
In boardrooms across the globe, a compelling narrative dominates enterprise security strategy: consolidate the security stack to reduce complexity, lower costs, and improve operational efficiency. Fewer vendors promise simpler management, cleaner procurement, and a stronger security posture through tighter integration.
On paper, the logic is difficult to challenge.
In practice, however, platform consolidation frequently increases risk rather than reducing it. The disconnect between marketing claims and architectural reality creates a dangerous blind spot-one that becomes most visible during real-world security incidents, when speed, context, and coordination matter most.This is not an argument against consolidation itself. Rather, it is an examination of how consolidation is commonly implemented, why vendor reduction alone fails to improve security, and what true architectural unification actually requires
Over the last decade, the cybersecurity industry has undergone aggressive consolidation. Most major security platforms did not emerge from unified architectural design. They were assembled through serial acquisitions of point solutions across endpoint, network, cloud, identity, and analytics domains.
The acquisition model typically follows a familiar pattern:
This strategy enables rapid portfolio expansion and competitive positioning. What it does not guarantee is architectural consistency.
The result is often a commercially unified platform built on technically fragmented foundations.
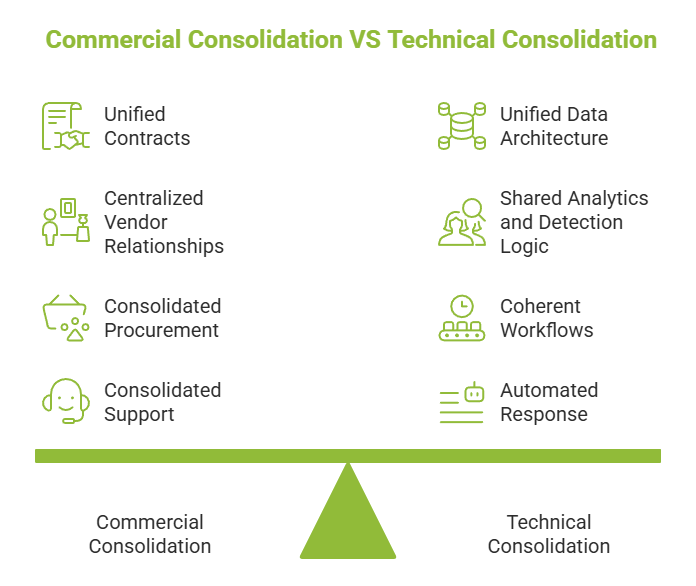
This distinction is where many security strategies break down.
A commercial platform delivers:
A technical platform delivers:
Organizations need both. Too often, they receive only the former while assuming the latter.
In real deployments, “single-platform” customers frequently operate:
Vendor count decreases. Operational and investigative complexity does not.
Data is the foundation of security operations. In a genuinely unified platform, telemetry from all sources flows into a single, normalized data plane.
In acquisition-driven platforms, the reality is different:
This fragmentation makes holistic analysis difficult. Analysts cannot easily trace attacker behavior across domains, and automation lacks the full context needed for confident decisions.
Beyond data storage, analytics remain siloed:
The result is a platform that appears integrated, but behaves like multiple independent security products during detection and investigation.
Consolidation is often expected to reduce infrastructure footprint. In practice, organizations still deploy:
Endpoints become more complex, not less-introducing performance risks and operational overhead that consolidation was meant to eliminate.
The true test of any security platform occurs during an incident.
In multi-stage attacks-such as ransomware or identity-based compromise-organizations expect consolidated platforms to provide:
Instead, they often encounter:
The systems may exchange data through APIs, but lack the deep architectural coupling required for real-time, coordinated defense.
Attackers exploit these seams precisely because they persist beneath consolidated branding.
Consolidation is frequently positioned as a way to gain leverage. In reality, it often creates new dependencies.
Organizations face:
Ironically, integration flexibility often declines after consolidation. Open APIs and third-party interoperability receive less emphasis, reducing an organization’s ability to adopt new capabilities as threats evolve.
Security effectiveness begins to move at vendor speed, not attacker speed.
Real consolidation is not about reducing tool count. It is about unifying intelligence and action.
Anything less preserves fragmentation under a unified brand.
