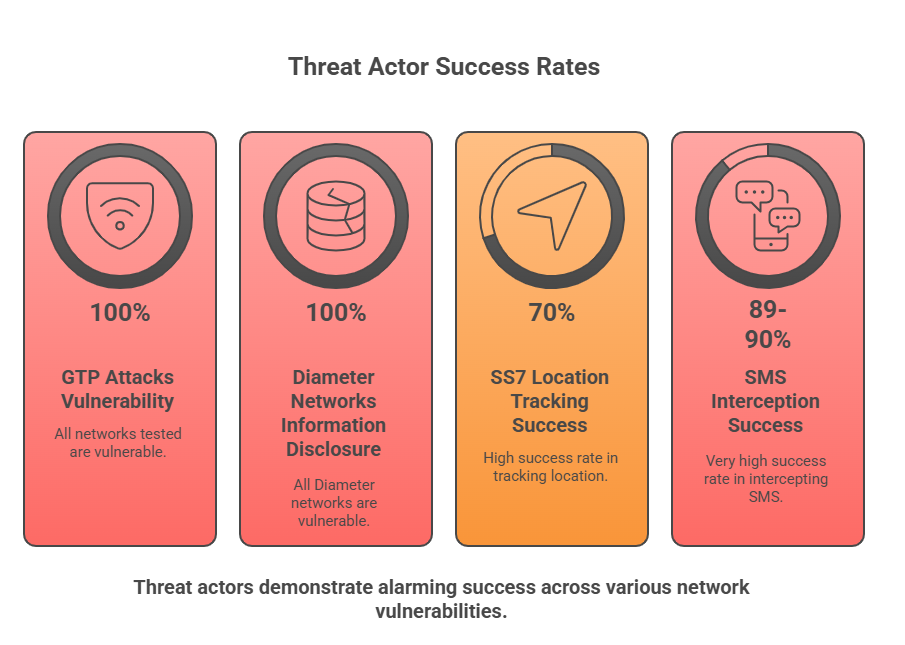
Threat actors consistently succeed:
100 percent of networks tested are vulnerable to GTP attacks 100 percent of Diameter networks are vulnerable to information disclosure 70 percent success rate in SS7 location tracking 89 to 90 percent success rate in SMS interception
The Threat: Nation State APT Campaigns Targeting Global Telecom Providers Telecommunications networks are now the primary battlefield for geopolitical cyber operations .
Salt Typhoon (China) The most severe telecom breach in U.S. history.
Persistent access since 2022
Infiltrated AT&T, Verizon, T Mobile, Lumen
Compromised wiretap systems
Exfiltrated call metadata and intercept capabilities
Volt Typhoon (China)
Compromised 30 percent of exposed Cisco routers
Pre-positioned within telecom edge infrastructure
Flax Typhoon (China)
Built botnet operations targeting telecom backbone environments
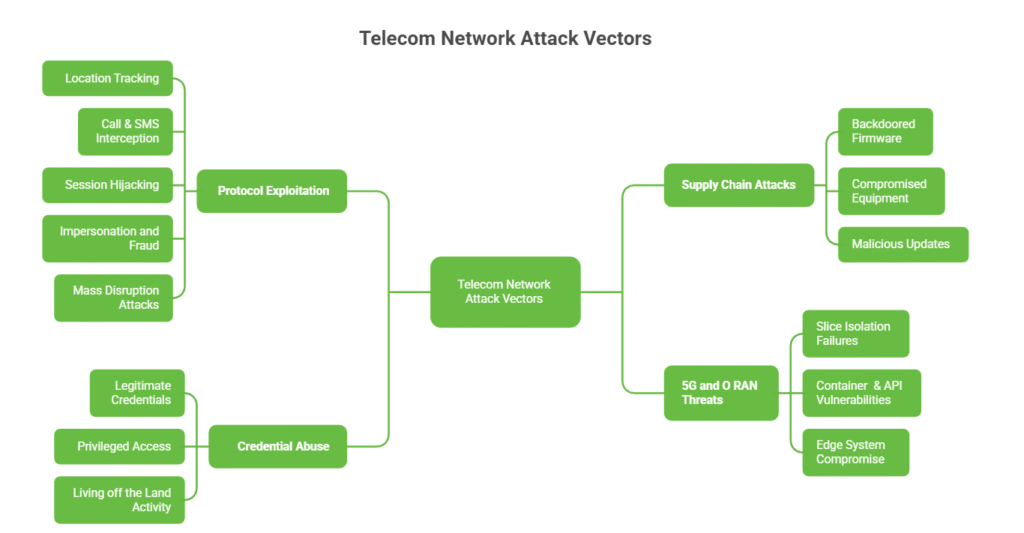
Attack Vectors Exposed Protocol Exploitation Telecom signaling protocols enable:
Location tracking Call and SMS interception Session hijacking Impersonation and fraud Mass disruption attacks
Supply Chain Attacks Including:
Backdoored firmware Compromised vendor equipment Malicious updates
Credential Abuse APTs maintain multi-year persistence via:
Legitimate credentials
Privileged access
Living off the land activity
5G and O RAN Threats
Slice isolation failures Container and API vulnerabilities Edge system compromise
