
In today’s cybersecurity market, nearly every vendor claims to offer an integrated or unified platform. For buyers under pressure to reduce complexity, these promises are appealing. But beneath the marketing language lies a reality that many organizations only discover after a breach: integration does not equal unification.
Many so-called platforms are not designed as platforms at all. They are collections of tools acquired, bundled, or loosely connected, which attempt to behave like a single system. This architectural shortcut introduces systemic cybersecurity risk that buyers rarely evaluate during procurement.
An integrated platform connects tools. A unified platform is designed as one system from the ground up. In stitched together environments, each tool maintains its own data model, and events are normalized late, if at all. Correlation occurs after ingestion rather than at the source, which ensures response actions remain siloed.
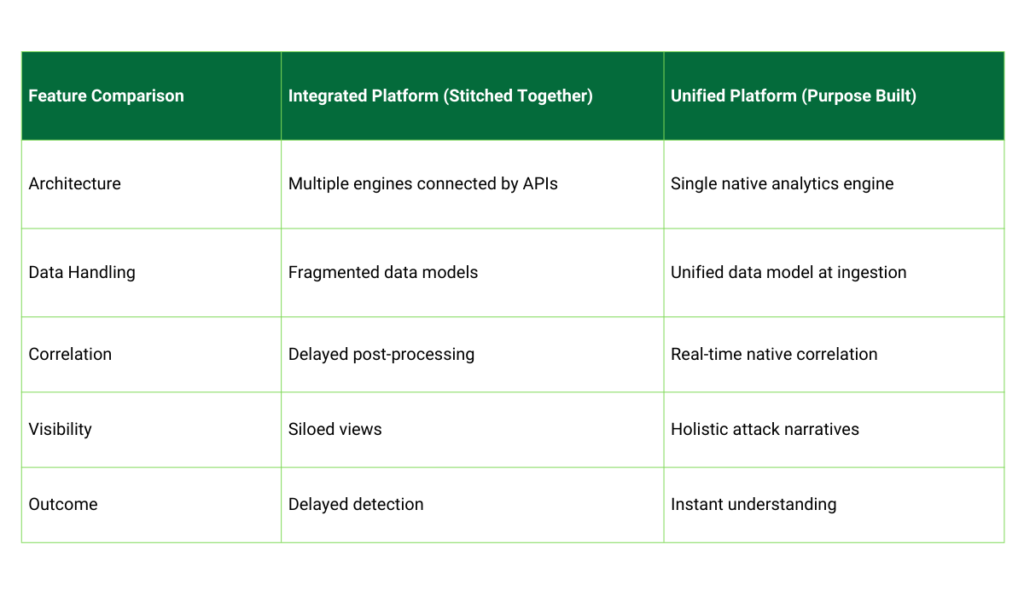
This architectural gap creates delays in detection and deep gaps in understanding attacker behavior.
Modern attackers no longer rely on loud exploits. They operate across time, domains, and trust boundaries. They utilize strategies that exploit the lack of communication between tools:
When security tools analyze these events independently, attacks appear as unrelated noise. Context is lost, and without context, detection fails.
Most buyers assume that more tools mean better protection. Dashboards reinforce this belief with charts, counts, and compliance metrics. But activity does not equal efficacy. An organization may be collecting endpoint telemetry, network flows, cloud audit logs, and identity events yet still fail to see a complete attack narrative because those data streams never converge into a single behavioral model.
