
Cyber Threat Intelligence (CTI) has become a foundational capability in today’s hyperconnected digital ecosystem, where cyber threats are no longer isolated or episodic. Modern adversaries leverage automation, advanced persistent tactics, ransomware-as-a-service (RaaS), nation-state resources, and supply-chain exploitation to conduct continuous and highly adaptive attacks. This escalating volume, velocity, and sophistication of threats has elevated CTI from an auxiliary security function to a mission-critical component of proactive cybersecurity operations and enterprise risk management.
At its core, cyber threat intelligence transforms raw security data into actionable insights that help organizations anticipate, prevent, detect, and respond to cyberattacks. When powered by AI, Machine Learning (ML), and Data-Threat Modeling (DTM), CTI becomes a force multiplier—enabling proactive defense instead of reactive firefighting.
This in-depth guide explores cyber threat intelligence in detail: what it is, why it matters, how it works, and how modern AI-driven platforms like Seceon are redefining CTI for enterprises, MSSPs, and critical infrastructure worldwide.
Cyber Threat Intelligence is the collection, analysis, and contextualization of information about existing and emerging cyber threats. The goal is not just awareness, but decision-ready intelligence that security teams can act on immediately.
CTI answers critical questions such as:
Unlike basic threat feeds that flood teams with indicators of compromise (IOCs), mature CTI focuses on relevance, accuracy, and timeliness.
The modern threat landscape is shaped by several converging trends:
Cloud adoption, remote work, IoT, OT, and SaaS applications have dramatically expanded enterprise attack surfaces.
Adversaries now use automation and AI to launch faster, stealthier, and more targeted campaigns.
Security teams are overwhelmed, under-resourced, and drowning in alerts.
Data breaches bring regulatory penalties, reputational damage, and financial loss.
Cyber threat intelligence addresses all of these challenges by prioritizing threats, reducing noise, and enabling faster, smarter responses.
CTI is typically categorized into four layers, each serving different stakeholders.
An effective CTI program integrates all four layers into a unified intelligence workflow.
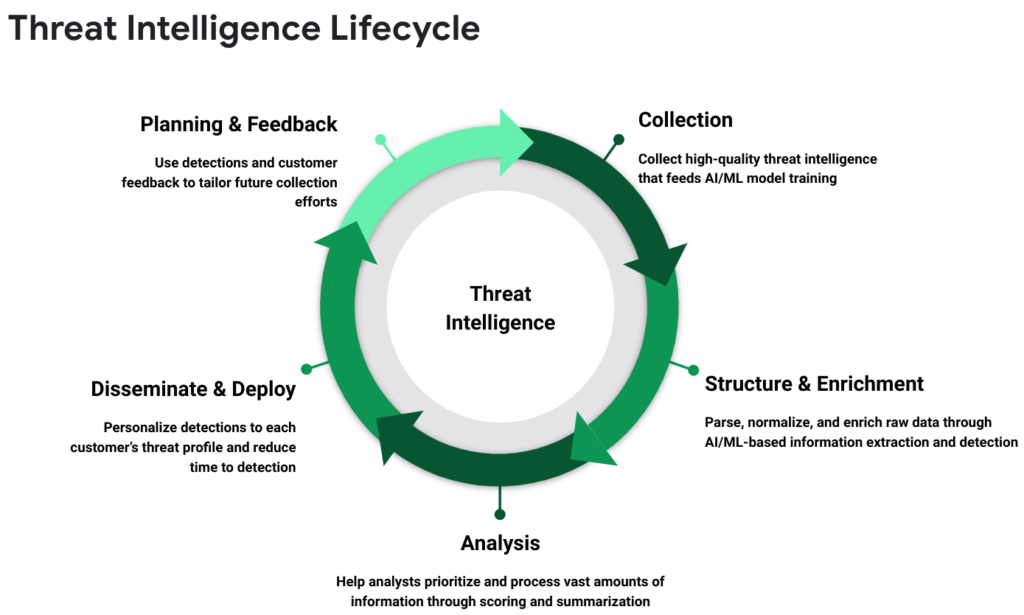
The CTI lifecycle ensures intelligence remains relevant and actionable:
Traditional tools struggle to keep up with this lifecycle due to data volume and velocity. This is where AI-driven platforms excel.
