
Traditional security measures like firewalls and antivirus software are no longer sufficient to protect organizations from sophisticated cyber threats. As attackers leverage advanced techniques that bypass conventional controls, User and Entity Behavior Analytics (UEBA) has emerged as a transformative technology that fundamentally changes how organizations detect, investigate, and respond to security threats.
User and Entity Behavior Analytics is an advanced cybersecurity technology that uses machine learning, artificial intelligence, and statistical analysis to establish baseline behaviors for users and entities within an organization’s IT environment. Unlike traditional rule-based systems that search for known attack signatures, UEBA learns what normal behavior looks like for each user and entity, then identifies deviations that may indicate security threats, insider attacks, compromised accounts, or policy violations.
The term “entities” encompasses human users, applications, servers, routers, IoT devices, endpoints, and any component that interacts within your network. This comprehensive approach monitors everything with an identity that performs actions within your digital infrastructure, making UEBA particularly effective at detecting previously unknown threats, zero-day attacks, and sophisticated insider threats that traditional tools typically miss.
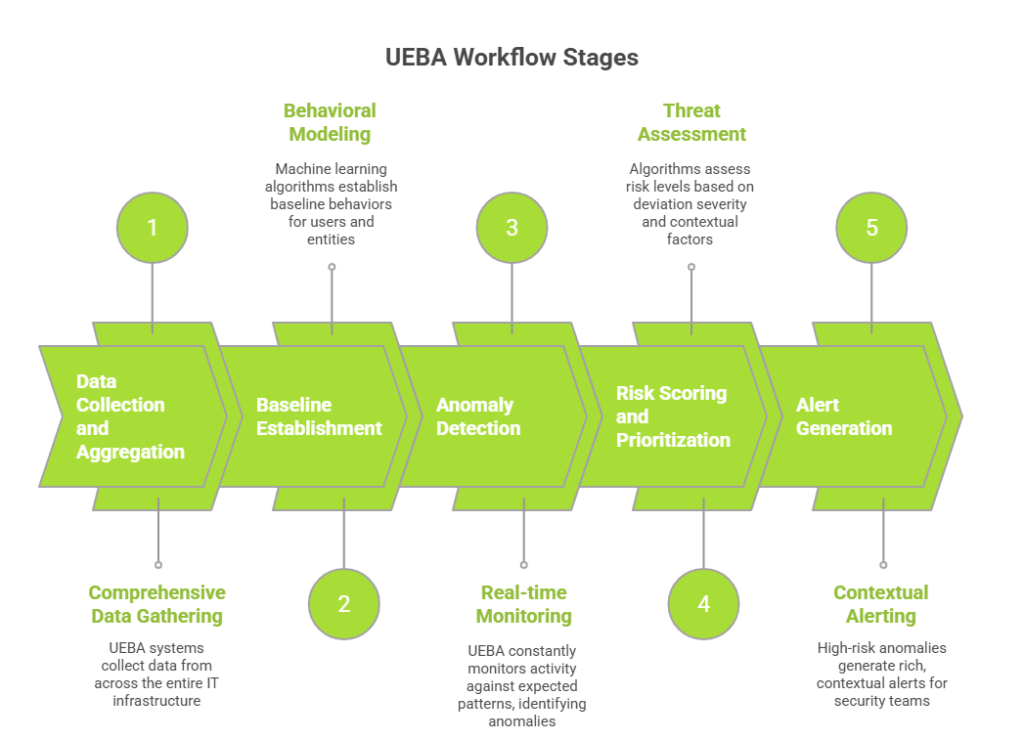
UEBA operates through a sophisticated multi-stage process combining data collection, behavioral modeling, anomaly detection, and risk scoring.
Data Collection and Aggregation: UEBA systems collect data from across your entire IT infrastructure, including authentication logs, network traffic data, file access logs, application usage patterns, email metadata, cloud service activity, endpoint actions, and database queries. This comprehensive data collection creates a holistic view of all organizational activities.
Baseline Establishment: Machine learning algorithms establish baseline behaviors for every user and entity, including working hours and login times, typical access locations, standard file access patterns, normal network communications, data transfer volumes, application usage, and collaboration patterns. These baselines continuously refine as legitimate behaviors evolve, ensuring normal business changes don’t trigger false alarms.
Anomaly Detection: UEBA constantly monitors ongoing activity against expected patterns, identifying anomalies such as login attempts from unusual locations or odd hours, access to atypical files or systems, unusually large data transfers, communications with suspicious external addresses, privilege escalations, changes in work patterns, and use of systems outside normal scope.
Risk Scoring and Prioritization: UEBA uses sophisticated algorithms to assess risk levels based on deviation severity, data sensitivity, user roles and privileges, contextual information, correlation with other activities, and historical patterns. Each anomaly receives a risk score, with the system aggregating multiple lower-risk anomalies into higher-risk threat scenarios, ensuring security teams focus on critical threats.
