
The traditional perimeter-based security model has become obsolete in today’s distributed digital environment. With 82% of organizations now operating in hybrid or multi-cloud infrastructures and remote work becoming the standard, the concept of a secure network boundary no longer exists. Zero Trust AI Security represents the evolution of cybersecurity strategy-combining the principles of zero trust architecture with artificial intelligence to create adaptive, intelligent security frameworks that protect organizations in 2026’s complex threat landscape.
Zero Trust AI Security integrates two transformative approaches to cybersecurity: the zero trust security model and artificial intelligence-driven threat detection and response. This combination creates a dynamic security posture that continuously validates, monitors, and adapts to emerging threats.
The foundational principle of zero trust is simple yet powerful: “Never trust, always verify.” Unlike traditional security models that assume internal network traffic is trustworthy, zero trust treats every access request as potentially hostile, regardless of origin. When enhanced with artificial intelligence, this model becomes exponentially more effective, utilizing machine learning algorithms to identify patterns, predict threats, and automate responses at speeds impossible for human security teams.
In 2026, organizations implementing Zero Trust AI Security reported 76% fewer successful breaches and reduced incident response times from days to minutes, demonstrating the tangible business value of this approach.
The cybersecurity landscape continues to evolve at an unprecedented pace, requiring organizations to fundamentally rethink their security strategies:
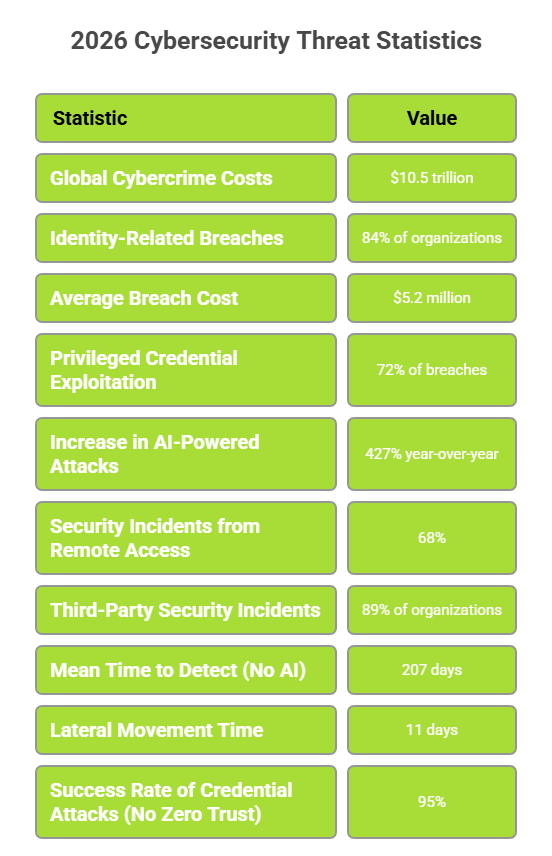
Understanding the magnitude of today’s security challenges provides context for why Zero Trust AI Security has become essential:
95% success rate: Credential-based attacks against organizations lacking zero trust controls
Digital Transformation Requirements: Cloud migration, SaaS application adoption, and hybrid infrastructure models eliminate traditional network boundaries, making perimeter-based security ineffective.
Regulatory Compliance: Frameworks, including GDPR, HIPAA, PCI-DSS, SOC 2, and the new Federal Zero Trust Architecture mandate require organizations to implement zero trust principles and demonstrate continuous verification capabilities.
Remote Workforce Security: With 58% of employees working in hybrid or fully remote environments, organizations must secure access from any location while maintaining productivity and user experience.
Third-Party Risk Management: Modern business operations rely on extensive partner ecosystems, requiring granular access controls and continuous monitoring of third-party connections.Insider Threat Mitigation: Malicious and negligent insider actions account for 34% of security incidents, costing organizations an average of $16.2 million per incident.