Why Traditional Security Tools Fail Telecom Operators Legacy tools cannot handle:
Petabyte scale data volume Billions of daily protocol messages Telecom specific telemetry IPv6 massive addressing 5G service based architectures
They lack:
Protocol awareness Real time correlation Behavioral analytics Telecom specific AI models
This results in SOC overload , alert fatigue , and multi year APT persistence .
The Solution: A Unified AI Platform Purpose Built for Telecom Seceon’s Open Threat Management (OTM) platform is the first AI driven, telecom native security architecture designed for true telecom scale.
Core Capabilities
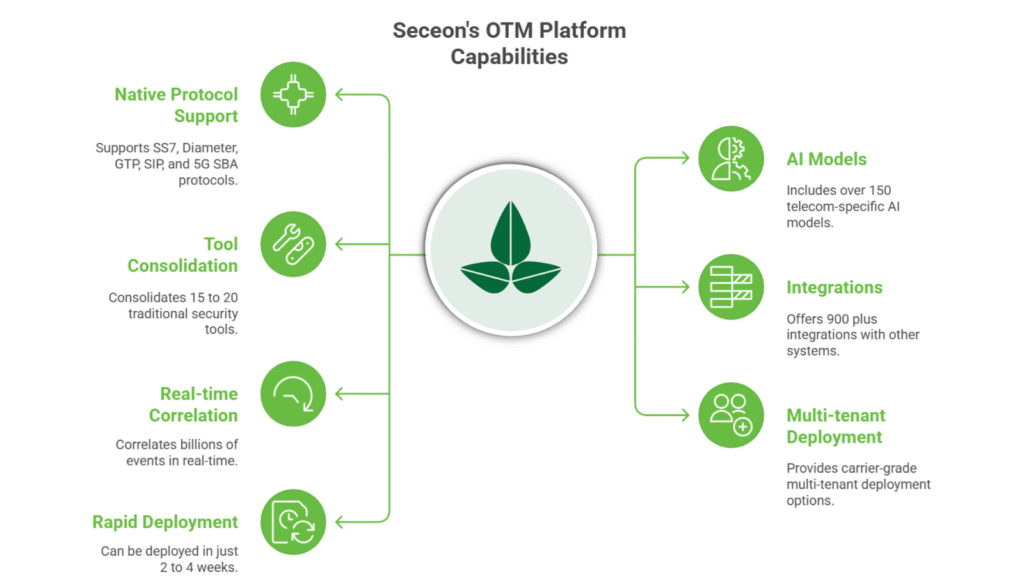
Native support for SS7, Diameter, GTP, SIP, 5G SBA
150 plus telecom specific AI models Consolidates 15 to 20 traditional tools
900 plus integrations Real time correlation across billions of events
Carrier grade multi tenant deployment Deployment in 2 to 4 weeks
Operators gain:
95 percent protocol attack detection accuracy70 percent faster detectionSub 5-second alertingOver 50 million dollars are prevented from fraud annually
AI at the Core of Telecom Defense Seceon’s AI engine enables:
Dynamic behavioral baselining Graph neural network correlation Cross protocol lateral movement detection Covert channel discovery Real time anomaly detection Subscriber analytics for 480 plus million users
This shifts operators from reactive to predictive and autonomous defense .