Alert Generation: High-risk anomalies generate rich, contextual alerts including detailed behavioral information, baseline comparisons, risk scores with contributing factors, correlated activities, investigation recommendations, and automated response options. This comprehensive context dramatically reduces investigation time and enables informed decisions.
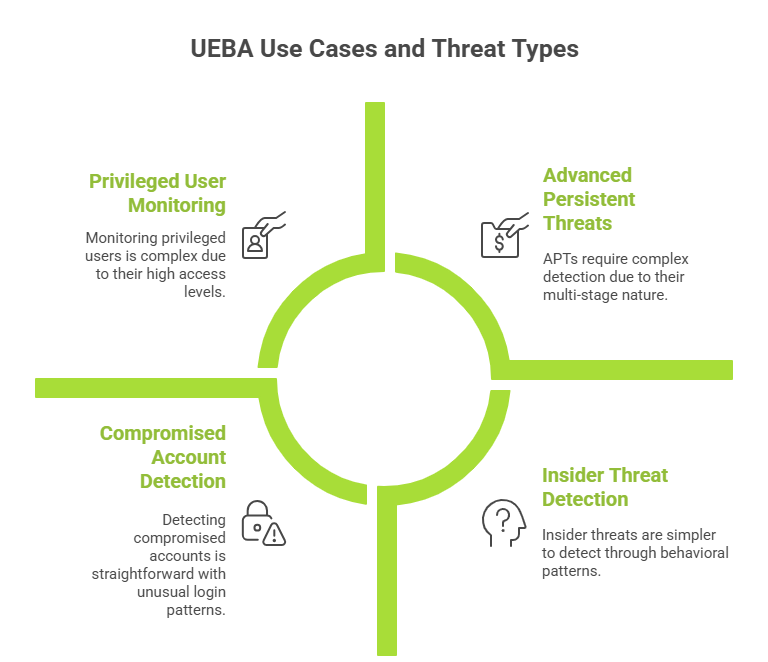
Insider Threat Detection: UEBA excels at identifying behavioral patterns suggesting malicious intent, including employees accessing unusual volumes of sensitive data before departure, accessing files unrelated to job responsibilities, attempting data exfiltration, seeking unauthorized privilege escalation, and accessing competitor-related information. UEBA detects these patterns even when insiders use legitimate credentials.
Compromised Account Detection: When attackers gain legitimate access through stolen credentials, UEBA identifies subtle behavioral differences, including logins from unusual geographic locations, impossible travel scenarios, access patterns differing from typical behavior, lateral network movement, privilege escalation attempts, and activities outside normal working hours.
Advanced Persistent Threats: UEBA detects APTs by identifying subtle anomalies across multiple attack stage,s including reconnaissance activity, command and control communications, lateral movement, privilege escalation, and staged data exfiltration. The ability to correlate multiple small anomalies provides comprehensive views of attacker activity.
Cloud Security and Shadow IT: UEBA provides critical visibility into cloud activity, detecting unusual usage patterns, identifying unauthorized cloud applications, monitoring data movement to and from cloud services, detecting compromised cloud accounts, and identifying risky configurations or excessive permissions across hybrid IT landscapes.
Privileged User Monitoring: UEBA provides enhanced monitoring of high-privilege users, including administrators, executives, developers with production access, and third-party contractors, detecting unauthorized system changes, excessive data access, privilege abuse, and policy violations.
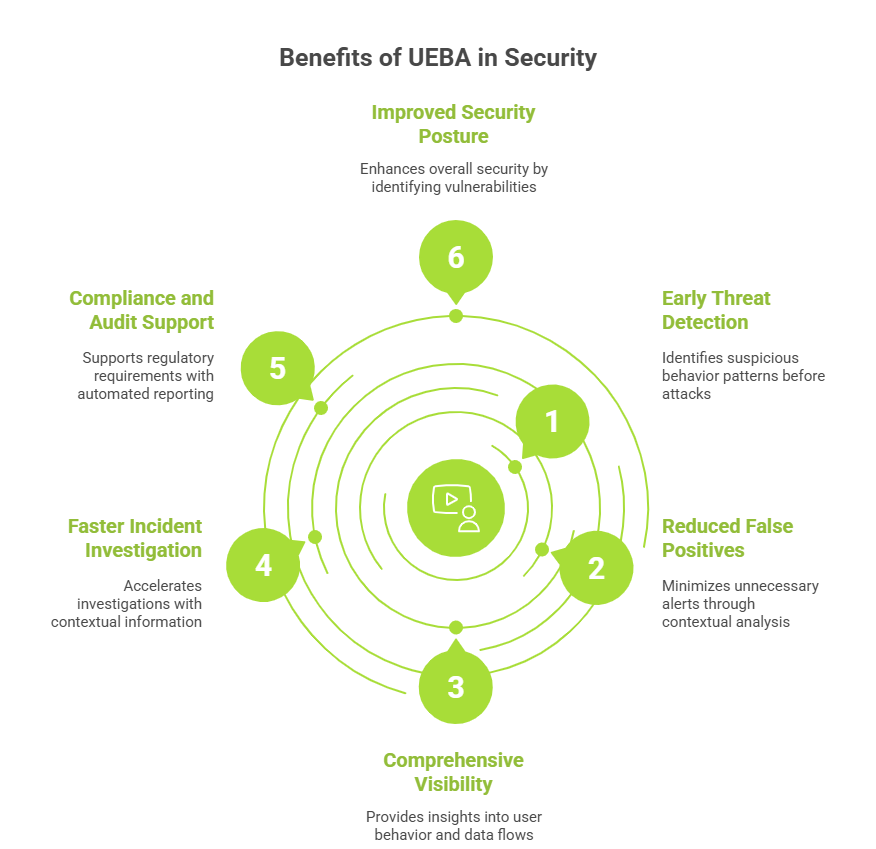
Early Threat Detection: UEBA identifies suspicious behavior patterns that precede actual attacks, providing opportunities for preemptive action. This early detection is particularly valuable for insider threats and APTs, which can remain undetected for extended periods using traditional security approaches.