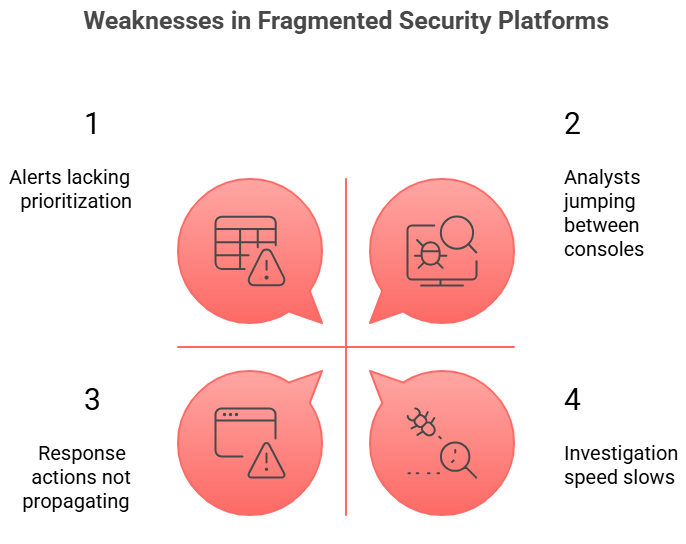
During an actual breach, fragmented platforms reveal their weaknesses:
Attack dwell time increases not because tools failed but because the architecture did.
Procurement processes often focus on feature checklists, integration claims, analyst rankings, and vendor reputation. They rarely assess whether analytics operate on a shared data plane, whether correlation is native or post-processing, or whether response is centralized or tool-specific.
Before accepting any platform claim, buyers should demand to know:
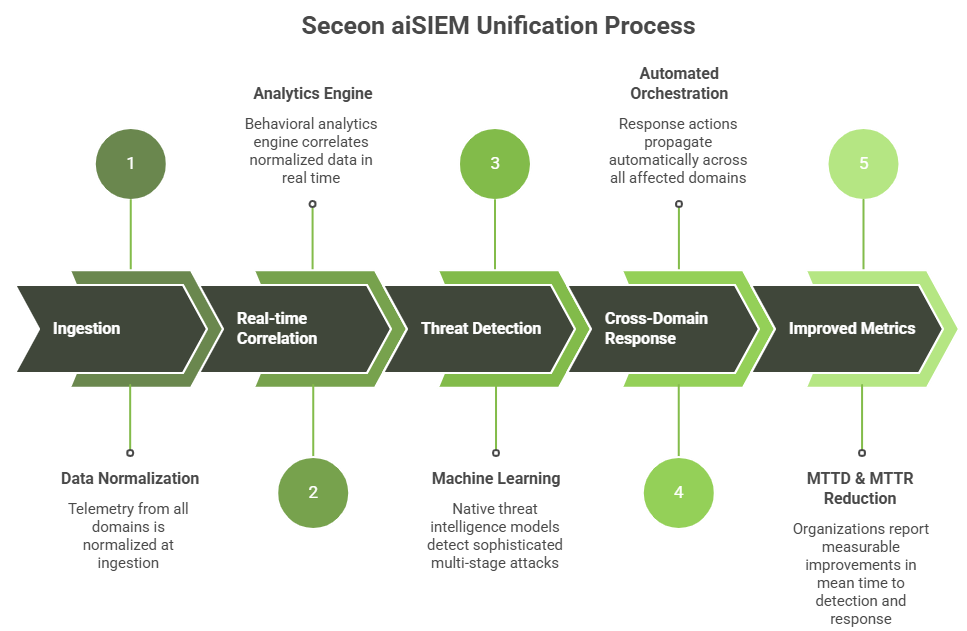
Unlike stitched-together platforms, Seceon aiSIEM was architected as a unified system from inception. This fundamental design choice eliminates the structural weaknesses that plague integrated platforms.
Single Analytics Engine
All telemetry, including endpoint, network, cloud, and identity, flows into one behavioral analytics engine that correlates in real time, not post-processing.
Unified Data Model
Events are normalized at ingestion, preserving context and relationships that fragmented systems lose.
Cross Domain Response
When Seceon detects a threat spanning cloud to endpoint, response actions propagate automatically across all affected domains without manual orchestration.
Native Threat Intelligence
Machine learning models operate on complete attack narratives, not isolated signals, enabling detection of sophisticated multi-stage attacks that evade tool-specific defenses.
Organizations deploying Seceon report measurable improvements in mean time to detection (MTTD) and mean time to response (MTTR) because the platform eliminates the architectural delays inherent in stitched solutions.
Security failures today are rarely due to missing tools. They happen because organizations deploy systems that cannot see attacks as attackers execute them. True platforms reduce risk by design. Kludged platforms hide it until it is too late.