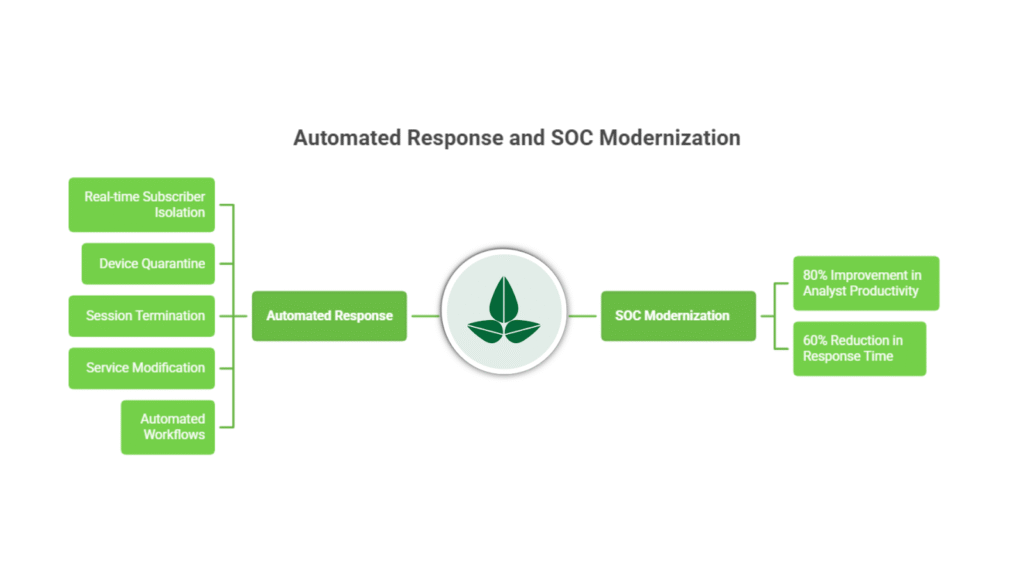
Automated Response and SOC Modernization OTM orchestrates:
Real-time subscriber isolation Device quarantine Session termination Service modification Automated workflow
SOC teams report:
80 percent improvement in analyst productivity60 percent reduction in response time
Real World Impact and Case Studies Bharti Airtel: 480 Million Subscribers Protected
120 PB processed daily50 billion SS7 messages analyzed per day500 million LTE authentications monitoredSub 5 second detection 95 percent accuracy
Case Study 1: Global Carrier SOC Transformation
Consolidated 18 tools
Increased detection accuracy to 95 percent
68 percent operational cost reduction
Case Study 2: Preventing 2.3 Billion Dollars in Losses
Detected signaling fraud
72 percent faster response
Case Study 3: Tier 1 Operator Securing 5G and Cloud
70 percent faster detection80 percent SOC efficiency gain50 million plus fraudulent sessions blocked annually
From Fragmented Defense to Telecom Cyber Resilience Telecom operators are now standardizing on:
Unified security platforms Predictive AI analytics Automated compliance End to end 5G and O RAN visibility Scalable multi tenant SOC operations
This delivers:
Stronger national infrastructure protection Reduced breach risk Lower fraud losses Higher operational efficiency Faster containment
This shift is no longer optional .strategic necessity for global telecom resilience.
Conclusion: Telecom Cybersecurity Has Entered a Critical New Phase Telecom networks form the digital nervous system of modern civilization .
Nation state APTs, protocol level attacks, and multi vector intrusions demand a telecom native, AI powered security model .
Unified platforms like Seceon OTM enable operators to:
Detect advanced attacks in real time Protect billions of signaling events Automate response at carrier scale Prevent multi billion dollar fraud losses Ensure secure 5G, O RAN, and cloud transformation
Telecom operators now stand at a defining crossroads .unified AI driven cybersecurity .