Modern CTI platforms ingest petabytes of security telemetry—logs, network flows, endpoints, cloud activity, emails, and more. AI and ML enable:
DTM maps threats to actual business assets, users, and data flows. Instead of asking “Is this malicious?”, DTM asks:
“Is this malicious for us, right now?”
This approach dramatically reduces false positives and ensures security teams focus on what truly matters.
| Traditional Security | Cyber Threat Intelligence |
|---|---|
| Reactive | Proactive & predictive |
| Siloed tools | Unified intelligence |
| Rule-based detection | AI-driven behavioral analysis |
| Alert overload | Prioritized, contextual insights |
| Slow response | Automated, rapid response |
CTI does not replace security tools—it supercharges them.
CTI enables teams to hunt for adversaries before alerts fire, using known attacker behaviors and indicators.
Contextual intelligence shortens Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Not all vulnerabilities are equal. CTI highlights which vulnerabilities are actively exploited in the wild.
Behavioral intelligence uncovers suspicious user actions and account misuse.
Demonstrates due diligence and continuous monitoring for regulatory requirements.
Despite its benefits, many organizations struggle with CTI due to:
These challenges have driven demand for fully integrated, AI-native CTI platforms.
How Seceon Redefines Cyber Threat Intelligence
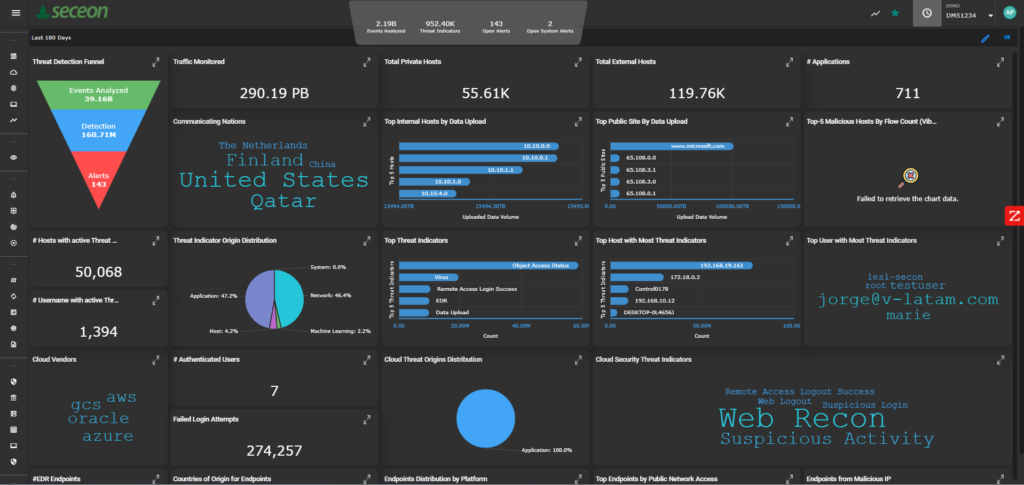
Seceon delivers a next-generation approach to cyber threat intelligence through its AI-powered aiXDR and aiSIEM platforms, designed for enterprises and Managed Security Service Providers (MSSPs).
Seceon ingests telemetry across:
All data is correlated in real time using advanced AI/ML and DTM, producing high-fidelity threat intelligence.
For enterprises, CTI provides visibility, risk reduction, and faster response across complex environments.
For MSSPs, CTI is the backbone of profitable, scalable security services:
Seceon’s platforms are specifically engineered to address top MSSP pain points while delivering enterprise-grade intelligence.
The future of CTI is shaped by:
Organizations that invest in AI-powered CTI today will define the security leaders of tomorrow.
To succeed with CTI:
Platforms like Seceon aiXDR and aiSIEM accelerate this journey by delivering end-to-end cyber threat intelligence out of the box.
Cyber threat intelligence is no longer just about defense—it’s about resilience, trust, and business continuity. In a world where cyberattacks are inevitable, intelligence determines who reacts too late and who stays ahead.
By combining AI, ML, and Data-Threat Modeling, modern CTI platforms empower organizations to move from reactive security to predictive, autonomous defense.
For enterprises and MSSPs seeking a future-ready cybersecurity strategy, Seceon stands at the forefront—delivering intelligent, scalable, and actionable cyber threat intelligence for the digital age.