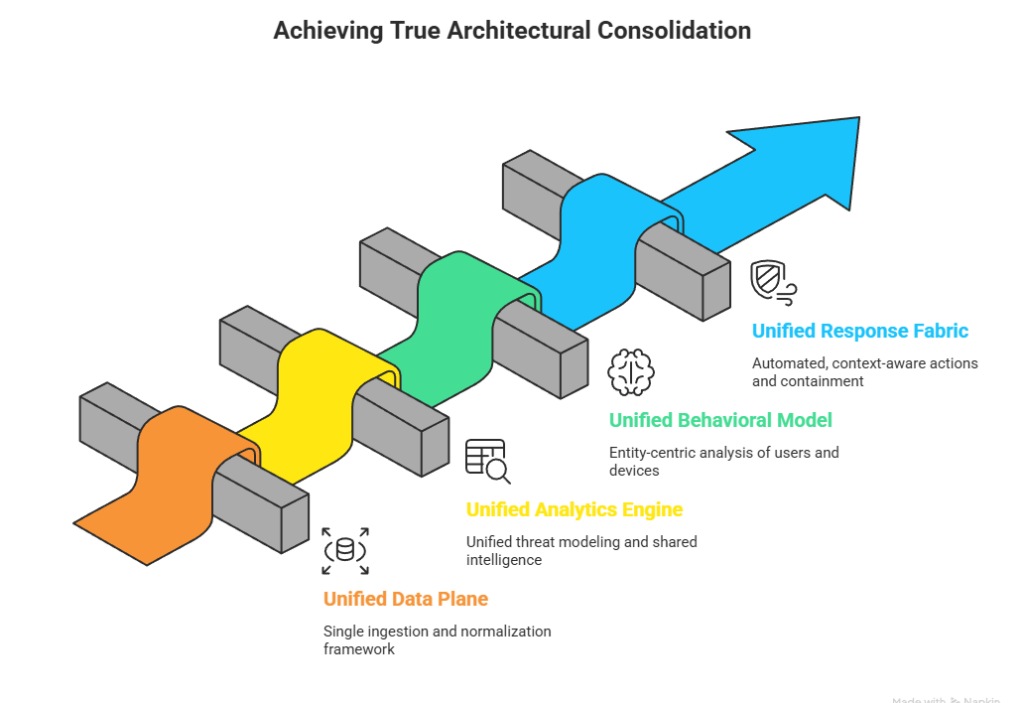
Seceon was built to solve the architectural problems created by acquisition-driven security platforms. Instead of stitching together multiple tools under one brand, Seceon is designed from the ground up as a single, unified security platform.
At its core, Seceon does not treat endpoint, network, cloud, identity, and application security as separate products. It treats them as different signal sources feeding one shared intelligence fabric.
Seceon collects and processes security data from across the enterprise into one normalized data plane. This provides:
As a result, analysts can investigate complex threats using a single query, instead of manually stitching data together from multiple tools.
Many platforms use separate analytics engines for each module. Seceon uses one analytics engine across the entire environment.
This engine:
This enables earlier detection of multi-stage and identity-driven attacks that siloed tools often miss.
Seceon takes an entity-centric approach, continuously tracking behavior across:
This allows Seceon to:
Security teams shift from reactive alert handling to behavior-driven threat detection.
Seceon extends unification beyond detection into coordinated response.
The platform enables:
Instead of isolated reactions, Seceon delivers synchronized, intelligence-driven response, reducing dwell time and limiting attack impact.
Most importantly, Seceon was built as a unified platform from day one, not assembled later through acquisitions. This removes:
The result is true platform consolidation-not just fewer vendors, but fewer failure points and better security outcomes.

Platform consolidation will continue to shape enterprise security strategies, driven by legitimate economic and operational pressures. However, many acquisition-driven platforms replace tool sprawl with hidden architectural complexity, failing to deliver meaningful security gains.
Reducing vendor logos does not reduce attack surfaces or operational risk.
Only architectural coherence does.True consolidation means one data plane, one analytics engine, one behavioral model, and one response fabric. Security leaders who understand this distinction will build platforms that deliver simpler operations, lower costs, and genuinely stronger security outcomes-not just the appearance of consolidation.