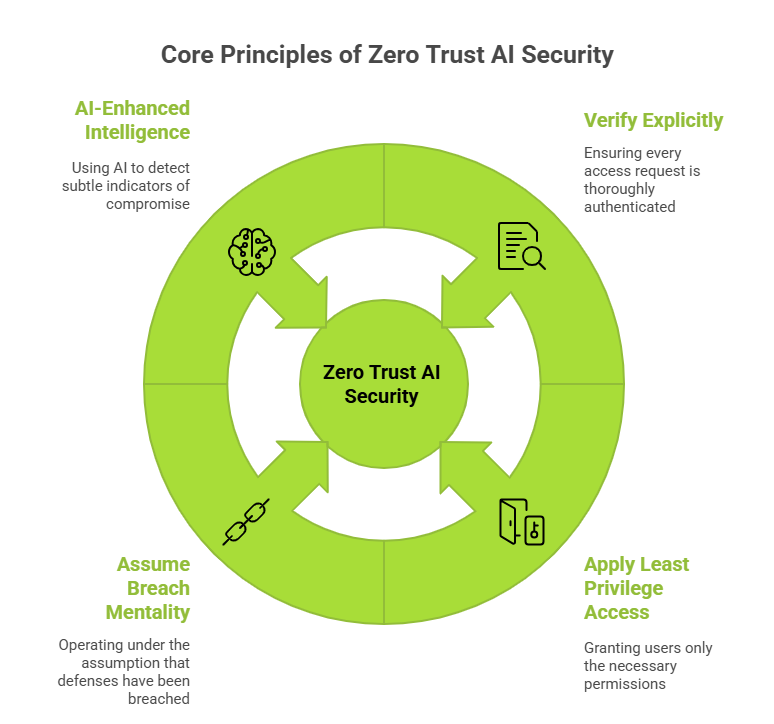
Effective implementation of Zero Trust AI Security requires understanding and applying fundamental principles that form the foundation of this security model:
Every access request undergoes comprehensive authentication and authorization processes utilizing multiple data points:
Organizations implement granular access controls that provide users with only the minimum permissions required for their specific roles:
Security architectures operate under the assumption that threats have already penetrated defenses, requiring continuous monitoring and rapid response:
Artificial intelligence amplifies zero trust effectiveness by processing vast datasets and identifying subtle indicators of compromise:
Machine learning algorithms are improving detection accuracy through continuous learning
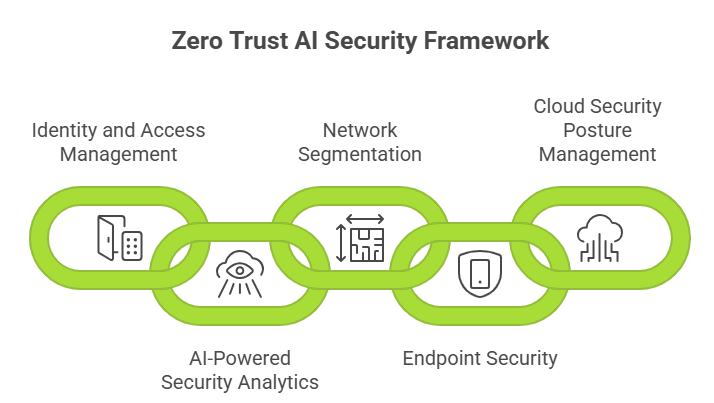
Implementing comprehensive Zero Trust AI Security requires integrating multiple technology components into a cohesive security framework:
Modern IAM solutions serve as the foundation of zero trust, managing digital identities and controlling access across all systems:
Artificial intelligence processes security data at scale, identifying threats that traditional systems miss:
Dividing networks into smaller, isolated segments limits attacker movement and contains potential breaches:
Comprehensive endpoint protection ensures device security regardless of location:
Organizations require specialized tools for securing cloud infrastructure and services:
Infrastructure as code (IaC) scanning and detecting security issues in deployment templates
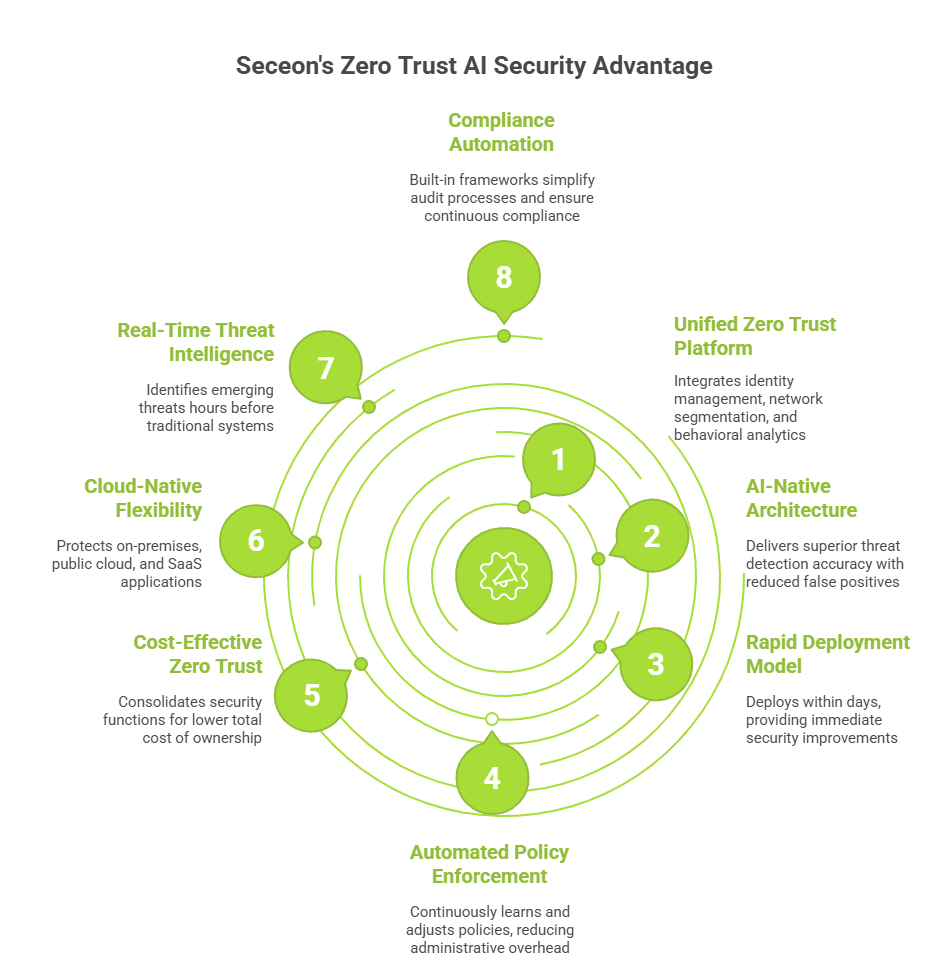
Organizations evaluating Zero Trust AI Security solutions require platforms that combine comprehensive functionality, ease of deployment, and proven effectiveness. Seceon’s aiSIEM platform delivers enterprise-grade zero trust capabilities enhanced by advanced artificial intelligence.
