
Security Operations Centers are under unprecedented strain. Alert volumes continue to rise, attack paths are becoming more complex, and experienced analysts remain difficult to hire and retain. In response, many organizations add more tools or increase headcount to compensate for platforms that do not work as expected.
This creates a hidden operational cost. When security relies on human effort to connect fragmented tools, it does not scale. It slowly breaks down.
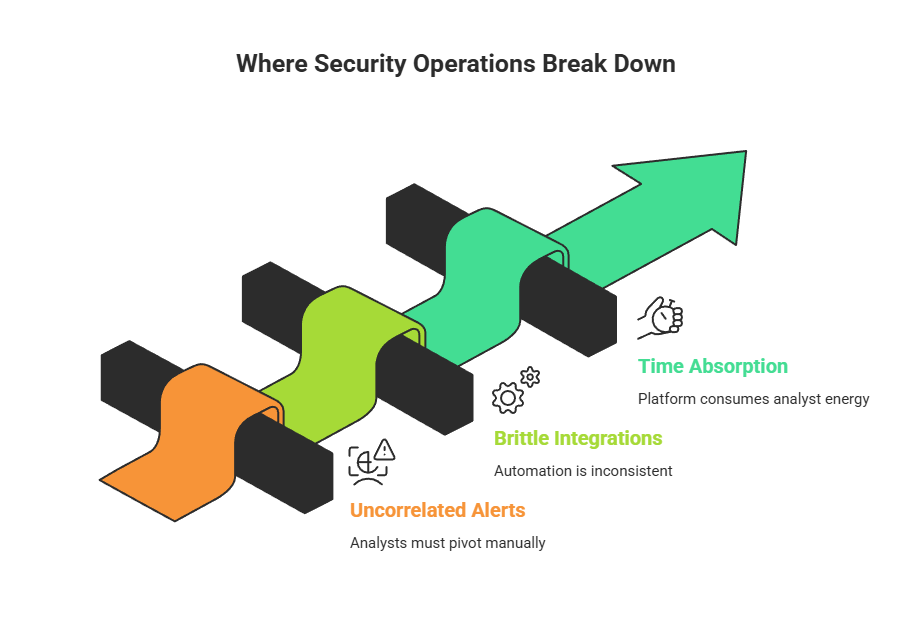
In fragmented security environments, failure rarely appears as a single event. It shows up in daily operations. Alerts arrive without correlation. Analysts are forced to pivot manually across multiple tools. Playbooks depend on brittle integrations, and automation is inconsistent or incomplete.
Instead of enabling analysts to focus on investigation and decision-making, the platform absorbs their time and energy.
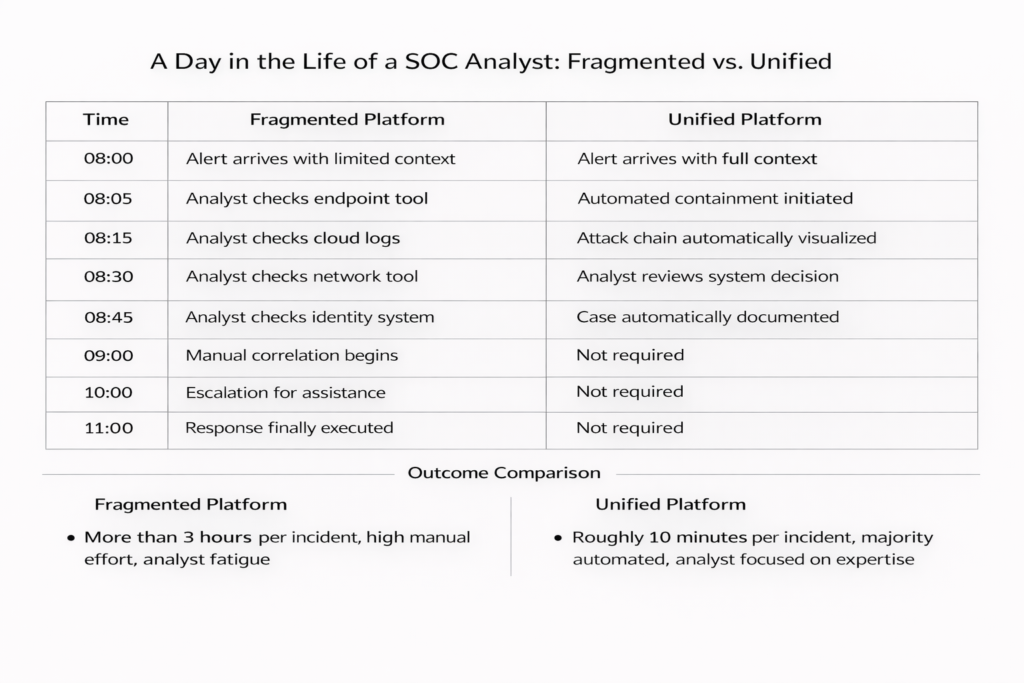
In a fragmented platform, incidents often take more than three hours to resolve. A significant portion of analyst time is spent on mechanics rather than investigation, leading to fatigue and slow response.
In a unified platform, the same incident can be resolved in roughly ten minutes. Most actions are automated, and analysts focus on applying judgment and expertise instead of stitching data together.