Reduced False Positives: UEBA dramatically reduces false positives through behavioral approaches and contextual risk scoring. Rather than generating alerts for every anomaly, the system considers context, correlates multiple signals, and focuses on genuinely risky deviations, delivering fewer, higher-quality alerts.
Comprehensive Visibility: UEBA provides unprecedented visibility by aggregating and analyzing data from numerous sources, revealing threats invisible when examining individual systems in isolation. Security teams gain insights into user behavior patterns, entity interactions, data flows, access patterns to sensitive resources, and relationships between seemingly unrelated events.
Faster Incident Investigation: UEBA accelerates investigations by providing rich contextual information about anomalies, clear timelines of suspicious activities, correlation of related events, baseline comparisons, and risk scoring. What might take investigators hours or days to piece together, UEBA presents in minutes through intuitive dashboards.
Compliance and Audit Support: UEBA supports regulatory requirements through automated user activity monitoring and reporting, detailed audit trails, detection of policy violations and unauthorized access, evidence collection for audits, and reporting capabilities for frameworks like GDPR, HIPAA, PCI DSS, and SOX.
Improved Security Posture: Beyond detecting specific threats, UEBA improves overall security by identifying excessive user privileges, applications with unusual access patterns, risky user behaviors requiring training, security gaps being exploited, and trends in security incidents over time.
UEBA vs. SIEM: While SIEM excels at real-time monitoring and detecting known threats through predefined rules, UEBA uses behavioral analytics to detect unknown threats by identifying anomalous behavior. The most effective approach combines both technologies, leveraging SIEM’s comprehensive data collection with UEBA’s behavioral analytics.
UEBA vs. IDS: Traditional intrusion detection systems monitor network traffic for known attack signatures but struggle with insider threats and compromised credentials. UEBA complements IDS by focusing on behavior rather than signatures, detecting threats across all activity types, and identifying threats over extended time periods.
UEBA vs. DLP: Data loss prevention focuses specifically on preventing sensitive data from leaving the organization, while UEBA provides broader behavioral monitoring. UEBA and DLP work best together, with UEBA providing behavioral context and early warning while DLP enforces data protection policies.
Organizations evaluating UEBA solutions should prioritize advanced machine learning capabilities that adapt over time, comprehensive data source integration spanning authentication systems, network devices, endpoints, cloud services, databases, and security platforms, real-time and historical analysis capabilities, intuitive visualization and dashboards, automated response capabilities, customization and tuning options, and scalability to handle growing data volumes and user populations.
UEBA technology continues evolving with several key trends: AI and deep learning advancement enabling detection of increasingly subtle anomalies, integration with Extended Detection and Response platforms for unified threat visibility, incorporation of behavioral biometrics for precise user identification, expansion to IoT and operational technology monitoring, cloud-native architectures for better scalability, and automated investigation and response capabilities.
UEBA investment delivers measurable value through risk reduction by detecting threats earlier and more accurately than traditional tools, efficiency gains reducing investigation time by 40-60%, compliance benefits automating monitoring and reporting requirements, insider threat protection preventing costly incidents, and a competitive advantage through advanced threat detection capabilities and security leadership demonstration.
User and Entity Behavior Analytics has evolved from an emerging technology to a critical component of modern cybersecurity programs. As threats become more sophisticated and traditional tools struggle to keep pace, UEBA provides the intelligence layer that identifies threats other tools miss.
The ability to detect insider threats, compromised accounts, advanced persistent threats, and unknown attack methods makes UEBA invaluable for organizations of all sizes and industries. When integrated with comprehensive security platforms like Seceon, which combines UEBA with SIEM, threat intelligence, and automated response capabilities, organizations gain earlier threat detection, reduced false positives, comprehensive visibility, faster investigation and response, improved compliance posture, and enhanced overall security effectiveness.
These benefits translate directly to reduced risk, lower costs, and stronger security outcomes. The question is no longer whether to implement UEBA, but how quickly organizations can deploy this critical capability to protect against sophisticated threats that traditional security tools cannot detect.