Unified Zero Trust Platform: Seceon integrates identity management, network segmentation, behavioral analytics, and automated response in a single, cohesive solution. Organizations eliminate the complexity and cost of managing multiple disparate security tools.
AI-Native Architecture: Built from inception with artificial intelligence at its core, Seceon’s platform delivers superior threat detection accuracy exceeding 99.3% while reducing false positives by 92% compared to traditional SIEM solutions.
Rapid Deployment Model: Unlike complex zero trust implementations requiring 12-18 months, Seceon deploys within days, providing immediate security improvements. Organizations achieve full operational capability within 30-60 days.
Automated Policy Enforcement: Seceon’s AI continuously learns organizational patterns and automatically suggests or implements policy adjustments, reducing administrative overhead by 67%.
Cost-Effective Zero Trust: By consolidating multiple security functions, Seceon delivers comprehensive zero trust protection at 60% lower total cost of ownership compared to building equivalent capabilities with point solutions.
Cloud-Native Flexibility: Designed for modern hybrid and multi-cloud environments, Seceon seamlessly protects on-premises infrastructure, public cloud workloads, and SaaS applications through a unified policy framework.
Real-Time Threat Intelligence: Seceon integrates global threat intelligence feeds with proprietary AI analysis, identifying emerging threats an average of 47 hours before traditional signature-based systems.Compliance Automation: Built-in compliance frameworks for GDPR, HIPAA, PCI-DSS, SOC 2, and zero trust architecture mandates simplify audit processes and ensure continuous compliance.
Organizations must establish clear metrics to evaluate Zero Trust AI Security effectiveness and demonstrate return on investment:
Organizations implementing Zero Trust AI Security should follow proven practices to maximize effectiveness and minimize implementation challenges:
Executive Sponsorship: Secure C-level commitment and adequate budget allocation. Zero trust represents a strategic initiative requiring organizational transformation beyond technology deployment.
User-Centric Design: Balance security requirements with user experience. Implementations causing excessive friction result in shadow IT and workarounds that undermine security objectives.
Incremental Implementation: Adopt a phased approach focusing on highest-risk areas first. Organizations attempting comprehensive overnight transitions typically experience implementation failures and user resistance.
Continuous Education: Invest in ongoing security awareness training. Zero trust effectiveness depends on user understanding and cooperation with new access procedures.
Regular Assessment: Conduct quarterly reviews of access policies, detection rules, and security effectiveness. Threat landscapes evolve continuously, requiring corresponding security adjustments.
Integration Planning: Ensure zero trust solutions integrate seamlessly with existing security infrastructure. Siloed implementations create visibility gaps and increase operational complexity.
Performance Monitoring: Establish comprehensive metrics tracking both security effectiveness and operational impact. Data-driven insights enable continuous improvement and demonstrate business value.
Organizations cannot afford to delay zero-trust implementation. Each day without comprehensive zero trust controls increases exposure to credential theft, lateral movement attacks, and data breaches that average $5.2 million in costs.
Seceon’s zero trust specialists provide comprehensive evaluations helping organizations understand their current security posture and develop strategic implementation roadmaps. Our assessment includes:
Organizations across healthcare, financial services, manufacturing, retail, and government sectors trust Seceon for Zero Trust AI Security. Customers report:
$3.2 million average annual savings from prevented incidents

The cybersecurity paradigm has fundamentally shifted. Perimeter-based security models cannot protect organizations operating in distributed, cloud-centric environments with remote workforces and extensive partner ecosystems. Zero Trust AI Security provides the comprehensive, adaptive protection modern enterprises require.
Organizations implementing zero trust architectures enhanced with artificial intelligence achieve measurably superior security outcomes-experiencing 76% fewer successful breaches while reducing operational costs through automation and intelligent policy enforcement. With average breach costs exceeding $5.2 million and regulatory penalties reaching eight figures, the business case for zero trust implementation is compelling.
When evaluating Zero Trust AI Security solutions, prioritize platforms offering unified architecture, AI-native design, rapid deployment capabilities, and proven effectiveness. Seceon delivers enterprise-grade zero trust protection accessible to organizations of all sizes, combining advanced technology with operational simplicity.
Your organization’s security resilience, regulatory compliance, and competitive positioning depend on implementing modern security architectures designed for today’s threat landscape. Zero Trust AI Security represents the foundation for secure digital operations in 2026 and beyond.