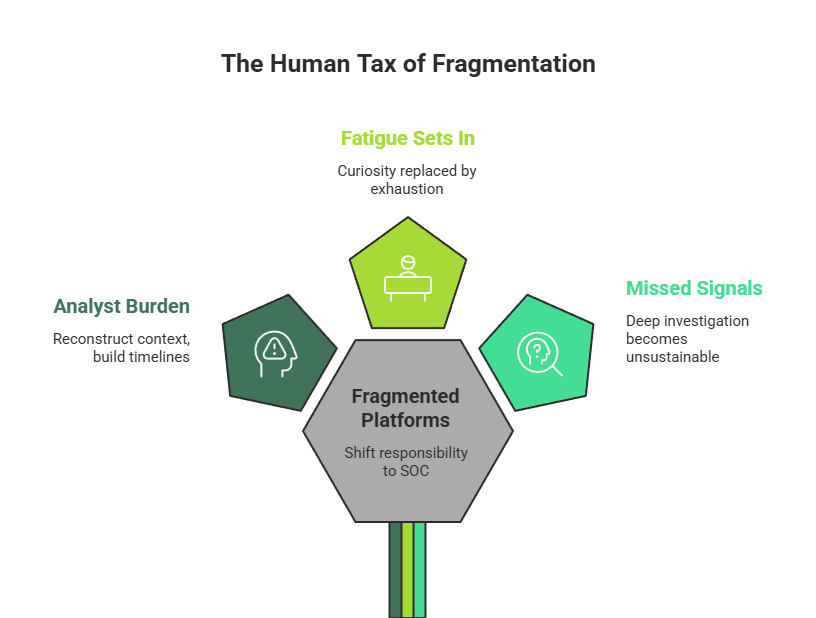
Fragmented platforms shift responsibility onto SOC teams. Analysts become responsible for reconstructing context, building timelines, eliminating false positives, and coordinating actions across tools. This work is repetitive, mentally draining, and highly error-prone.
Over time, fatigue replaces curiosity. Missed signals become normalized, not because analysts are careless, but because the platform makes deep investigation unsustainable at scale.
Fragmented security platforms often appear affordable on paper, but operational reality tells a different story. Managed services gradually expand to compensate for tooling gaps. Professional services engagements rarely disengage fully. Headcount grows, yet security outcomes do not improve. Mean time to respond stagnates despite rising investment.
Organizations are not paying for better security. They are paying to keep security operations functioning.
When analysts spend their days clicking between consoles, chasing low-value alerts, manually validating signals, and fighting tooling friction, burnout becomes unavoidable. As experienced analysts leave, organizations lose institutional knowledge that no platform can replace. The cycle then repeats with new hires facing the same operational constraints.
Many platforms claim automation capabilities, but in practice automation frequently stops at tool boundaries. Response actions require manual approval, integrations break when APIs change, and playbooks evolve into ongoing maintenance projects.
This creates the appearance of automation without delivering operational relief. True automation requires architectural cohesion, not a collection of loosely connected tools.
Rather than counting alerts, tools, or integrations, organizations should measure outcomes that reflect real operational scalability. These include analyst time per incident, automated response coverage, mean time to understanding rather than just response, and reduction in human touchpoints.
These metrics reveal whether a security platform truly scales or merely survives under pressure.
Seceon was designed around a simple principle. Security platforms should amplify analyst expertise, not replace it with manual labor.
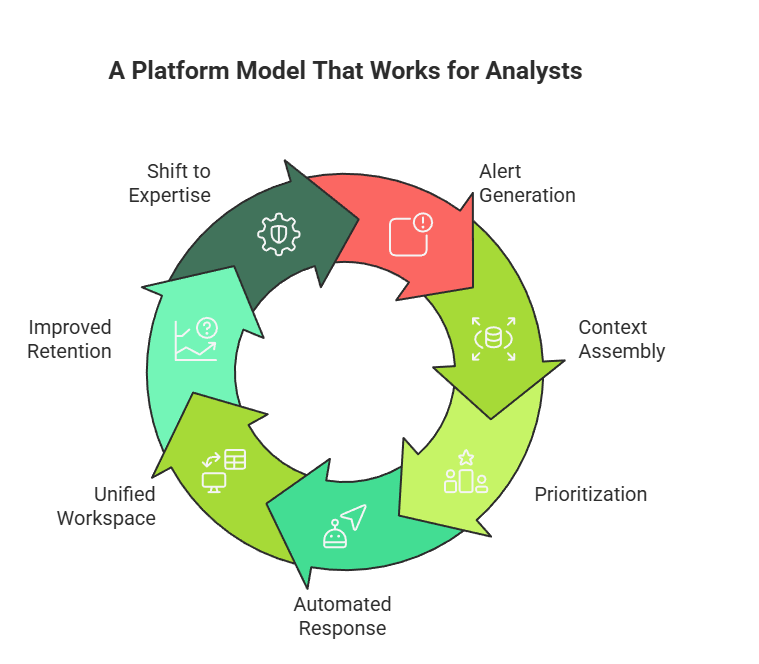
When an alert fires, Seceon automatically assembles full context across endpoint, network, cloud, and identity data. Alerts are prioritized based on real attack progression and business impact rather than static severity scores. Response actions execute across domains automatically, and all investigation context persists in a unified workspace so analysts do not need to reconstruct decisions across shifts.
Organizations adopting this model report significant reductions in manual investigation time, lower analyst workload per incident, improved retention, and a shift from reactive labor to meaningful security expertise.
And no SOC can scale on burnout.
If a security platform requires constant human compensation, it is not reducing risk.
It is converting technical debt into human exhaustion.
